picoCTF 2022 - Web Exploitation
Writeup for the picoCTF 2022 - Web Exploitation category
Updated:
Web Exploitation
Includes
100 points 7398 solves
inspector
Can you get the flag?
Go to this website and see what you can discover.
The button prompts an alert box hinting that the code is in a separate file.
When checking at the page source, the styles.css file contains the first half of the flag.
body {
background-color: lightblue;
}
/* picoCTF{1nclu51v17y_1of2_ */
The script.js file contains the second half of the flag.
function greetings()
{
alert("This code is in a separate file!");
}
// f7w_2of2_b8f4b022}
Flag: picoCTF{1nclu51v17y_1of2_f7w_2of2_b8f4b022}
Inspect HTML
100 points 7974 solves
inspector
Can you get the flag?
Go to this website and see what you can discover.
The flag is a comment in the source html file.
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>On Histiaeus</title>
</head>
<body>
<h1>On Histiaeus</h1>
<p>However, according to Herodotus, Histiaeus was unhappy having to stay in
Susa, and made plans to return to his position as King of Miletus by
instigating a revolt in Ionia. In 499 BC, he shaved the head of his
most trusted slave, tattooed a message on his head, and then waited for
his hair to grow back. The slave was then sent to Aristagoras, who was
instructed to shave the slave's head again and read the message, which
told him to revolt against the Persians.</p>
<br>
<p> Source: Wikipedia on Histiaeus </p>
<!--picoCTF{1n5p3t0r_0f_h7ml_fd5d57bd}-->
</body>
</html>
Flag: picoCTF{1n5p3t0r_0f_h7ml_fd5d57bd}
Local Authority
100 points 6562 solves
inspector
Can you get the flag?
Go to this website and see what you can discover.
There is a login form with the submit function handled by login.php. Looking into the php file reveals existence of secure.js and it contains the login username and password admin:strongPassword098765.
function checkPassword(username, password)
{
if( username === 'admin' && password === 'strongPassword098765' )
{
return true;
}
else
{
return false;
}
}
The flag is shown on the screen when logged in with the provided user account.
Flag: picoCTF{j5_15_7r4n5p4r3n7_a8788e61}
Search source
100 points 4741 solves
The developer of this website mistakenly left an important artifact in the website source, can you find it?
The website is here
The flag is a comment in style.css.
...
.navbar-expand-md .navbar-nav .nav-link {
padding: 15px 48px;
font-size: 16px;
color: #000;
line-height: 18px;
}
/** banner_main picoCTF{1nsp3ti0n_0f_w3bpag3s_8de925a7} **/
.carousel-indicators li {
width: 20px;
height: 20px;
border-radius: 11px;
background-color: #070000;
}
...
Flag: picoCTF{1nsp3ti0n_0f_w3bpag3s_8de925a7}
Forbidden Paths
200 points 4403 solves
Can you get the flag?
Here’s the website.
We know that the website files live in/usr/share/nginx/html/and the flag is at/flag.txtbut the website is filtering absolute file paths. Can you get past the filter to read the flag?
There is an input box for showing the content of a file according to the file name. The path ../../../../flag.txt was used as the input and the flag was returned.
Flag: picoCTF{7h3_p47h_70_5ucc355_e5fe3d4d}
Power Cookie
200 points 5515 solves
cookie
Can you get the flag?
Go to this website and see what you can discover.
The button to start a guest section adds a cookie isAdmin = 0. The cookie was edited to isAdmin = 1 and the page was reloaded, which returned the flag.
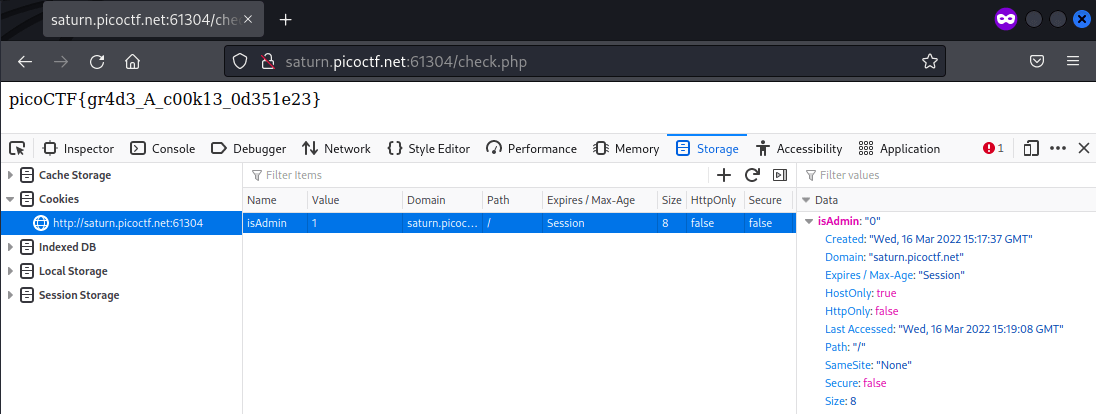
Flag: picoCTF{gr4d3_A_c00k13_0d351e23}
Secrets
200 points 3678 solves
We have several pages hidden. Can you find the one with the flag?
The website is running here.
index.html reveals a directory with the file secret/assets/index.css. The page secret/index.html was accessible.
The page source reveals another directory with file hidden/file.css and similarly, secret/hidden/index.html was accessible.
Tried to find login information at the page source but instead found another directory with the superhidden/xdfgwd.html. The page itself was not accessible but secret/hidden/superhidde/index.html was. Ctrl-A was used to select all and reveal the flag in white colour.
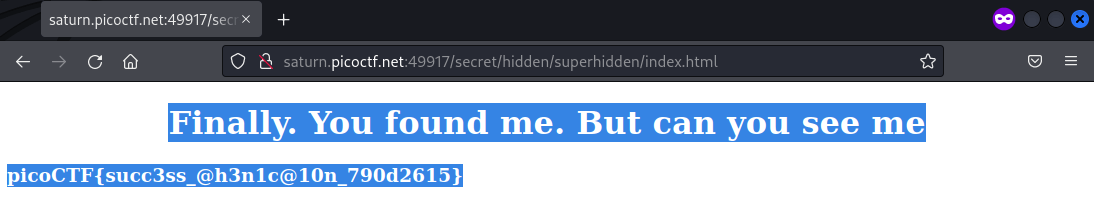
Flag: picoCTF{succ3ss_@h3n1c@10n_790d2615}
SQL Direct
200 points 3456 solves
sql
Connect to this PostgreSQL server and find the flag!
psql -h saturn.picoctf.net -p 59382 -U postgres pico
Password ispostgres
Connected to the database server and found the flags table. Listed all entries and the flag is returned.
pico=# \dt+
List of relations
Schema | Name | Type | Owner | Persistence | Access method | Size | Description
--------+-------+-------+----------+-------------+---------------+-------+-------------
public | flags | table | postgres | permanent | heap | 16 kB |
(1 row)
pico=# select * from flags;
id | firstname | lastname | address
----+-----------+-----------+----------------------------------------
1 | Luke | Skywalker | picoCTF{L3arN_S0m3_5qL_t0d4Y_21c94904}
2 | Leia | Organa | Alderaan
3 | Han | Solo | Corellia
(3 rows)
Flag: picoCTF{L3arN_S0m3_5qL_t0d4Y_21c94904}
SQLiLite
300 points 3714 solves
sql
Can you login to this website?
Try to login here.
There is a login form with the submit function handled by login.php. Looking into the php file reveals that the form might be vulnerable to SQL injection.
<pre>username:
password:
SQL query: SELECT * FROM users WHERE name='' AND password=''
</pre><h1>Login failed.</h1>
The username admin and password ' OR '1'='1 was submitted and successfully logged in. The page source revealed the hidden flag.
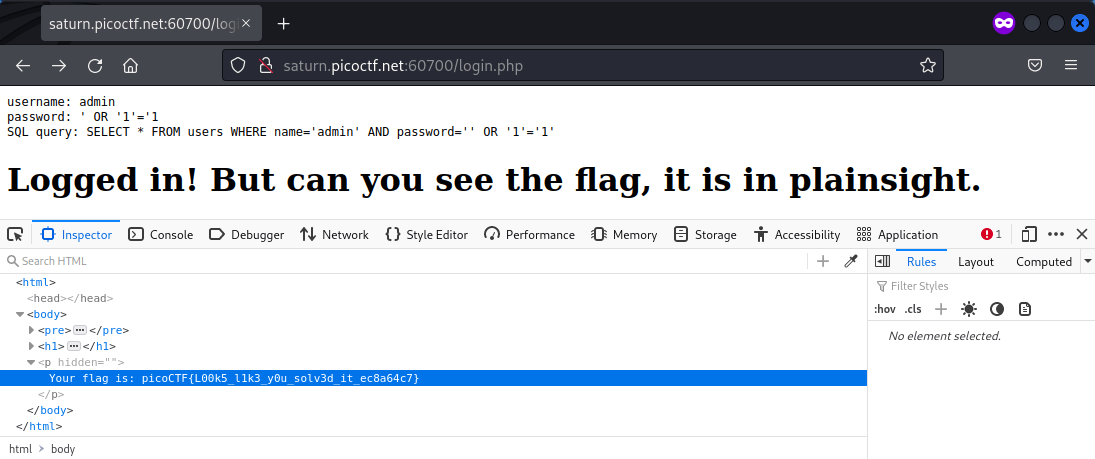
Flag: picoCTF{L00k5_l1k3_y0u_solv3d_it_ec8a64c7}
Comments