DaVinciCTF 2022
Writeup for the DaVinciCTF 2022
Updated:
Warmup
FrenchFlag
10 points 614 solves
Forensic
Can you find the data present in our flag?Attachment: flag.png
Basic check with exiftool reveals the flag at the Creator tag.
└─$ exiftool flag.png
ExifTool Version Number : 12.40
File Name : flag.png
...
Creator : dvCTF{flagception}
Image Size : 1280x853
Megapixels : 1.1
Flag: dvCTF{flagception}
EBG13
10 points 640 solves
Crypto
We found this message : can you decipher it?
qiPGS{3apElcg1ba_1f_r4fl}
The flag is encrypted with the ROT-13 cipher, which can be decrypted by shifting each character 13 places forward or with CyberChef.
Flag: dvCTF{3ncRypt1on_1s_e4sy}
QmFzZTY0
10 points 527 solves
Crypto
Attachment: file.txtVm0wd2QyUXlVWGxWV0d4V1YwZDRWMVl3WkRSV01WbDNXa1JTVjAxV2JETlhhMUpUVmpBeFYySkVUbGhoTVVwVVZtcEJlRll5U2tWVWJHaG9UVlZ3VlZadGNFSmxSbGw1VTJ0V1ZXSkhhRzlVVmxaM1ZsWmFjVkZ0UmxSTmJFcEpWbTEwYTFkSFNrZGpSVGxhVmpOU1IxcFZXbUZrUjA1R1UyMTRVMkpIZHpGV1ZFb3dWakZhV0ZOcmFHaFNlbXhXVm1wT1QwMHhjRlpYYlVaclVqQTFSMXBGV2xOVWJGcFlaSHBHVjFaRmIzZFdha1poVjBaT2NtRkhhRk5sYlhoWFZtMHdlR0l4U2tkWGJHUllZbFZhY2xWcVJtRlRSbGw1VFZSU1ZrMXJjRWxhU0hCSFZqSkZlVlZZWkZwbGEzQklXWHBHVDJSV1ZuUmhSazVzWWxob1dGWnRNWGRVTVZGM1RVaG9hbEpzY0ZsWmJGWmhZMnhXY1ZGVVJsTk5WMUo1VmpJMWExWXdNVVZTYTFwV1lrWktTRlpxUm1GU2JVbDZXa1prYUdFeGNHOVdha0poVkRKT2RGSnJhR2hTYXpWeldXeG9iMWRHV25STldHUlZUVlpHTTFSVmFHOWhiRXB6WTBac1dtSkhhRlJXTUZwVFZqSkdSbFJzVG1sU2JrSmFWMnhXWVZReFdsaFRiRnBZVmtWd1YxbHJXa3RTUmxweFVWaG9hMVpzV2pGV01uaGhZVWRGZUdOR2JGaGhNVnBvVmtSS1QyTXlUa1phUjJoVFRXNW9WVlpHWTNoaU1rbDRWMWhvV0dKRk5WVlVWM1J6VGtaVmVXUkhkRmhTTUhCSlZsZDRjMWR0U2tkWGJXaGFUVzVvV0ZreFdrZFdWa3B6VkdzMVYwMVZiekZXYlhCS1RWZEZlRmRZWkU1V1ZscFVXV3RrVTFsV1VsWlhiVVpPVFZad2VGVXlkREJXTVZweVkwWndXR0V4Y0ROV2FrWkxWakpPU1dKR1pGZFNWWEJ2Vm10U1MxUXlUWGxVYTFwb1VqTkNWRmxZY0ZkWFZscFlZMFU1YVUxcmJEUldNV2h2V1ZaS1IxTnNaRlZXYkZwNlZHeGFZVmRGTlZaUFZtaFRUVWhDU2xac1pEUmpNV1IwVTJ0a1dHSlhhR0ZVVmxwM1lVWndSbHBHVGxSU2EzQjVWR3hhVDJGV1NuUlBWRTVYVFc1b1dGbHFTa1psUm1SWldrVTFWMVpzY0ZWWFYzUnJWVEZzVjFWc1dsaGlWVnBQVkZaYWQyVkdWWGxrUkVKWFRWWndlVmt3V25kWFIwVjRZMFJPVjJGcldreFdha3BQVTFkS1IxcEdaRk5XV0VKMlZtMTBVMU14VVhsVVdHeFZZVEZ3YjFWcVRrTldSbXh5Vm01a1YxWnNjREJhVldNMVZXc3hXRlZ1Y0ZkTlYyaDJWakJrUzFKck5WZFZiRlpYVFRKb1NWWkhlR0ZXTWxKSVZXdG9hMUl5YUhCVmJHaENaREZhYzFwRVVtcE5WMUl3VlRKMGExZEhTbGhoUjBaVlZteHdNMWxWV25kU2JIQkhWR3hTVTJFelFqVldSM2hoVkRKR1YxTnVVbEJXUlRWWVZGYzFiMWRHYkhGVGExcHNVbTFTV2xkclZURldNVnB6WTBaV1dGWXpVbkpXVkVaelZqRldjMWRzYUdsV1ZuQlFWa1phWVdReVZrZFdXR3hyVWtWS1dGUldXbmRsVm10M1YyNWtXRkl3VmpSWk1GSlBWakpHY2xkcmVGZE5WbkJJV1RJeFMxSXhjRWhpUm1oVFZsaENTMVp0TVRCVk1VMTRWbGhvV0ZkSGFGaFpiWGhoVm14c2MxcEhPVmRTYkVwWlZHeGpOVll4V25OalJXaFlWa1UxZGxsV1ZYaGpiVXBGVld4a1RsWXlhREpXYWtKclV6RktjazVXWkZkaVJscFlWRlJHUzA1c1draGtSMFpYWWxaYVdWWlhkRzloTVVwMFlVWlNWVlpYYUVSVk1uaGhZekZ3UlZWdGNFNVdNVWwzVmxSS01HRXhaRWhUYkdob1VqQmFWbFp1Y0Zka2JGbDNWMjVPVDJKRmNIcFhhMlIzWVZaT1JsTnJiRmhXYkZweVdYcEdWbVF3TVVsaFJrNW9Za2hDV1ZkV1pEQmtiVkY0VjJ4V1UySkdjSE5WYlRGVFRWWlZlV042UmxoU2EzQmFWVmMxYjFZeFdqWlJhbEphWVd0YVlWcFZXbGRqTWtaR1QxWmthR1ZzV2xGV2ExcGhXVmRSZVZaclpGZFhSM2h5Vld0V1MxZEdVbGRYYm1Sc1ZtMTBNMVl5Tld0WFJrbDNWbXBTV2sxR1NsQldNakZHWlZaV2NscEhSbGROTW1oSlYxUkplRk14U1hsU2EyUm9VbXhLVkZac2FFTlRNVnAwVFZSQ1ZrMVZNVFJXYkdodlYwWmtTR0ZHYkZwaVdHaG9WbTE0YzJOc2NFaFBWM0JUWWtoQ05GWnJZM2RPVjBWNVUydGthbEpYYUZoWmJGSkNUVlphV0dNemFGaFNiRm94V1RCYWExUnNXWGxoUkVwWFlXdEtjbFY2Umt0amF6VlhXa1phYVZKc2NGbFhWM2hoVW0xUmVGZHVSbE5pVlZwWVZGZDRTMU5XV2xoa1J6bG9UVlZ3TUZaWGN6VldNa1p5VjJ0NFZrMXVhSEpXYWtaaFpFWktkR05GTlZkTlZXd3pWbXhTUzAxSFJYaGFSV2hVWWtkb2IxVnFRbUZXYkZwMFpVaGtUazFZUWxsYVZXaExZa1paZUZkcmJHRlNWMUYzVmxSS1JtVnNSbGxhUm1ocFVteHdiMWRXVWt0U01XUkhVMnhzWVZJelFsUldhazV2VjFaa1dHVkhPVkpOVmtwSVZsYzFTMWRIU2taalNFNVdZbFJHVkZwWGVITldiR1J6Vkcxb1UxWkZXalpXVkVreFlqRlplRmRxV2xOV1JVcG9WV3RXWVdOc1ZuRlRhM1JVVm14S01GbFZXazloUjFaelYycGFWMDFYVVhkWFZtUlNaVlphY2xwR1pGaFNNMmg1VmxkMFYxTXhaRWRWYkdSWVltMVNjMVp0ZUhOT1ZuQldZVWQwV0ZJd2NFaFpNRnB2VjJzeFNHRkZlRmROYm1ob1ZqQmFWMk5zY0VoU2JHUk9UVzFvU2xZeFVrcGxSazE0VTFoc1UyRXlVbTlWYlhoTFZrWmFjMkZGVGxSTlZuQXdWRlpTUTFack1WWk5WRkpYWWtkb2RsWXdXbXRUUjBaSFlrWndhVmRIYUc5V2JURTBZekpPYzJORmFGQldNMEpVV1d0b1EwNUdXbkpaTTJSUFZteHNORll5TlU5aGJFcFlZVVpzVjJFeFZYaGFSM2h6VmpGYVdXRkdhRk5pUm5BMVYxWldZV0V4VW5SU2JrNVlZa1phV0ZsVVNsSk5SbVJYVjJ0MGFrMVdTakZXUnpGdlZUSktSMk5HYkZkU2JFcE1XV3BHVDFZeFpISmhSM2hUVFVad2FGWnRNSGhWTVU1WFYyNVNhMUo2Ykc5VVZsWnpUbFpzVm1GRlRsZGlWWEJKV1ZWV1QxbFdTa1pYYmtwWFlXdGFhRnBGVlRWV01WcHlUbFprYVdFd1dYcFdiWGhxWkRBeFYxUllhRmhoTW1oVldXdGtiMkl4Vm5GUmJVWlhZa1p3TUZwVmFHdFVhekZaVVd4c1lWWlhhRXhaYTFwaFZsWktjMXBHYUdoTldFSlJWMVphWVZNeVRuUlVhMVpZWWtkU2IxUlhjekJOUm1SWlkwVmtWMkpXV2xoV1J6VlhWa2RLUjFOdVFsZGlSbkF6VmpGYVlWSXhiRFpTYld4T1ZqRktTVll5ZEdGaE1XUklVMnRhYWxORk5WZFpiRkpIVmtad1dHVklUbGRpUjFKNlZrY3hiMVl5UlhwUldHaFhWbTFOZUZscVJscGxSbVJaWTBkb1ZGSllRbGxXYlhSWFdWZFdjMWR1UmxOaVIxSnhWRlprVTJWc2JGWmFTRTVYVFZad01WVlhjR0ZXTURGWVZWaGtXRlp0VWs5YVJFRjRVMWRHUjJGR2FGTk5NbWhSVm0weE5HRXhWWGhYV0doV1lrZG9jbFV3WkZOV1JsSlhWMnQwYkdKSGVGZFpWV1F3VjBaSmQyTkZhRnBOUm5CMlZqSnplRk5IUmtabFJtUk9ZbTFvYjFacVFtRldNazV6WTBWb1UySkhVbGhVVmxaM1ZXeGFjMVZyVGxkaGVsWllWakZvYjJGc1NsaGhSemxXWVd0d2RsWkVSbFprTVZweVpFVTFhVkp1UVhkV1JscFRVVEZhY2sxV1drNVdSa3BZVm0weGIyVnNXblJOVlZwc1ZteGFlbFl5ZUhkaFZtUkhVMWh3V0Zac1dtaFdha3BUVTBaYWNsZHRkRk5OTUVwVlYxZDBiMUV3TlVkWGJrcGFUVEpTVUZadE1WTlRSbGw1VGxVNWFHSkZjREJhVldSSFZsWmFWMk5HWkZWV2JIQjZWbXBHWVZkWFJrZGhSazVwVW01Qk1WWXhXbGRaVjBWNFZXNVNVMkpyTlZsWmExcGhWMFpzVlZOc1NrNVNiRmt5VlcxME1HRnJNVmxSYTNCWFlsaG9WRmxXV2t0ak1rNUhZa1pvVjAweFNtOVhhMUpDVFZkTmVGcElTbWhTTTJoVVZGVmFkMkZHV25STlNHaFdUVlUxV0ZZeU5WTmhNVW8yWWtjNVZWWnNXbnBVYkZwelZtMUdSbFJzWkdsV1dFSktWMVpXVjFReGJGZFRhMXBZWW10d1dGbFhkR0ZoUm5CR1ZsUldWMDFXY0hsVWJGcHJZVmRGZDFkWWNGZGlXR2h4V2tSQmVGWXhVbGxoUm1ob1RXMW9WbGRYZEd0aU1rbDRWbTVHVW1KVldsaFphMXAzVFVad1ZtRkhkRlZoZWtaWldsVmFhMVl3TVhGV2JrcFhWa1Z3VEZVeFdrZGpiVVpIV2taT1RrMXRhRlpXYlRGM1V6Rk5lVlJ1VGxWaWEzQnhWVzB4YjJOR1ZuUmxTR1JzVm0xU1dsa3dWbXRXTWtwWFYyeG9WMUo2VmxCWlZscExaRlpHY2s5V1ZsZGxhMW95Vm1wR1lXRXhXWGhXYmtwaFVqTlNUMWxVUm5kVFZscHhVMnBTVjAxV1ZqVlZNblJyWVd4T1JrNVdaRnBpUmtwSVZtdGFVMVl4WkhOWGJYaFhUVVJSZVZaWE1UUmlNVlY1VWxod1VtSlZXbGhXYlRGT1pVWnNjVkpzY0d4U2JWSmFXVEJrYjFaR1NsbFJiR1JZVm14S1RGWlVSazlTTVZwMVVteE9hVlpXY0ZwV2JUQXhVVEZPVjJKR1dsaGhlbXhZVkZaYWQxTkdXWGxsUjBaWFRXdHdTVlpIY0ZOV1YwVjVWV3hPWVZac2NHaFpNbmgzVWpGd1IyRkdUazVOYldjeFZtMTRhMlF4UlhoaVJtaFZZVEpTV0ZsdGVFdGpNVlYzV2taT2FrMVhlSGxXTW5oclZERmFkVkZzWkZwV1YxRjNWakJhU21ReVRrWmhSbkJPVW01Q01sWnFTbnBsUms1SVVtdGFiRkp0VWs5WmJURnZZakZhY1ZGdFJsZE5helY2V1RCV2IxVXlTa2hWYkdoVlZteGFNMVpYZUdGak1WWnlXa2RvVGxaVVJUQldWRVp2WWpKR2MxTnNhRlppVjJoWFdXeG9UbVZHV1hkWGJIQnJUVlp3ZVZwRlZURmhWa3AxVVZoa1YxSnNjRlJWVkVaaFkyc3hWMWRyTlZkU2EzQlpWbTB3ZUdJeVZuTlhibEpPVmxad2MxWnRlR0ZsYkZwMFpVaGthRlp0VWtoVk1XaDNWMFpaZWxGcmFGZGhhM0JRVm1wR1UyUldWbk5SYkdScFZtdHdWbFl4WkRSaU1rbDNUbFprV0dKc1NrOVZhMVpoWWpGU1YxZHVUazlTYkd3MVZHeFZOV0ZIU2taalJXUldUV3BHZGxacVNrdFRSbFp5VDFaV1YySklRbTlXYWtKclZHMVdkRkpyWkdoU2F6VndWVzAxUWsxc1dYaFhiR1JhVmpCV05GWlhOVTlYUm1SSVpVYzVWbUV4V2pOV01GcFRWakZrZFZwSGFGTmlSbXQ1VmxjeE1HUXlTa2RUYms1VVlXdGFXRlZ1Y0VkVFJscFZVMnQwVTAxck5VaFphMXB2VmpBd2VGTnRPVmhoTVVwRFZGWmtUbVZHY0VsVGJVWlRZa2hDZGxaR1pEUlRNV1JIVjJ0a1lWTklRbk5WYkZKWFYwWmFkRTVXVG1oTlZXd3pWako0YTFadFNsbGhTSEJWWWtad2VsWnRNVWRTYkZKeldrZHNWMWRGU2t0V01WcFhWakZWZUZkc2FGUmlSM2h2VlRCV2QxZEdiSEpYYm1SVVVtNUNSMVl5ZERCaE1VbDNUbFZrVldKR2NISldSM2hoVjBkUmVtTkdaR2xYUjJoVlZsaHdRbVZHVGtkVGJHeG9VakJhVkZacVNtOVdiR1JZWkVkMGFVMXJiRFJXYlRWVFZHeGFObUpHYUZwaE1YQXpXbGQ0V21WVk5WaGtSbFpvWld0YVdWZFVRbTlqTVZsM1RWaEdVMkV5YUdGV2FrNXZZVVpyZVUxVk9WTldhMW93VlcxNFQxWXdNVlpYV0hCWFlsaG9WRlY2Umt0a1JscDFWR3hPYVZJemFHOVdWekI0WWpKT1IxWnVVbXhUUjFKd1ZGWmtVMWRHV2xoa1JFSldUVVJHV0ZsclVsTlhSMFY1WVVab1YyRXlVa3hXTUdSWFUxWlNjMk5HWkZOV2JUazJWbTF3UjFsWFJYaFhXR2hxVWxaYVUxbHNhRk5qUmxwMFpFWndUbEpzY0hoVk1uQlRWakF4VjFacVZsWmlSMmgyV1ZkNFQxSnJOVmRhUm5CcFVtdHdTVlp0ZEdGa01XUklWbXRzVldKSFVuQlZha1pMVG14YWNsa3phR2xOVmxZMFZqSjBZVmRIUm5OalJtaFhZVEZhZVZwVlduTldWa3B6WTBkNFUySldTbUZYVkVKaFdWZEdWMWRZYkdoU2JXaFpXV3RrVW1ReFpGZFhiazVYVFdzMVNGWXllRzloVmtsNFUyNW9WMUp0VVhkWFZscEtaVVpXV1dGR2FHbFhSa3AzVmxkd1EyUXhaSE5pUmxwV1lsVmFXRlJWVWtkWFZscFhZVWQwV0ZKc2NEQldWM2hQV1ZaYWMyTkhhRnBOYm1nelZXcEdkMUl5UmtkVWF6Vk9ZbGRqZUZadE1UUmhNREZIVjFob1ZWZEhhR2hWYkdSVFYwWnNkR1ZGZEdwaVJsWXpWMnRhVDJGck1WaGxTR3hYVFc1b2NsWkVSbUZrVmtaeldrWndWMVl4UmpOV2FrSmhVMjFSZVZScldtaFNia0pQVlcwMVEwMXNXbkZUYm5Cc1VtczFTRlp0TlZkWFIwcElWV3M1V21KVVJuWlpha1poWTFaR2RGSnNaRTVoZWxZMlYxUkNWMkl4VlhsVGEyaFdZa2RvVmxadGVHRk5NVnBZWlVkR2FrMVlRa3BYYTFwVFZHeGFWVkpVUWxkV1JWcDJXWHBHVm1WV1NsbGlSMmhUWlcxNFdGZFhkR0ZUTVdSSFYxaGtXR0pyTlhKVmFrWkxVakZ3UmxaVVJtaFdhM0F4VlZab2ExWXhTbk5qUmxKV1ZrVmFhRmt5YzNoV01XUnlUbFprVTJFelFscFdiVEF4WkRGWmVGZHJaRmhpYTFwVldWUkdkMk14V25SbFIwWk9VbTE0VjFZeU1VZFdWMHBHWTBSR1ZsWjZRVEZXYWtwTFZsWktWVkZzY0d4aE0wSlJWMWh3UjJReFRsZFdiazVWWWxkNFdWVnNWbmRXYkZsNFdrUkNhVTFWVmpOVWJGWnJWMGRLY21OSFJsVldSWEJVVmxWYVlXUkhWa2xVYXpsVFlrZDNNVlpIZUZaT1YwWklVMnRhYWxKdGVHRldiRnAzWkd4YWMxZHRSazlpUm5BeFZqSjRkMVJ0U25SaFJGcFhZbGhvYUZWcVJtdFhSa3B5V2tkb1UyRjZWbmRXVnpCM1RsVTFSMWRZYUZaaE1EVmhWbXBDVjA1R1dsaE9WVGxZVW0xU1NWcFZZelZXYlVWNFYycE9WMDFHY0hwV01HUlRVbTFTU0dOSGJGTmlSM1ExVm14amVFMUZNVWhTYmxKVFlXeHdXRmxyWkc5WFZteFZVbTVrYUZKdGVGaFdNblF3WVdzeGNrNVZhRnBoTVhCMlZtcEJkMlZHVG5SUFZtUm9ZVE5CTWxkc1ZtRlRiVlpIWTBWc1ZHSlhhRlJVVkVaTFZsWmFSMVp0Um10TlYxSllWakowYTFsV1RrbFJiazVXWWtaS1dGWXdXbUZrUlRWWFZHMW9UbFpYT0hsWFYzUmhZVEZhZEZOc2JHaFNSVFZXVm14YWQyRkdXWGRXVkVaWFlrWktlbGRyVlRGaFJUQjNVMnQwVjAxV2NGaFdha1pXWlVaa2MyRkdVbWhOYkVwNFZsZHdTMkl4V1hoVmJGcGhVbXMxV1ZWdGVGZE5NVmw1WkVSQ2FHRjZSbGxXVnpWelZsZEtSMk5JU2xwV2JIQnlWVEJhVTJOV1ZuTmFSMnhZVWpKb05WWnJaREJoTVU1MFZteGtWbUpIZUc5VmJURnZZMFpzV1dOR1pGaGlSMUpZVmxkMGEyRXdNVmRqUm1oYVlUSm9URmRXV2t0T2JVcEhZa1phYVZaRlZYZFdha1poWTIxV2RGUnJXbUZTTW1oUFdWUk9RMU5zWkhOV2JVWm9UVlpzTTFSV2FFZFZNa1Y1WVVkR1YyRnJOWFpaVlZweVpWVXhWazlXVWxkTlJGWkpWMVpXYTJJeFVuTmFSVnBVVjBkNFdGbHNVa2ROTVZZMlVtczFiRlpzU2pGV1IzaFhZVmRGZWxGdVpGZFdla0kwVmxSR2ExSXlTa2xVYkdob1RWaENlVlpHV21Gak1EVkhWMWhzVGxaWFVsbFZha0ozVjBaWmVXUkhPVmROVlc4eVZtMTBORll3TVVoVmEzaFdZbGhOZUZacVNrZFNNV1IwWWtaT2FXRXdjRnBXYlhSclRrWktjazlXWkZKaVJYQlNWbXRTUWs5UlBUMD0
The flag is encoded in the Base64 format and it is revealed after decoding it for 20 times using CyberChef.
Flag: dvCTF{Base64_Is_The_Best}
MP3
10 points 218 solves
Steganography
The flag in the audio is given without the tag format!
You must fill in : dvCTF{flag}Attachment: MP3.mp3
The flag is spoken out in the MP3 file. Reverse the audio and slow it down to listen the flag.
Flag: dvCTF{r3v3rs3_mp3}
RSA
87 points 79 solves
Easy
Our team has found a cipher text: there seems to be some clues to decipher it. Can you help us to read it?n = 0x7CD1020889B4382BE84B3F14EAAE242755CC1BD56F431B348F4FF8F207A96F41AFCF3EBDF4C17CB6537AD4B01B9FF9497763B22D013B614C8FCDB0C34F9D88F1A523013791EDFEB1FBBA160799892C118892FB7F199C9957DF5A26DAB4D776E5226F06ACD05412F6DD2B1B75D24CE9DC2DDAC513BCB96CD9B97F9BEF8543A3A1 phi = 0x7CD1020889B4382BE84B3F14EAAE242755CC1BD56F431B348F4FF8F207A96F41AFCF3EBDF4C17CB6537AD4B01B9FF9497763B22D013B614C8FCDB0C34F9D88F037D2317D3864035ECE8BCDD458711B788B5B3FDFD5164F7D736D0A56F416E8C16126E3868D73F54AF4D61F6033E069994319C849460C60A725A0F4DD97EDCC84 e = 0x10001 ct = 0x268D7D5F5593EA30F536635B58585620B51D2D143AFE4734635C259278D61413D0C89678E81EDF466B1E45E27EBF802F62F61263E499A516465163C7CB668F94258B3424C3E2BD76634923DECD670E4B6034F8FD00C76F9DAD00A72DB22B70B9408C89FCEE4C9B0D2D4B5664284328711BFAD57FBE1EDCC0854AAD57390DCAD6Hint: There is another decoding step after the decryption!
First, convert the Hex numbers to Decimal using https://www.rapidtables.com/convert/number/hex-to-decimal.html.
n = 87649082972615446885156213990388141958462041885187282183358321369043253078954716183685582963065012168992348062798954305060720006415266001335650005751863897735171741039420405425935144397447296138110870810719506425543947491726403454512721294407851871180512317063750030012483422248351385763316752934512386876321
phi = 87649082972615446885156213990388141958462041885187282183358321369043253078954716183685582963065012168992348062798954305060720006415266001335650005751863878602037628450194440652151553598137526621296494079379835255789373284025572667141114891644303376103362880682087270696210666254302024051328494090372669885572
e = 65537
ct = 27072622593514815453879432614324701776473574595747953216191498481974488509392434673536099100283731897243171732583922534894433636848515336632487302801454568578704912185172822029407973421574599852974535422485632743936976338461213855442178470548247222162434148032907372865397517157263392748002249405715658427094
Calculate the private key and use it to decrypt the ciphertext using https://www.dcode.fr/rsa-cipher gives 100118678470123102108521039599861127251114116518811695988695828352125.
Convert the number to ASCII text using https://onlineasciitools.com/convert-decimal-to-ascii reveals the flag.
Flag: dvCTF{fl4g_cVpH3rt3Xt_bV_RS4}
Steganography
The Art of Details
50 points 145 solves
Easy
A simple detail can make a big difference Always beware of the first element
Warning ! flag format : dvctf{flag}Attachment: The_Art_of_Details.docx
With the help of the Accessibility function, it showed that there are three images in the document, with a very small size located on the full stop of the first three paragraphs.
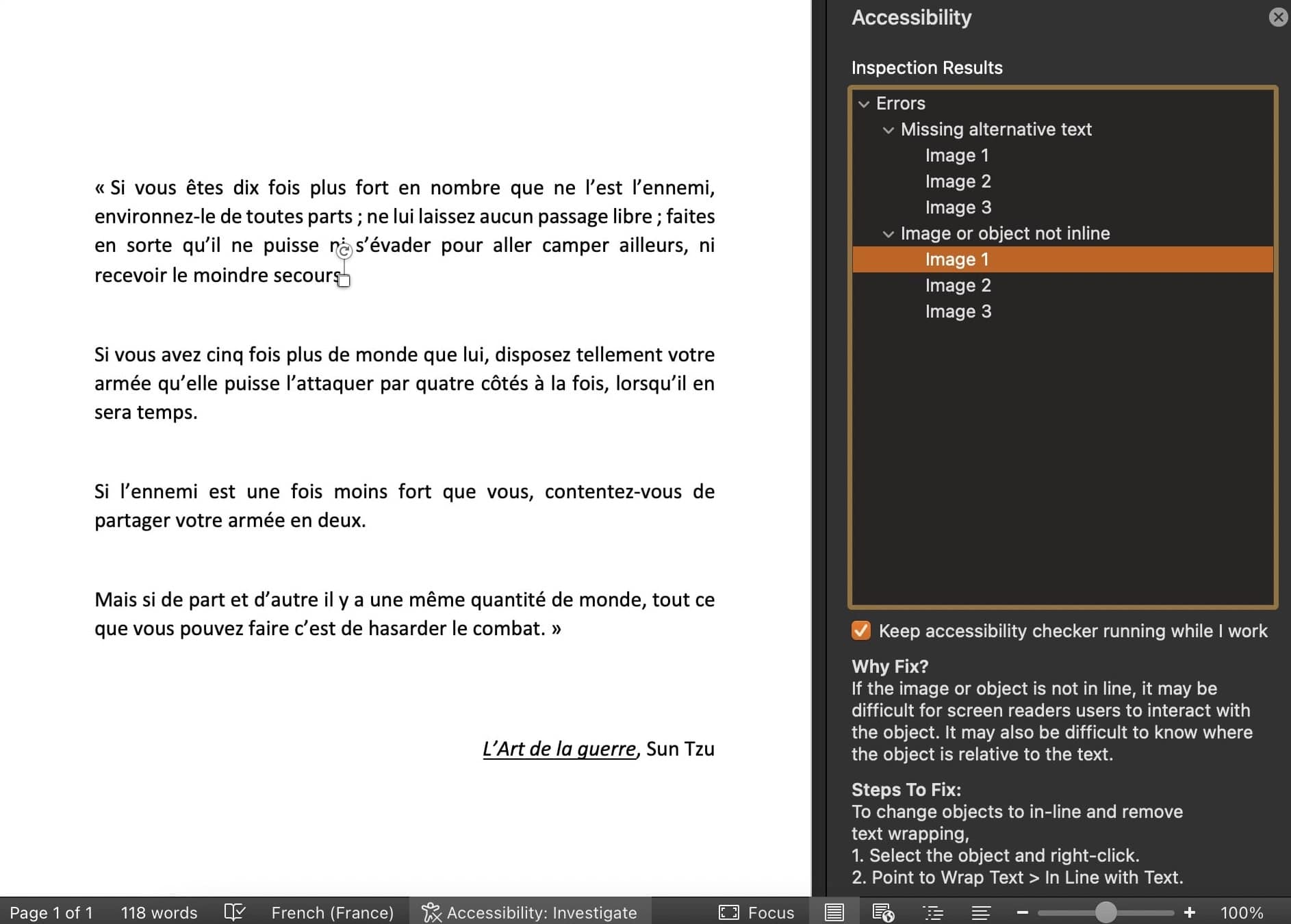
Increasing the size of the images reveal three QR codes.
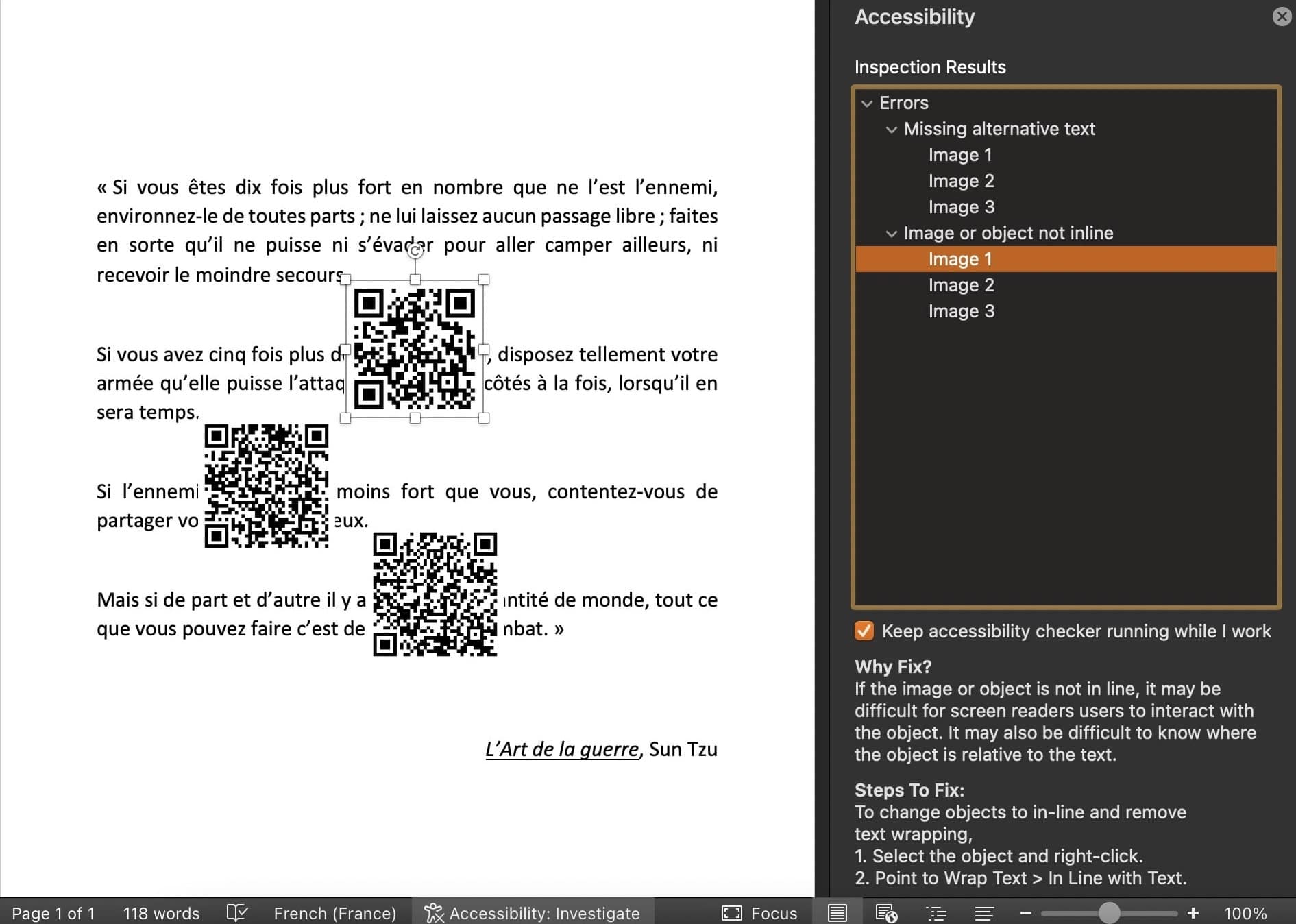
The images can also be revealed and extracted with binwalk, as Microsoft Office documents are actually compressed files.
└─$ binwalk -e The_Art_of_Details.docx
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
...
4760 0x1298 Zip archive data, at least v1.0 to extract, compressed size: 518, uncompressed size: 518, name: word/media/image1.png
5329 0x14D1 Zip archive data, at least v1.0 to extract, compressed size: 723, uncompressed size: 723, name: word/media/image2.png
6103 0x17D7 Zip archive data, at least v1.0 to extract, compressed size: 714, uncompressed size: 714, name: word/media/image3.png
...
Scanning the QR code gives the following strings:
image1.png: aXRpc25vdHRoZWZsYWc=
image2.png: dGhla2V5ezRBajgyRDZoUlpLQThocXA1dG01fQ==
image3.png: defaw{u1qeuugx&crl0gl_4_r_fbe4a_f4hli0rm}
The third string looks like the encrypted flag while the first two strings are encoded in Base64, decoding it gives:
image1.png: itisnottheflag
image2.png: thekey{4Aj82D6hRZKA8hqp5tm5}
The key seems to be hinting that the flag is encrypted with the Vigenère cipher.
Since digits are not allowed to be in the key, all digits were removed from the key and AjDhRZKAhqptm was used to decrypt the flag using CyberChef.
Flag: dvctf{v1genere&qrc0de_4_a_gre4t_p4ssw0rd}
ICMP
292 points 85 solves
Medium
Attachment: icmp.pcap
The data of the ICMP packets in ASCII are in Base64 format and decoding it gives the following.
This is not a flag!
Neither does this package!
Search a little more, you will eventually find ...
... They wrote a poem :D ...
In fact, the flag is not in this part of the packages, sorry...
Well, got to look at elsewhere.
The id of the packets look like Hex numbers. The packets are exported as plaintext with the “Export Packet Dissections > As Plain Text” function in WireShark.
First, the packets are arranged according to the seq number, then the id is extracted and converted from Hex number to ASCII, then decoded as Base64. The flag is then revealed.
import re
import base64
ids = [0] * 32
with open("icmp.txt", "r") as f:
lines = f.readlines()
for line in lines:
if("id=0x00" in line):
seq = int(re.findall(r"seq=(\d+)", line)[0])
ids[seq-1] = re.findall(r"id=0x00(\w+)", line)[0].decode("hex")
print(base64.b64decode("".join(ids) + "=").decode())
Flag: dvCTF{h1dden_1n_the_1d}
OSINT
Monkeey
50 points 344 solves
Easy
In what city is the statue of this monkey found? Wrap it around with the wrapper: dvCTF{city_in_lowercase}Attachment: img.png
Google searched for the image with the keyword “big balls gorilla” reveals a sculpture of the image.
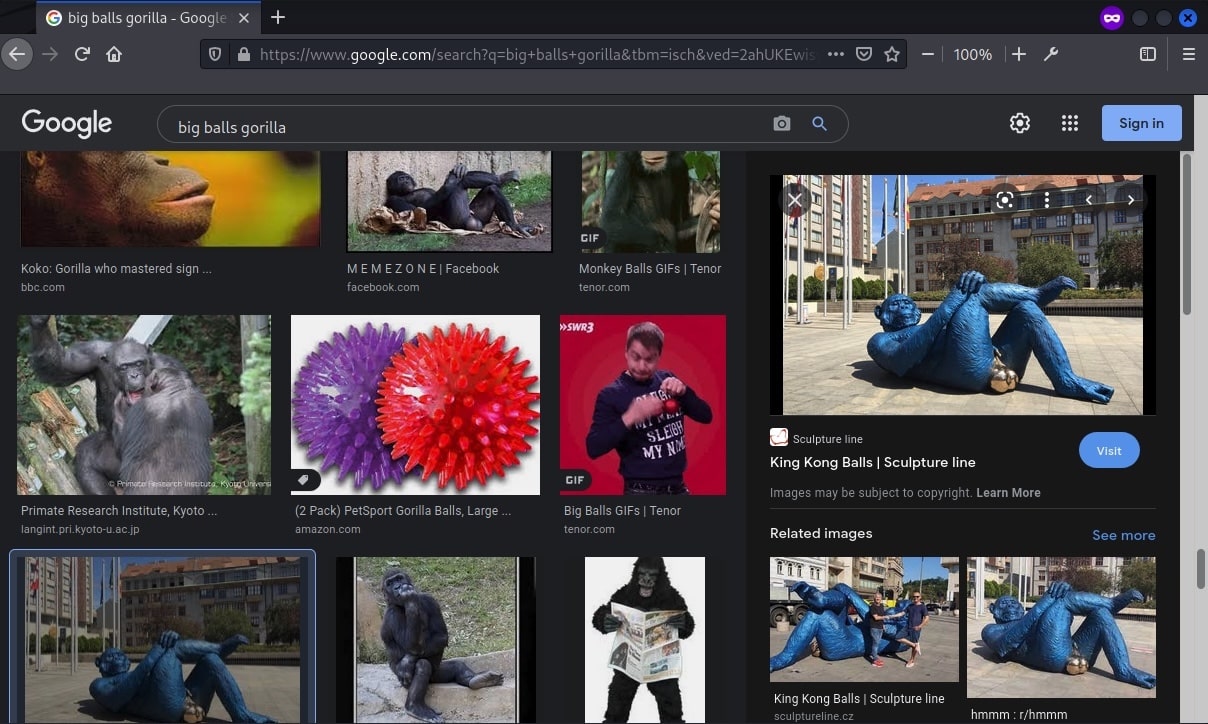
Going to the website with the sculpture image gives more information, that the sculpture is called King Kong’s Balls and is located at Milos Forman Square, Prague, Czech Repblic.
Flag: dvCTF{prague}
Elon Musk
120 points 115 solves
Easy
Hi,
I’m a huge fan of Elon Musk so I invested all my money in cryptocurrencies. However, I I got lost in the cryptoworld and I lost something, can you help me find it?
Sincerely,
@IL0veElon
Searching the username on Google shows a twitter account.
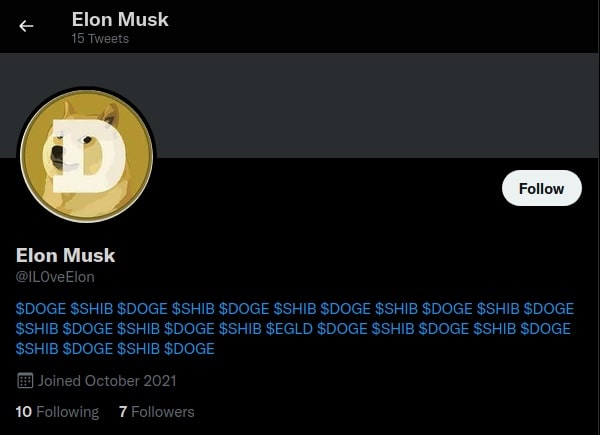
Scrolling through the account, one of the tweets looked like a hash that could be transaction ID or something.
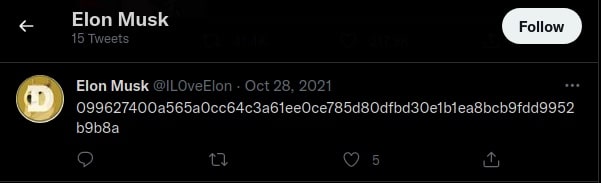
Referring back to the profile section, the cryptocurrency is likely to be either $DOGE, $SHIB, or the one $EGLD lying in between a bunch of the other two.
With that being said, $EGLD transactions were being searched with the string 099627400a565a0cc64c3a61ee0ce785d80dfbd30e1b1ea8bcb9fdd9952b9b8a at https://explorer.elrond.com.
The string is indeed the hash of the transaction and the flag is at the input data section.
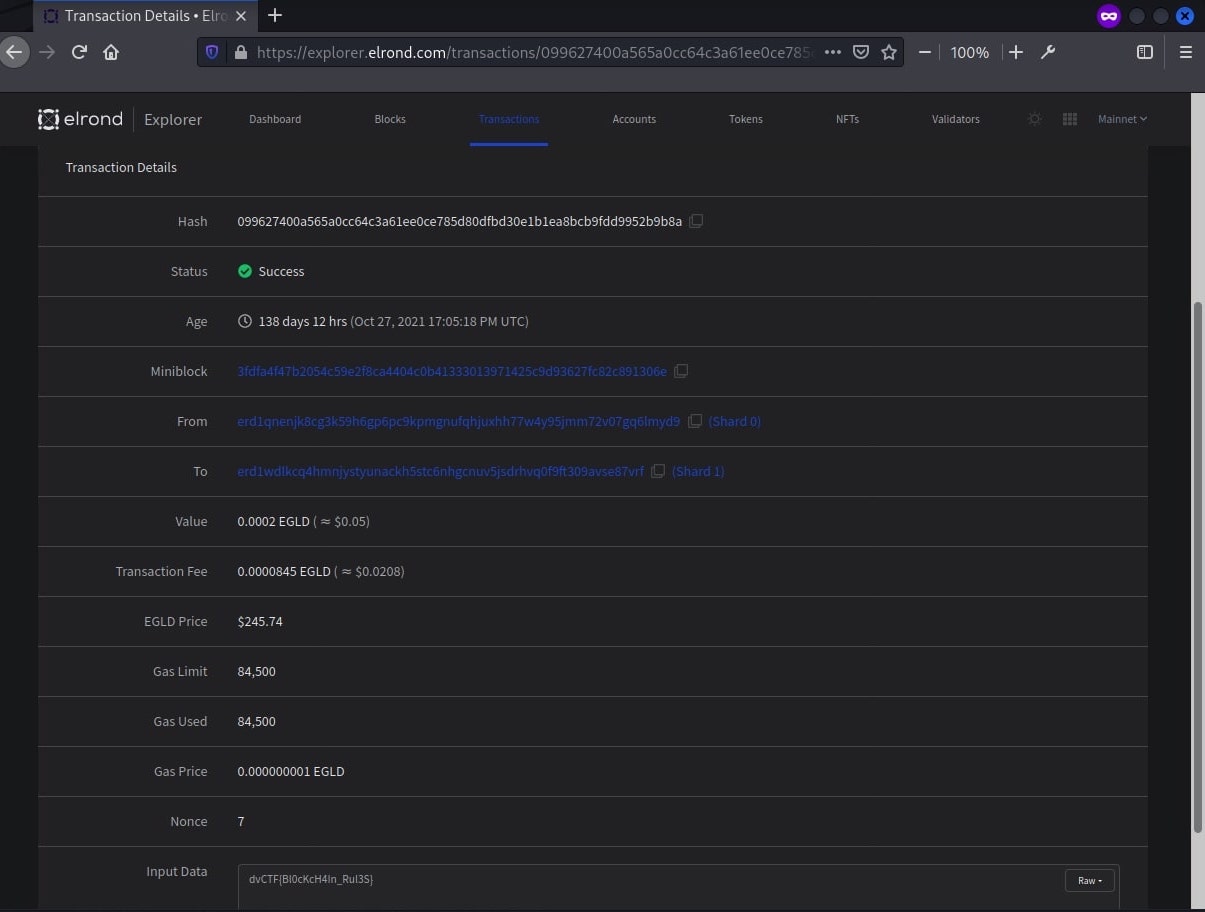
Flag: dvCTF{Bl0cKcH4In_Rul3S}
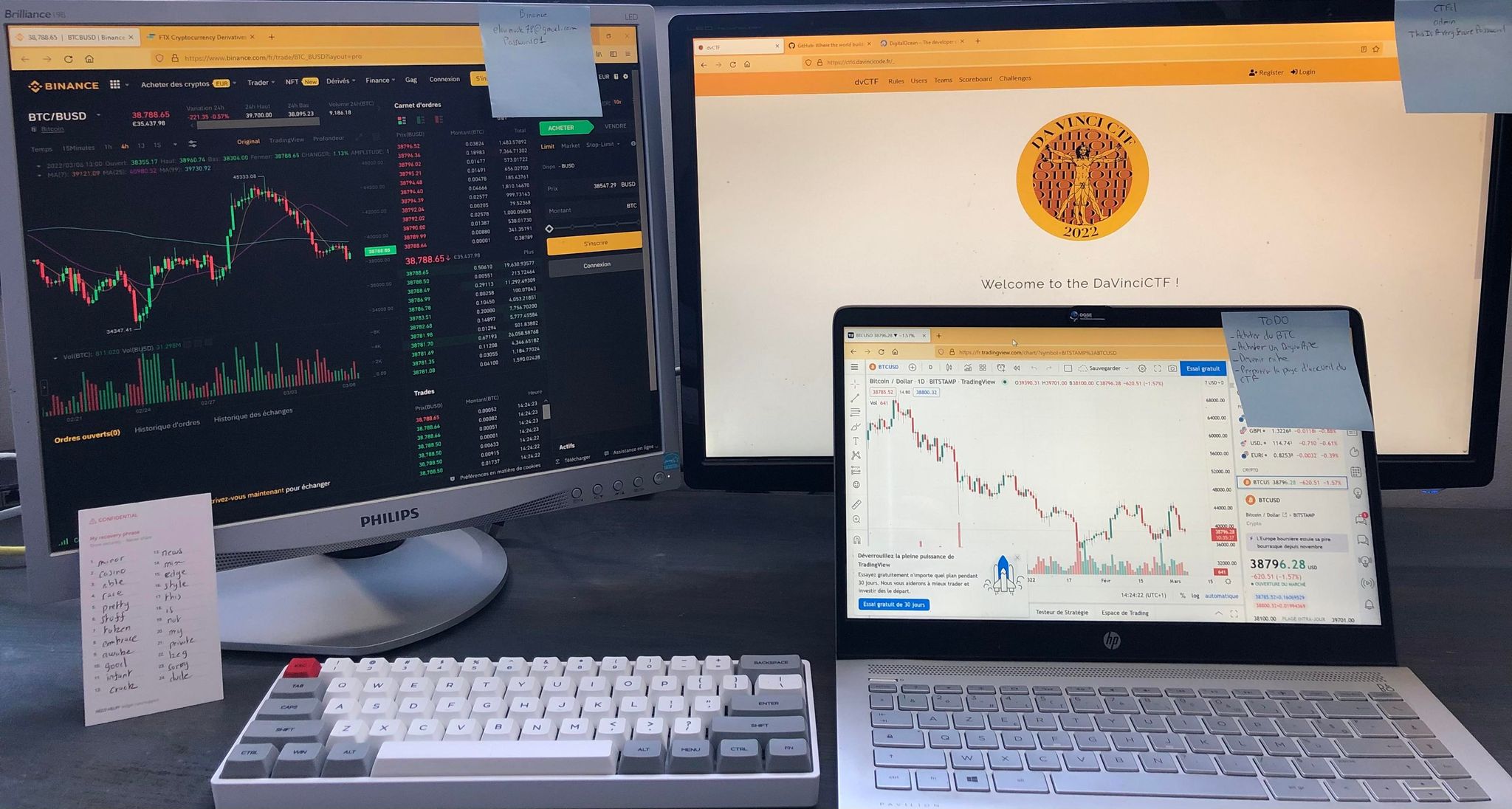
Welcome to the DaVinciCTF!
440 points 46 solves
Easy
Attachment: img.jpg
The challenge name suggests that the part with the DaVinciCTF page might contain the flag, with the URL https://ctfd.davincicode.fr/_ and login details Admin:ThisIsAVerySecurePassword shown in the image.

Thought that it might require logging into the platform, but apparently just have to search for dvctf{ or use ctrl-A to highlight all on the login page to reveal the flag in white colour near the bottom of the page.
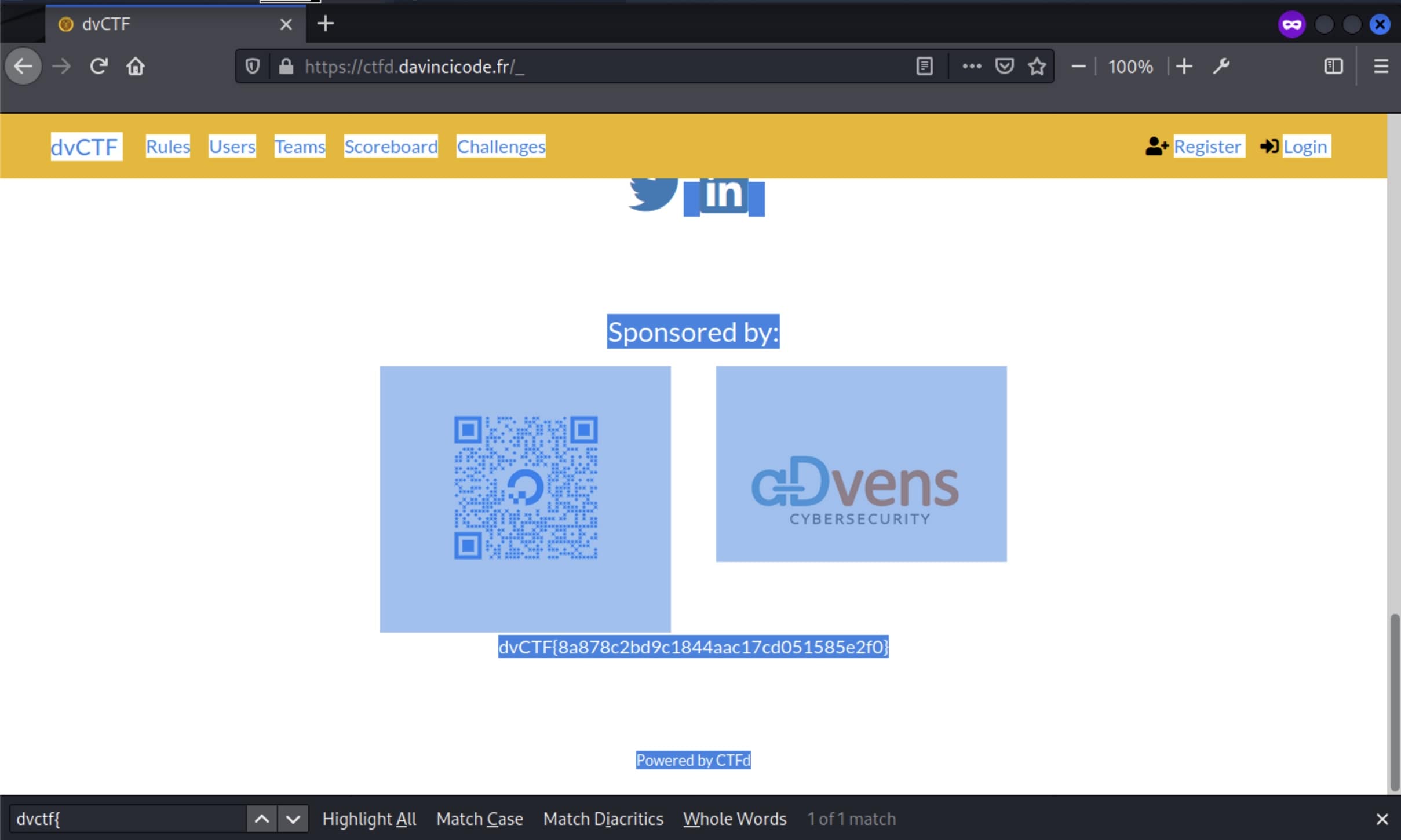
Flag: dvCTF{8a878c2bd9c1844aac17cd051585e2f0}
Painting Spot
426 points 51 solves
Found a nice painting spot, took a picture of it. But I can’t remember where it is… The flag is in the form of dvCTF{} and has the flag wrapper already
Attachment: paintingSpot.zip
Used exiftool to look for GPS information, not quite useful but instead, found some interesting information right beneath at the XP tags.
└─$ exiftool paintingSpot.jpg
ExifTool Version Number : 12.40
File Name : paintingSpot.jpg
...
GPS Altitude Ref : Above Sea Level
GPS Speed Ref : km/h
GPS Speed : 0.07419386512
GPS Img Direction Ref : True North
GPS Img Direction : 227.9959872
GPS Dest Bearing Ref : True North
GPS Dest Bearing : 227.9959872
GPS Horizontal Positioning Error: 6.047869715 m
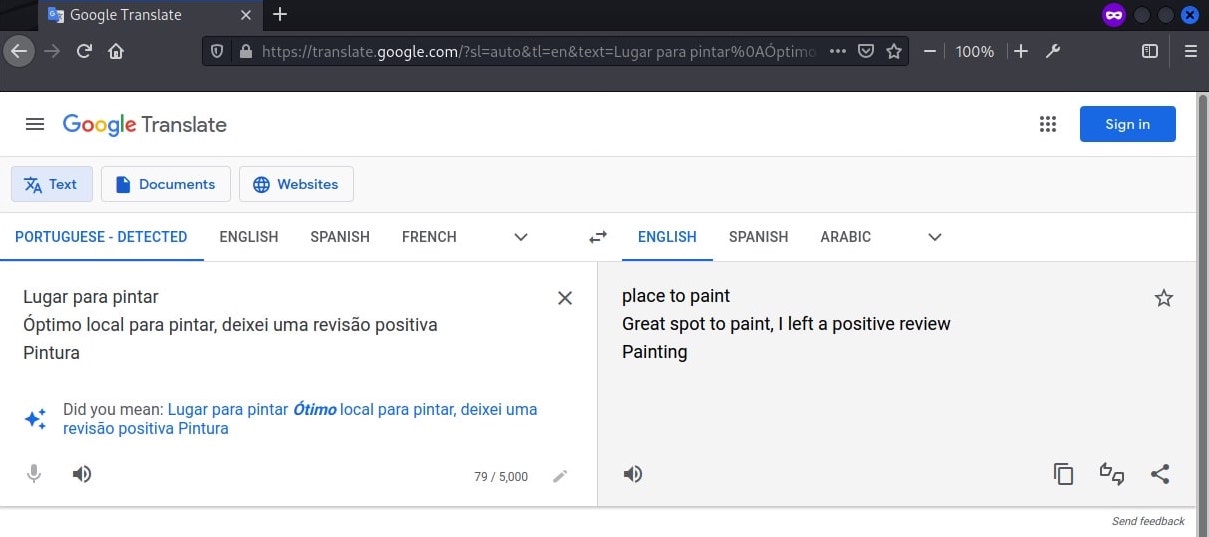
XP Title : Lugar para pintar
XP Comment : Óptimo local para pintar, deixei uma revisão positiva
XP Keywords : Pintura
...
Google translate detected that the comments are in Portuguese. It is likely that the place is in Portugal and the comment suggests that the flag might be in a review.
Uploaded the image to Google to search for similar images with the keyword “portugal” to narrow down the results.
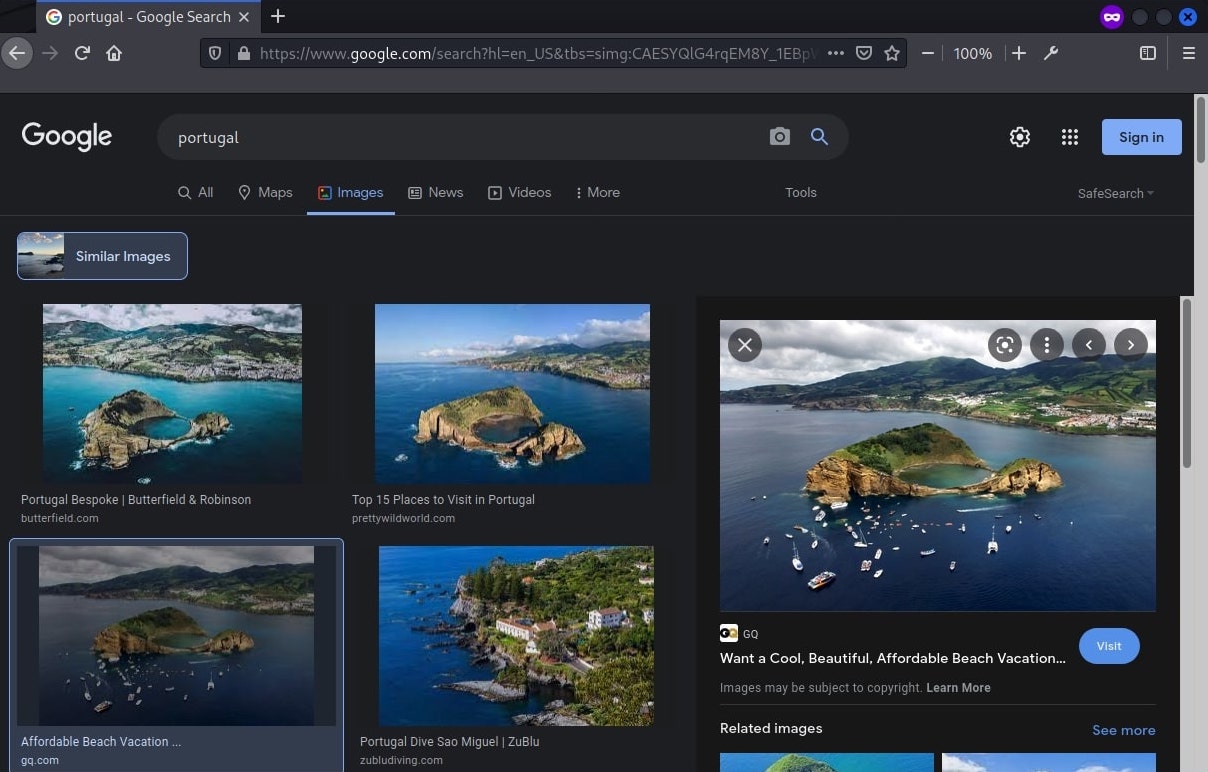
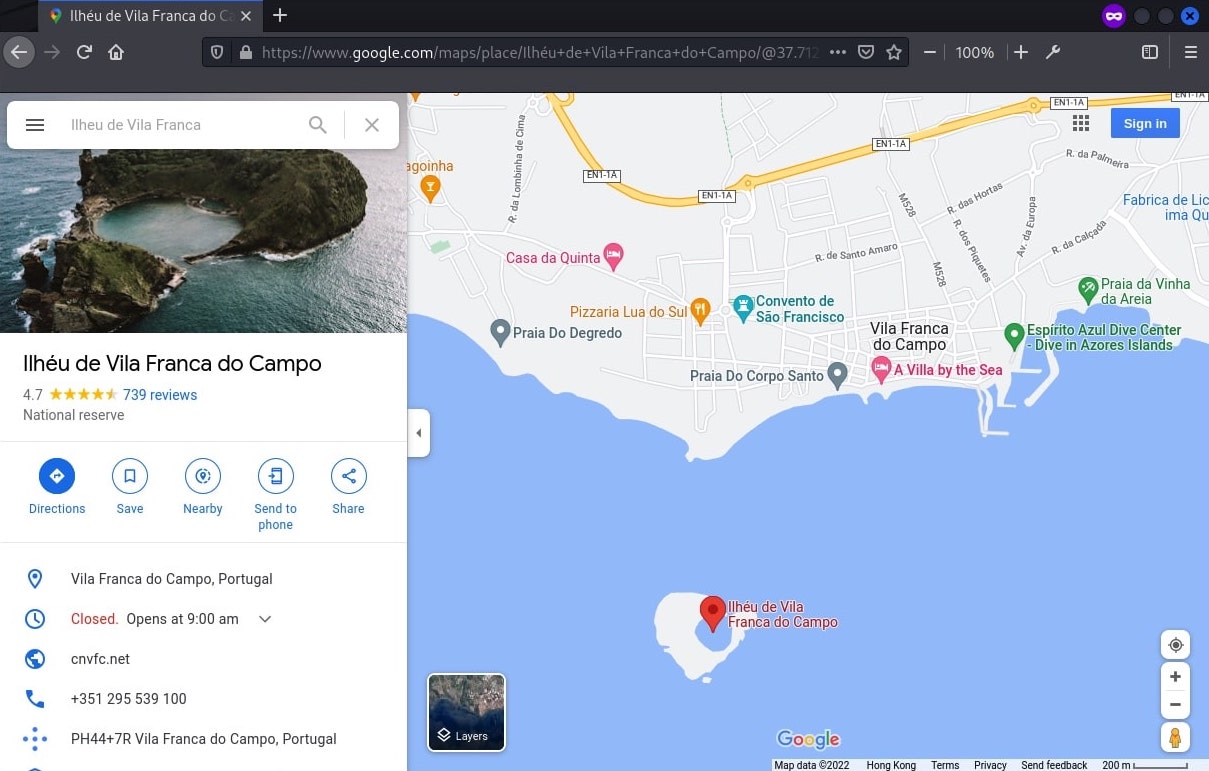
The top results were all pointing at the same location. Going to the website with the image and it described the place as “Best of the Azores: Ilhéu de Vila Franca”.
The place was located on Google map. From the picture provided, it should be taken somewhere on the right side on the map but not too far away from the island.
The beach “Praia do Corpo Santo” seems to best fit the angle. Sorted the reviews of the beach by newest and the flag was found.
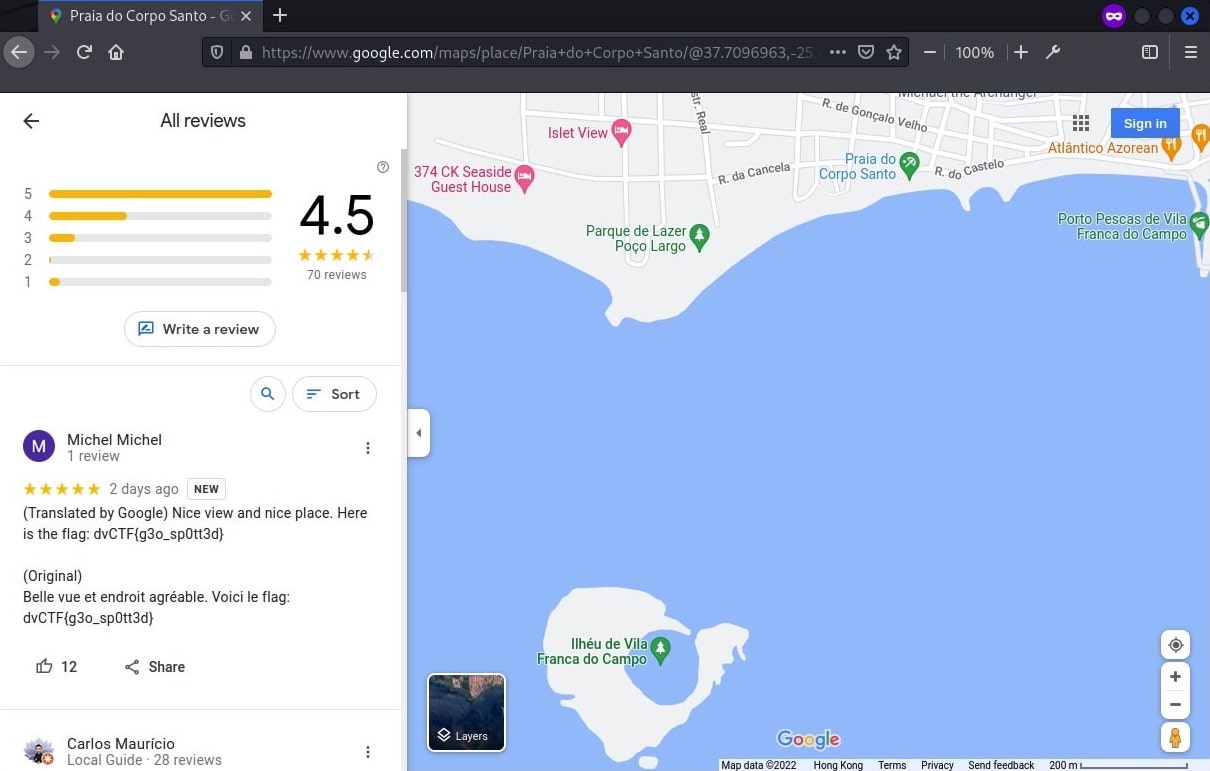
Flag: dvCTF{g3o_sp0tt3d}
Misc
The HackerMan
491 points 18 solves
EasyOSINTSteganography
I found someone on social media, teasing a CTF he made but I couldn’t find out more. I think his pseudonym was “BornHackerMan”.
Google search did not return any social media accounts, but searching the username within twitter returns an account.
One of the tweets suggested that the CTF is likely to be at Docker or GitHub.
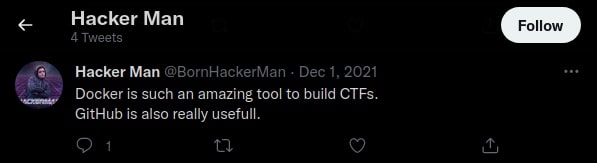
The other tweets looked normal, but for the video there were captions that has to be toggled on and it contained information.
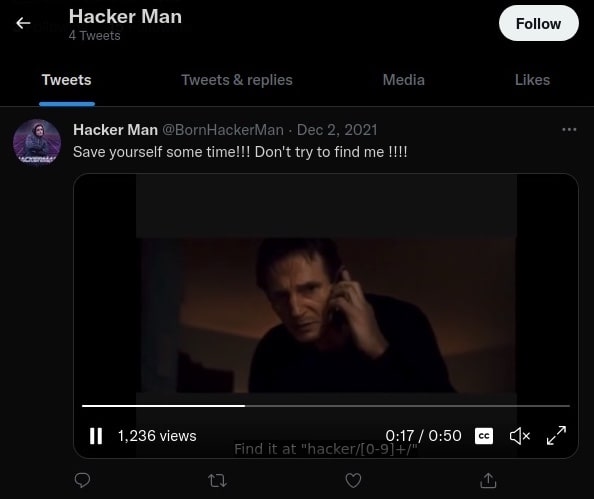
*Dailing*
*Ringing*
I finish my first CTF *hurray*
Find it at "hacker/[0-9]+/"
Signed: "The Hackerman"
Seems like the username associated with the CTF is with the regex hacker/[0-9]+/. A number is needed, and the dial tones from the beginning of the video could be DTMF tones. The dial tones were recorded as an audio file and uploaded to https://unframework.github.io/dtmf-detect/#/ to get it decoded as 4398884.
Since the original video had background noises, the decoder could not decode it perfectly as by ear you can hear that there should be 6 digits instead of 7 digits. Nevertheless, it helped to recognise most of the dials and the correct dial should be either 439884 or 439804.
The different combinations of the possible username were used to search for results on https://hub.docker.com/. At last, the user hacker439804 was found to have a container “myfirstctf”. (Apparently the / is not part of the regex, but acting as a wrapper of the regex).
Looking into the latest digest, the flag was found within one of the image layer commands.
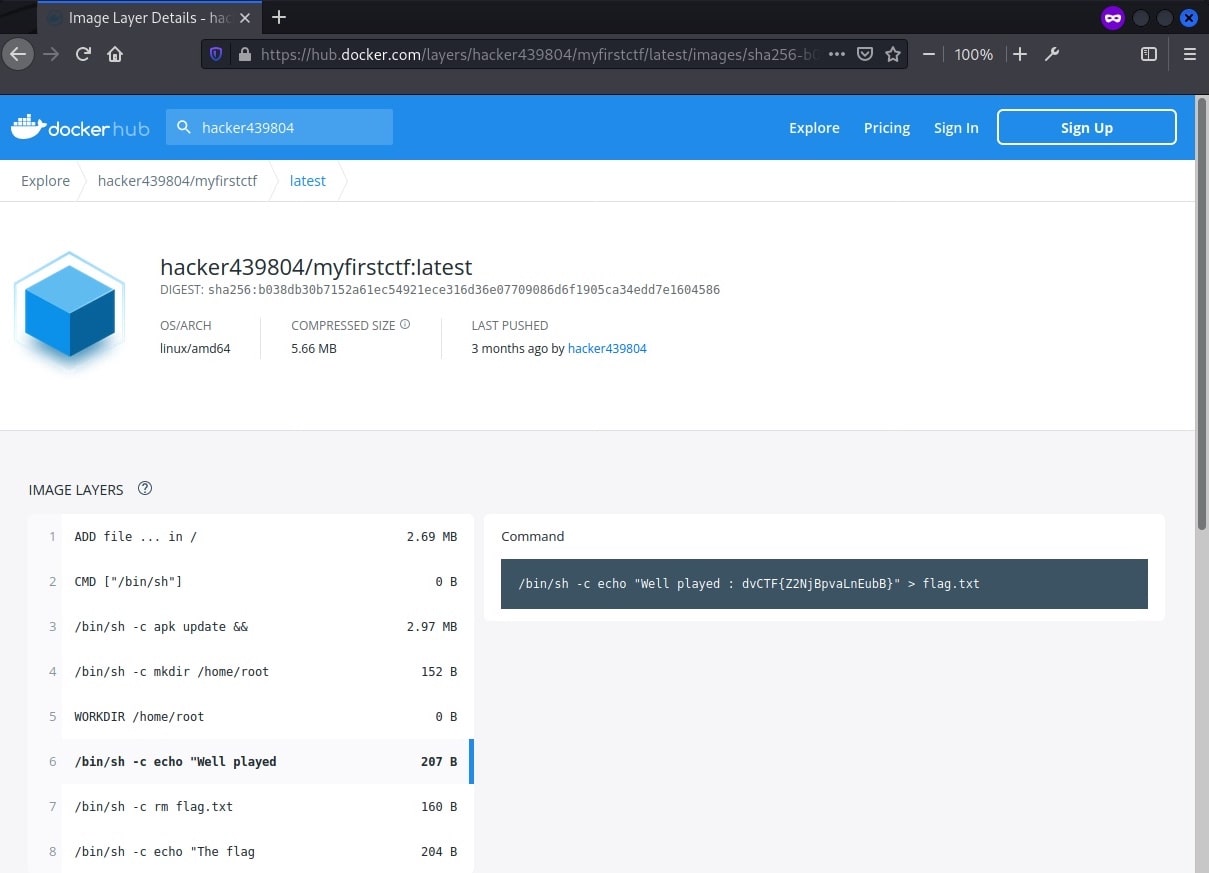
Flag: dvCTF{Z2NjBpvaLnEubB}
Going Postal
490 points 20 solves
MediumOSINTSteganography
My dear friend “Bob” made a tool online to uncover the truth behind that map.Attachment: map.jpg
Basic check with steghide reveals that there is a 7-zip file hidden in the image.
└─$ steghide info map.jpg
"map.jpg":
format: jpeg
capacity: 76.8 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "secretpwd.7z":
size: 758.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
└─$ steghide extract -sf map.jpg
Enter passphrase:
wrote extracted data to "secretpwd.7z".
└─$ 7z x secretpwd.7z
...
Extracting archive: secretpwd.7z
Enter password (will not be echoed):
ERROR: secretpwd.7z
Can not open encrypted archive. Wrong password?
...
A password is needed to extract the file, and it is likely to be the barcode on the image. Google searched for information with the keyword “australia post barcode” and found the 4-state barcode system used by Australian Post.
When searching for a decoder, the second result returned http://bobcodes.weebly.com/auspost.html which matches the challenge description.
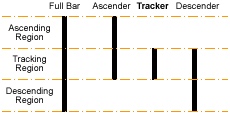
The barcode was manually translated into ATDFFDDADDAADAADFAFAFFDAFTFDAFATAFAAATADTAFDTDDDDDDDTTTDFFTDDADFAAT, as required by the decoder as the input. It was then fed into the decoder and decoded successfully.
Format Control Code: 62
Sorting Code: 78475110
Customer Information Field: V3K4N64r00
The information was consolidated into a wordlist to crack the file.
└─$ cat list.txt
62
78475110
V3K4N64r00
6278475110V3K4N64r00
62_78475110_V3K4N64r00
62-78475110-V3K4N64r00
v3k4n64r00
VEKANGAroo
VEKANGAROO
vekangaroo
└─$ /usr/share/john/7z2john.pl secretpwd.7z > 7z.txt
└─$ john --wordlist=list.txt 7z.txt
...
6278475110V3K4N64r00 (secretpwd.7z)
...
└─$ 7z x secretpwd.7z
...
Extracting archive: secretpwd.7z
Enter password (will not be echoed):
...
Everything is Ok
Folders: 41
Files: 0
Size: 0
Compressed: 758
The file was extracted successfully with the password 6278475110V3K4N64r00, containing 41 empty folders with binary names.
└─$ 7z l secretpwd.7z
...
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2021-09-30 23:01:11 D.... 0 0 secretpwd
2021-07-26 03:47:00 D.... 0 0 secretpwd/1013:0000000000000000000000000000000000000000
2021-07-25 22:03:00 D.... 0 0 secretpwd/1020:0011100000000110011111000111001000011100
2021-07-25 19:22:00 D.... 0 0 secretpwd/1044:0011011000111110011111011000110000010000
2021-07-25 15:32:00 D.... 0 0 secretpwd/1063:0011100001001111110010011001000111011100
2021-07-26 00:48:00 D.... 0 0 secretpwd/1115:0011000000110000011111100001000001100000
2021-07-25 13:01:00 D.... 0 0 secretpwd/1144:0011000111111001100011000001001001100000
2021-07-26 02:26:00 D.... 0 0 secretpwd/1154:0011000111001001100100111100110000011100
2021-07-25 16:22:00 D.... 0 0 secretpwd/1155:0011011111000111101101100011001110000000
2021-07-26 03:22:00 D.... 0 0 secretpwd/1189:0011111111111111111111111111111111111100
2021-07-25 07:25:00 D.... 0 0 secretpwd/1209:0000000000000000000000000000000000000000
2021-07-25 19:15:00 D.... 0 0 secretpwd/1221:0011011111111101111100100111000010011100
2021-07-25 09:56:00 D.... 0 0 secretpwd/1441:0011011000111001110000000111111001111000
2021-07-25 18:49:00 D.... 0 0 secretpwd/1441:0011011111111001111100100111000110011100
2021-07-26 02:02:00 D.... 0 0 secretpwd/1460:0011000111001001101100111110110000011100
2021-07-25 18:04:00 D.... 0 0 secretpwd/1507:0011111111000000011111100111000000000000
2021-07-25 11:41:00 D.... 0 0 secretpwd/1514:0011111110000110000000111111001000011100
2021-07-25 22:22:00 D.... 0 0 secretpwd/1532:0011000111111000010011100110000110011000
2021-07-25 13:57:00 D.... 0 0 secretpwd/1568:0011111111110000001100000000000111111100
2021-07-25 18:33:00 D.... 0 0 secretpwd/1600:0011111111000000011111100111000000000000
2021-07-25 16:10:00 D.... 0 0 secretpwd/1617:0011011111000111101100100001001110000000
2021-07-25 09:07:00 D.... 0 0 secretpwd/1648:0011011011001001001100100100010010111000
2021-07-26 02:46:00 D.... 0 0 secretpwd/1657:0011011110110000000011000000110110010000
2021-07-25 16:48:00 D.... 0 0 secretpwd/1657:0011100001111000011111100111110111101100
2021-07-25 11:10:00 D.... 0 0 secretpwd/1660:0011011000111001110000000111111001110000
2021-07-26 00:05:00 D.... 0 0 secretpwd/1668:0011100001110001110000000000110001111100
2021-07-25 07:08:00 D.... 0 0 secretpwd/1670:0000000000000000000000000000000000000000
2021-07-25 11:28:00 D.... 0 0 secretpwd/1722:0011111110000110000000111111001000011100
2021-07-25 21:50:00 D.... 0 0 secretpwd/1727:0011000001001000011100000110111000000000
2021-07-25 15:18:00 D.... 0 0 secretpwd/1730:0011011000110110000000011001001111100000
2021-07-25 13:35:00 D.... 0 0 secretpwd/1745:0011111111110000001100000000000111111100
2021-07-26 00:27:00 D.... 0 0 secretpwd/1746:0011000000110000111111100001000001100000
2021-07-26 05:13:00 D.... 0 0 secretpwd/1757:0000000000000000000000000000000000000000
2021-07-25 22:51:00 D.... 0 0 secretpwd/1789:0011000111111000010011100100000010010000
2021-07-26 03:08:00 D.... 0 0 secretpwd/1789:0011111111111111111111111111111111111100
2021-07-25 07:54:00 D.... 0 0 secretpwd/1838:0011011001001001101100100110110110010000
2021-07-25 09:38:00 D.... 0 0 secretpwd/1890:0011011110000110001100011000000001111100
2021-07-25 15:41:00 D.... 0 0 secretpwd/1904:0011100001001111110011011001000110011100
2021-07-25 21:28:00 D.... 0 0 secretpwd/1941:0011000001001000011100000110111000000000
2021-07-25 21:10:00 D.... 0 0 secretpwd/1956:0011011110111000001111011000001000011100
2021-07-25 19:44:00 D.... 0 0 secretpwd/1975:0011011100111100001111011000001000011100
------------------- ----- ------------ ------------ ------------------------
2021-09-30 23:01:11 0 0 0 files, 41 folders
The binary numbers were extracted and used to generate image (0 as white pixel and 1 as black pixel) using CyberChef.

The code looked a bit off that it seemed to be divided into four parts with white lines in between.
Apparently the number prefix of the folder name was a trap, the binary numbers should be sorted by the timestamp instead of the default sorting by the folder name. The listing information was imported into excel and sorted according to the timestamp. The binary numbers were extracted again in the correct order.
0000000000000000000000000000000000000000
0000000000000000000000000000000000000000
0011011001001001101100100110110110010000
0011011011001001001100100100010010111000
0011011110000110001100011000000001111100
0011011000111001110000000111111001111000
0011011000111001110000000111111001110000
0011111110000110000000111111001000011100
0011111110000110000000111111001000011100
0011000111111001100011000001001001100000
0011111111110000001100000000000111111100
0011111111110000001100000000000111111100
0011011000110110000000011001001111100000
0011100001001111110010011001000111011100
0011100001001111110011011001000110011100
0011011111000111101100100001001110000000
0011011111000111101101100011001110000000
0011100001111000011111100111110111101100
0011111111000000011111100111000000000000
0011111111000000011111100111000000000000
0011011111111001111100100111000110011100
0011011111111101111100100111000010011100
0011011000111110011111011000110000010000
0011011100111100001111011000001000011100
0011011110111000001111011000001000011100
0011000001001000011100000110111000000000
0011000001001000011100000110111000000000
0011100000000110011111000111001000011100
0011000111111000010011100110000110011000
0011000111111000010011100100000010010000
0011100001110001110000000000110001111100
0011000000110000111111100001000001100000
0011000000110000011111100001000001100000
0011000111001001101100111110110000011100
0011000111001001100100111100110000011100
0011011110110000000011000000110110010000
0011111111111111111111111111111111111100
0011111111111111111111111111111111111100
0000000000000000000000000000000000000000
0000000000000000000000000000000000000000
A new image was generated using CyberChef. The flag is then revealed when scanned as a data matrix code using https://products.aspose.app/barcode/recognize.

Flag: DVCTF{4U57r4114_P057_4_57473}


Comments