TAMUctf 2022
Writeup for the TAMUctf 2022
Updated:
Forensics
Plain
100 points 274 solves
Someone logged into my computer and stole my flag. Can you get it back for me?
Attachment:
plain.pcap
Basic check with strings revealed a Base64 string Z2lnZW17ZDBudF91czNfdDNsbmV0X2V2M3J9Cg==, which was decoded using CyberChef and obtained the flag.
└─$ strings plain.pcap
...
Z2lnZW17ZDBudF91czNfdDNsbmV0X2V2M3J9Cg==
@{Pb="
@{Pb
]0;tacex@ubuntu: /tmp/flag
Flag: gigem{d0nt_us3_t3lnet_ev3r}
What’s the Difference
100 points 176 solves
I made a mistake while making a writeup for a challenge from MetaCTF 2021. Can you find it?
Attachment: whats-the-difference.zip
Extracted the file and revealed a git folder.
└─$ unzip whats-the-difference.zip
Archive: whats-the-difference.zip
inflating: README.md
creating: .git/
creating: .git/branches/
inflating: .git/COMMIT_EDITMSG
Checked the log with git log and revealed that the first commit contained the wrong flag, which is likely to be the flag for this challenge.
└─$ git log
commit 0b055455560bce16787d2e2a7b0ae36b3ddd2b35 (HEAD -> master)
Author: TacEx <TacEx@root.dev>
Date: Fri Apr 8 02:14:25 2022 -0500
Whoops wrong flag
commit e61bf8b90c60b29a241bd29205eb173ef79cd850
Author: TacEx <TacEx@root.dev>
Date: Fri Apr 8 02:13:54 2022 -0500
Add writeup
Checked the difference between the commits with git diff and the flag was revealed.
└─$ git diff e61bf8b90c60b29a241bd29205eb173ef79cd850 0b055455560bce16787d2e2a7b0ae36b3ddd2b35
diff --git a/README.md b/README.md
index 95fb13e..f22d0cb 100644
--- a/README.md
+++ b/README.md
@@ -70,4 +70,4 @@ for i in range(25):
break
-Flag: gigem{b3_car3ful_b3for3_y0u_c0mmit}
+Flag: MetaCTF{yOu_w!N_th1$_0n3}
Flag: gigem{b3_car3ful_b3for3_y0u_c0mmit}
Taxes
100 points 118 solves
Thank you for completing your 2021 taxes with Another Data Harvester!
We’ve sent you your 2021 tax return. For your safety and privacy, we’ve delivered the document as encrypted with your Social Security Number, with no dashes.
We hope you have a pleasant 2022. Make sure to file with us next year so we canharvest your data furtherhelp you with your taxes again!
Note: The Social Security Number in question is a United States Social Security Number.Attachment:
2021-return-enc.pdf
Since the US SNN is a 9 digit number, the password for the encrypted PDF was bruteforced using john and revealed to be 694705124.
└─$ pdf2john 2021-return-enc.pdf > taxes.john
└─$ john -mask=?d?d?d?d?d?d?d?d?d taxes.john
Created directory: /home/kali/.john
Using default input encoding: UTF-8
Loaded 1 password hash (PDF [MD5 SHA2 RC4/AES 32/64])
Cost 1 (revision) is 3 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
694705124 (2021-return-enc.pdf)
1g 0:01:37:17 DONE (2022-04-16 05:42) 0.000171g/s 123447p/s 123447c/s 123447C/s 128705124..844705124
Use the "--show --format=PDF" options to display all of the cracked passwords reliably
Session completed.
The file was then decrypted and the flag was found within.
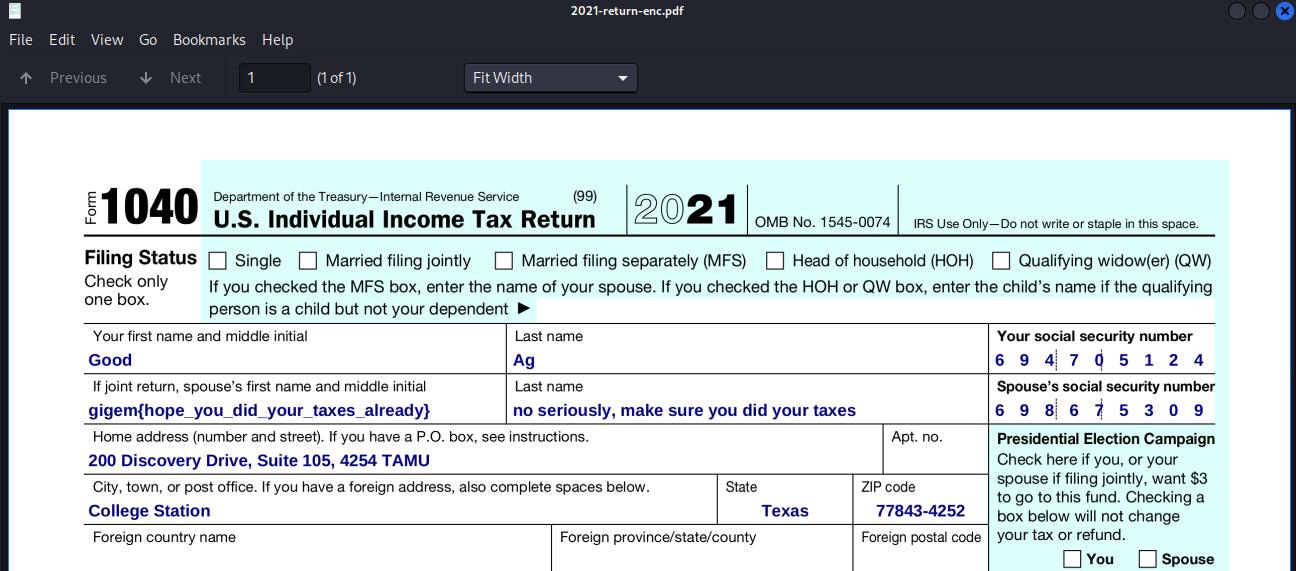
Flag: gigem{hope_you_did_your_taxes_already}
Web
Triplet
100 points 404 solves
This website looks like it was made for the Netscape and AOL era, but there is a flag somewhere in there. Find it and get the points.
Do not connect with HTTPS, make sure to connect with HTTP
Link: http://triplet.tamuctf.com
The first part of the flag was found at the bottom in the base html file.
</body>
<!--
gigem{ThReE_PaRtS
-->
</html>
The second part of the flag was found within style.css.
button {
cursor: pointer;
background-color: #FFCAD4;
border: none;
padding: 12px 28px;
}
/* _tO_wEb_HTML_CSS_ */
The third and last part of the flag was found within script.js.
function doTheStuff() {
alert("HOWDY THERE!");
}
// AND_JS_0xCHICKEN}
Flag: gigem{ThReE_PaRtS_tO_wEb_HTML_CSS_AND_JS_0xCHICKEN}
Lock Out
100 points 160 solves
I seem to have locked myself out of my admin panel! Can you find a way back in for me?
Do not connect with HTTPS, make sure to connect with HTTP
Link: http://lockout.tamuctf.com
The network packets revealed that the login form POST the login information to admin.php, which has a 302 redirection back to login.php.
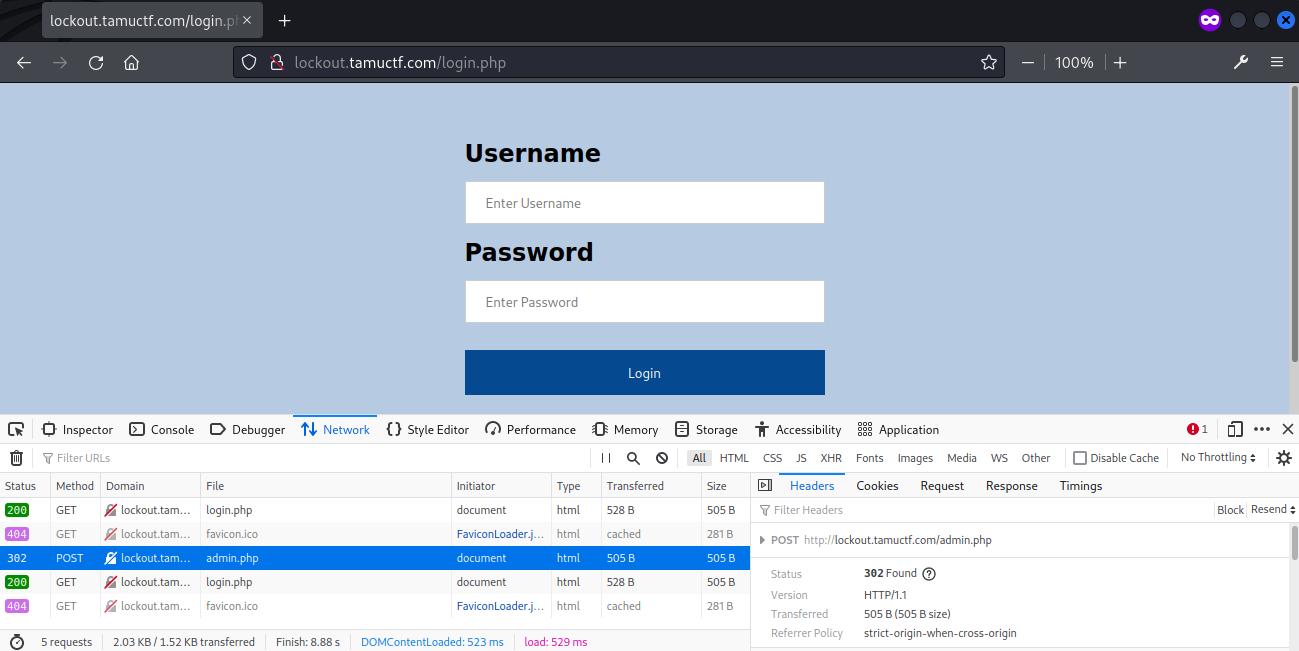
The easiest way to prevent redirection is to use curl, which revealed a form at the admin.php page containing a single input PrintFlag.
└─$ curl http://lockout.tamuctf.com/admin.php
<!DOCTYPE html>
<head>
<link rel="stylesheet" href="/static/admin.css">
</head>
<body>
<h1>Industry Night Shopping List</h1>
<p>Croc Martins</p>
<img src="static/crocmartins.jpg" alt="Croc-Martins">
<form action="admin.php" method="get">
<input type="submit" name="PrintFlag" value="PrintFlag">
</form>
</body>
The parameter PrintFlag was then given as GET /admin.php?PrintFlag and the flag was returned.
└─$ curl http://lockout.tamuctf.com/admin.php?PrintFlag
<p>gigem{if_i_cant_wear_croc_martins_to_industry_night_then_im_not_going}</p>
<!DOCTYPE html>
...
Flag: gigem{if_i_cant_wear_croc_martins_to_industry_night_then_im_not_going}
Serial Killer
100 points 99 solves
I’m tryinig a new way to display files on my website. Can you try to break it for me?
Do not connect with HTTPS, make sure to connect with HTTP
Link: http://serial.tamuctf.com
Tip: The flag is located in the/etc/passwdfile.
A PHPSESSID cookie was found and seemed to be encoded in Base64.
PHPSESSID=Tzo3OiJHZXRQYWdlIjoxOntzOjQ6ImZpbGUiO3M6MTA6ImluZGV4Lmh0bWwiO30%3D
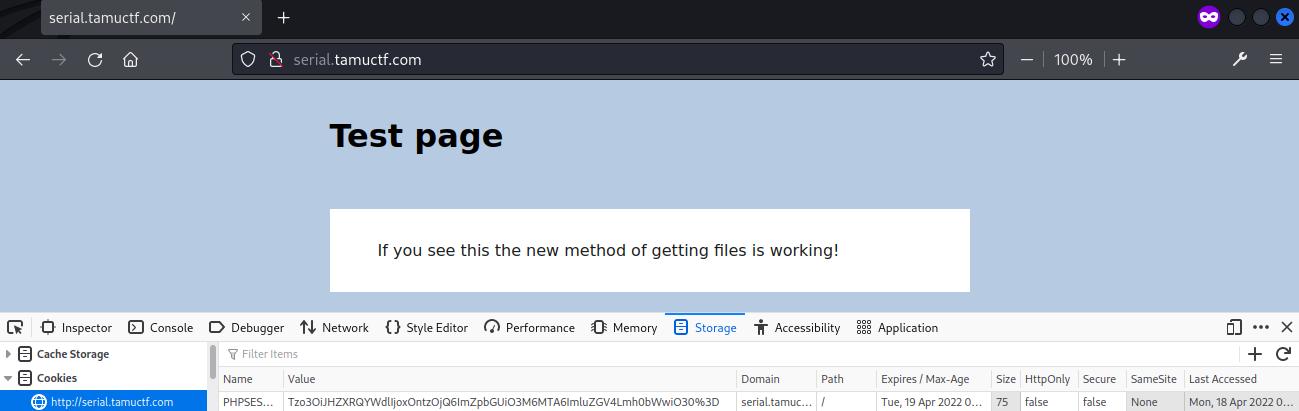
The cookie value was then decoded as Base64 using CyberChef and revealed that the file to be returned by the page index.html is included in the cookie, preceded by the number of characters of the file name s:10.
// encoded cookie
Tzo3OiJHZXRQYWdlIjoxOntzOjQ6ImZpbGUiO3M6MTA6ImluZGV4Lmh0bWwiO30=
// decoded cookie
O:7:"GetPage":1:{s:4:"file";s:10:"index.html";}
As the flag is located at /etc/passwd, the file name was changed in the cookie and encoded back as Base64 using CyberChef.
// plain text
O:7:"GetPage":1:{s:4:"file";s:11:"/etc/passwd";}
// Base64 encoded
Tzo3OiJHZXRQYWdlIjoxOntzOjQ6ImZpbGUiO3M6MTE6Ii9ldGMvcGFzc3dkIjt9
The cookie was updated at the page and an error message was returned, revealed the current directory as /var/www/html/.
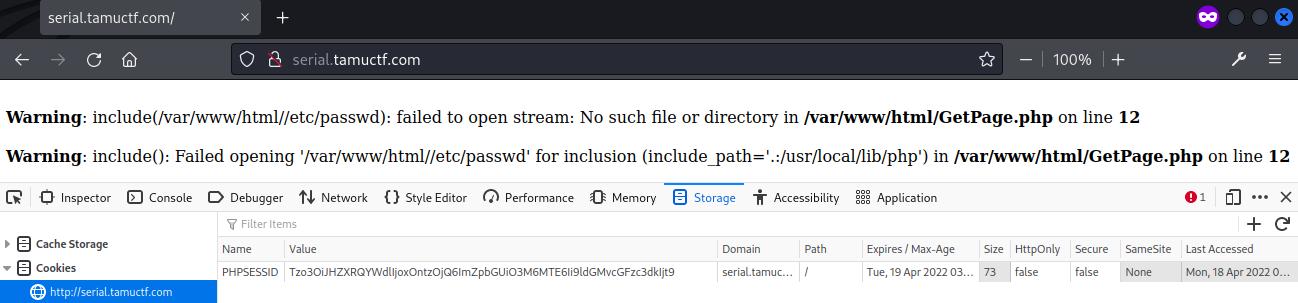
The file name was then changed to ../../../etc/passwd and encoded as Base64 using CyberChef.
// plain text
O:7:"GetPage":1:{s:4:"file";s:19:"../../../etc/passwd";}
// Base64 encoded
Tzo3OiJHZXRQYWdlIjoxOntzOjQ6ImZpbGUiO3M6MTk6Ii4uLy4uLy4uL2V0Yy9wYXNzd2QiO30=
The cookie was updated at the page and another error message was returned, seems like the input was forbidden by the admin.
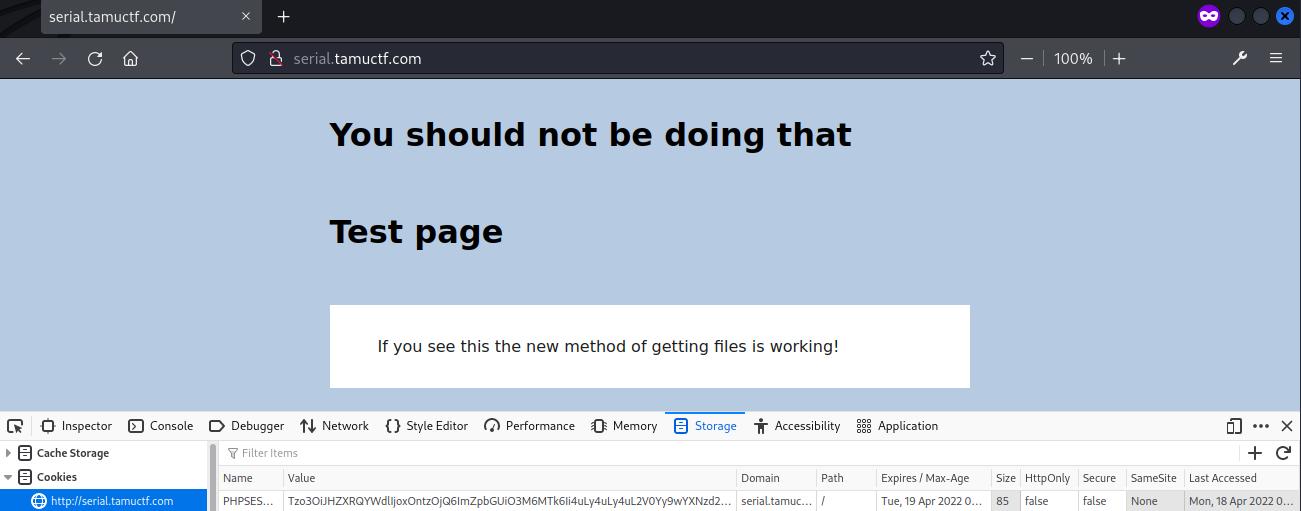
All slashes / was replaced by %2f to escape the input checking. The cookie was encoded as Base64 using CyberChef.
// plain text
O:7:"GetPage":1:{s:4:"file";s:27:"..%2f..%2f..%2fetc%2fpasswd";}
// Base64 encoded
Tzo3OiJHZXRQYWdlIjoxOntzOjQ6ImZpbGUiO3M6Mjc6Ii4uJTJmLi4lMmYuLiUyZmV0YyUyZnBhc3N3ZCI7fQ==
The cookie was updated at the page and the file /etc/passwd was returned successfully, with the flag found at the end of the file.
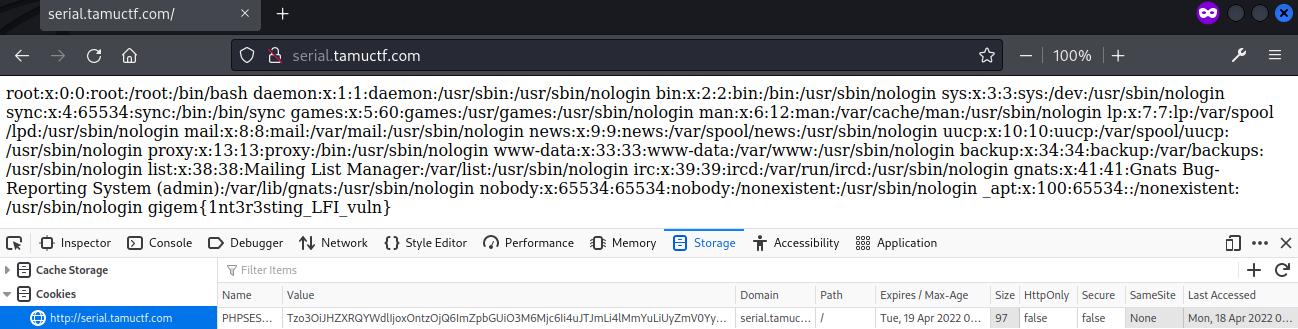
Flag: gigem{1nt3r3sting_LFI_vuln}
Misc
Gamer
100 points 105 solves
I was vibing in VC with my gamer friends when I stumbled across a mysterious in-game inscription. Can you figure out what it means?
Flag format is case-insensitive.Attachment:
sus.txtsummon bat ~ ~69 ~ {Silent:1b,Invulnerable:1b,Passengers:[{id:":chest_minecart",CustomNameVisible:1b,CustomName:'[{"text":"_","color":"gold","bold":true,"obfuscated":true},{"text":"FLAG","color":"dark_red","bold":true,"obfuscated":false},{"text":"_","color":"gold","bold":true}]',Items:[{Slot:0b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"hh",Color:14},{Pattern:"bs",Color:0},{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:1b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"cs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:2b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"hh",Color:14},{Pattern:"bs",Color:0},{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:3b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"ms",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:4b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"tt",Color:0},{Pattern:"tts",Color:14},{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:5b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ms",Color:0},{Pattern:"rs",Color:14},{Pattern:"ts",Color:0},{Pattern:"ls",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:6b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"tt",Color:0},{Pattern:"tts",Color:14},{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:7b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"cs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:8b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"tt",Color:14},{Pattern:"drs",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:9b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"ms",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:10b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"bs",Color:0}],Base:14}}},{Slot:11b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"ts",Color:0},{Pattern:"cbo",Color:14},{Pattern:"ls",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:12b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"cs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:13b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"ls",Color:0},{Pattern:"ms",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:14b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"tt",Color:0},{Pattern:"tts",Color:14},{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:15b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:16b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"tt",Color:14},{Pattern:"drs",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:17b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"ts",Color:0},{Pattern:"cbo",Color:14},{Pattern:"ls",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:18b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ts",Color:0},{Pattern:"dls",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}}},{Slot:19b,id:"red_banner",Count:1b,tag:{BlockEntityTag:{Patterns:[{Pattern:"ms",Color:0},{Pattern:"ls",Color:14},{Pattern:"ts",Color:0},{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}],Base:14}}}]}],ActiveEffects:[{Id:11b,Amplifier:255b,Duration:20000000,ShowParticles:0b},{Id:14b,Amplifier:1b,Duration:20000000,ShowParticles:0b}]}
Google searched with the keyword “summon bat” and revealed that the text is a game command in Minecraft.
The command looked like it creates a chest, which has the flag that is composed by a number of banners written in json. Each of the banner json starting with BlockEntityTag was extracted out.
BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"hh",Color:14},{Pattern:"bs",Color:0},{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"cs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"hh",Color:14},{Pattern:"bs",Color:0},{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"ms",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"tt",Color:0},{Pattern:"tts",Color:14},{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ms",Color:0},{Pattern:"rs",Color:14},{Pattern:"ts",Color:0},{Pattern:"ls",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"tt",Color:0},{Pattern:"tts",Color:14},{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"cs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"tt",Color:14},{Pattern:"drs",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"ts",Color:0},{Pattern:"ms",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"bs",Color:0}],Base:14}
BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"ts",Color:0},{Pattern:"cbo",Color:14},{Pattern:"ls",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"cs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"ls",Color:0},{Pattern:"ms",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"tt",Color:0},{Pattern:"tts",Color:14},{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"ts",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ls",Color:0},{Pattern:"tt",Color:14},{Pattern:"drs",Color:0},{Pattern:"rs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"ts",Color:0},{Pattern:"cbo",Color:14},{Pattern:"ls",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ts",Color:0},{Pattern:"dls",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}]}
BlockEntityTag:{Patterns:[{Pattern:"ms",Color:0},{Pattern:"ls",Color:14},{Pattern:"ts",Color:0},{Pattern:"rs",Color:0},{Pattern:"bs",Color:0},{Pattern:"bo",Color:14}],Base:14}
The banner editor at https://www.needcoolshoes.com/banner was used to import the json to reveal how each of the individual banner looks like and hence obtained the flag.
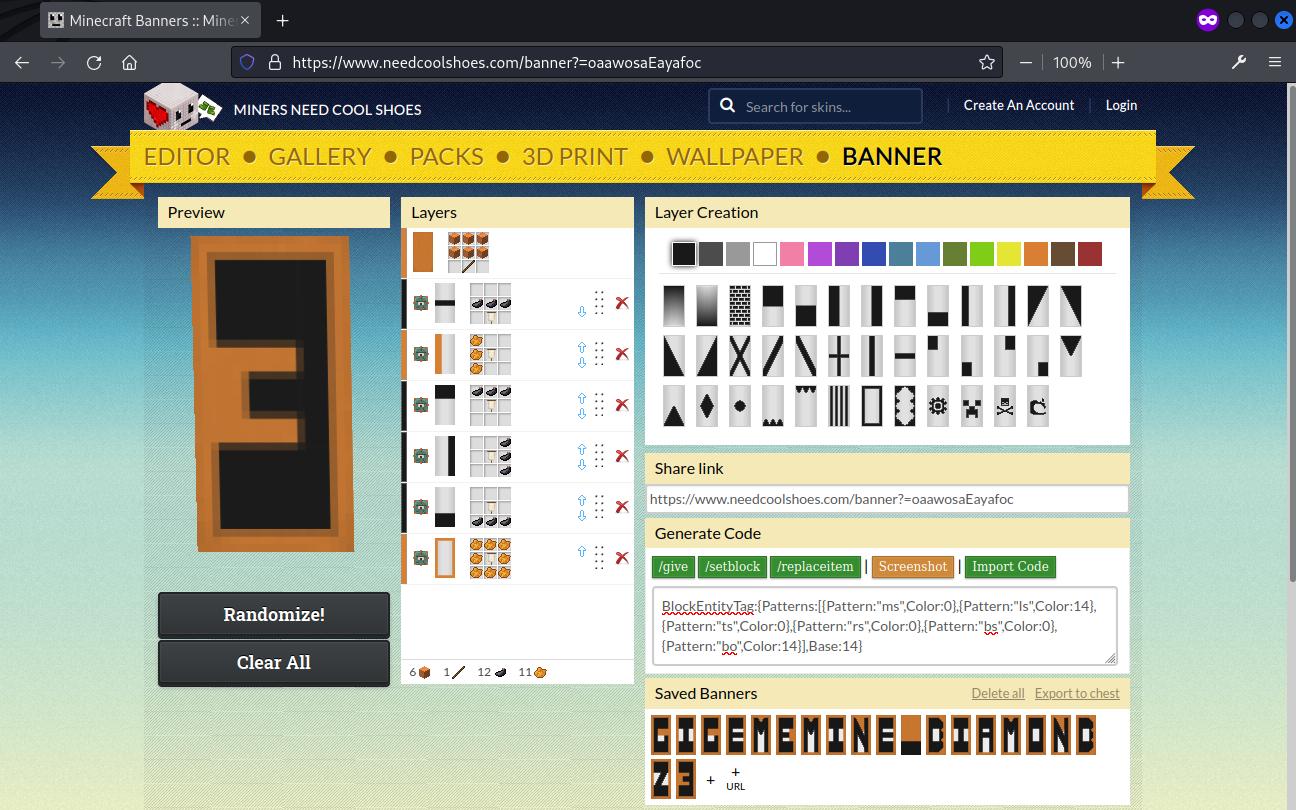
Flag: GIGEM{MINE_DIAMONDZ}
Hear Me Out
100 points 185 solves
You overheard some suspicious people typing on their phones, what are they saying?
The flag format isgigem{messagewithoutspace}, case-insensitive.Attachment:
hear-me-out.mp3
The file contained dial tones and it was uploaded to https://unframework.github.io/dtmf-detect/#/ to decode the tones as 444 222 2 66 8 44 33 2 777 88.
The message is likely to be typed on the phone keypad with 444 being i, which the whole message was decoded using https://www.dcode.fr/multitap-abc-cipher as icanthearu.
Flag: gigem{icanthearu}
Gilberto’s Brother
100 points 90 solves
We are trying to find information on Gilberto’s brother. We managed to get Gilberto to send us a screenshot of his screen by asking him to recommend us a pirating movie. Can you find the name of the company Gilberto’s brother is interning for and the difference of the the brother’s birthday by days?
Flag Format:gigem{company_name_days}(replace any space with_)Attachment:
screenshot.png
At the upper left corner, there is a tab at Twitter hinting that Gilberto should have an Twitter account. There is also a bookmark folder named “Georcia Family Photos” that “Georcia” should be the brothers’ last name.
Searched for “gilberto georcia” at Twitter and found accounts for both Gilberto and his brother, Gerardo.
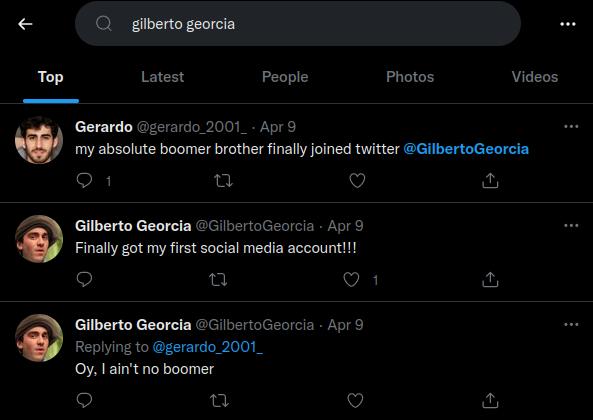
First for Gilberto, his birthday is found to be 20 Nov, 1994.
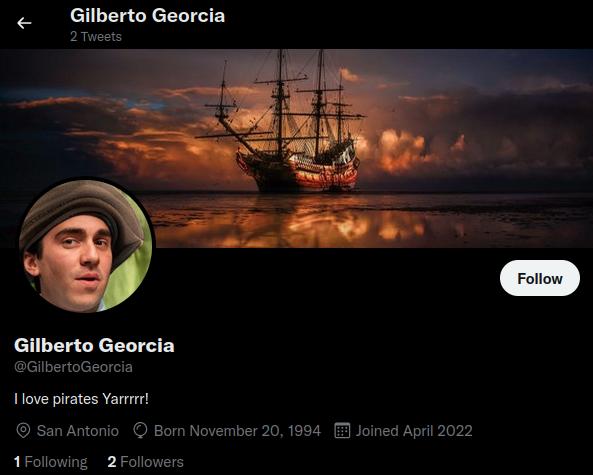
Then for Gerarto, the username revealed that he is likely to be born in 2001.
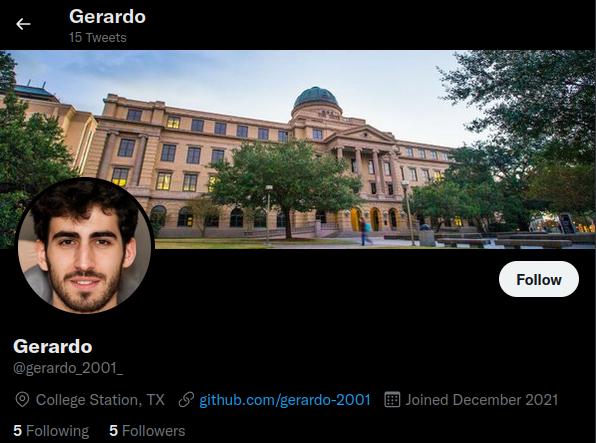
One of his tweets revealed his birthday is on 23 Dec.
There is also a github link at his account, which revealed that he is an intern at Greg Tech.
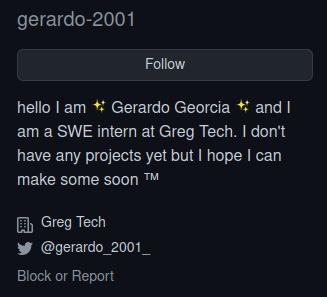
The difference of the brothers’ birthdays by days is calculated using https://www.timeanddate.com/date/durationresult.html that there is 2590 days between 20 Nov, 1994 and 23 Dec, 2001.
Flag: gigem{Greg_Tech_2590}
Got Skills?
100 points 49 solves
What organization hosted the CTF that took place in the city this image was taken in between March 31st and April 2nd?
The flag format isgigem{organization}Attachment:
ship.jpg
A reverse image search was done using https://yandex.com/images/ and the ship in the image was found to be USS Lexington CV-16.
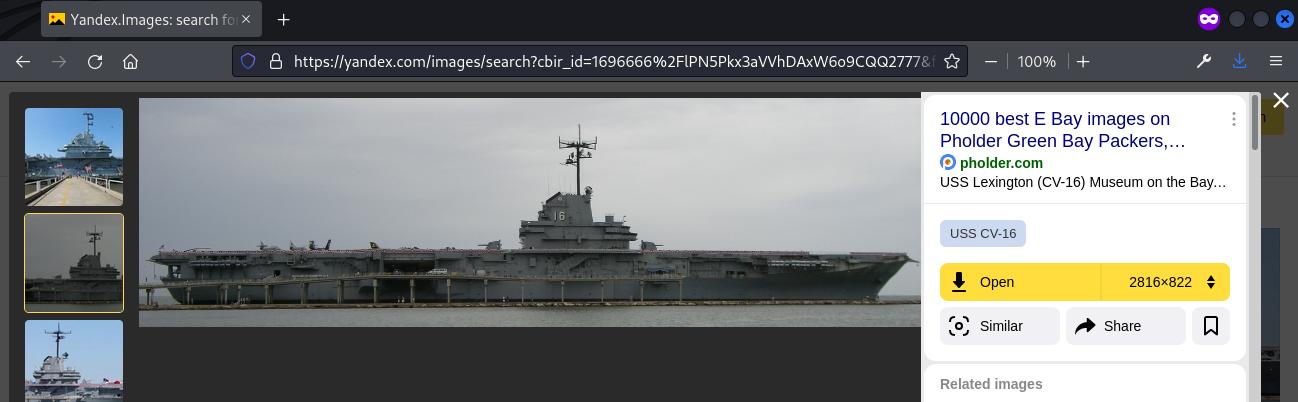
The museum is located at Corpus Christi, Texas. Google searched for the competition with the keyword “Corpus Christi 31 mar 2 apr cyber security” and the first result pointed at the SkillsUSA Texas Leadership & Skills Conference.
Flag: gigem{SkillsUSA}

Comments